This topic will provide you with the hands-on skills required to conduct quality tests on hardware, run a variety of command-line tools and conduct risk analysis by running vulnerability assessments on a simulated network environment.
In this topic, you will learn how to:
- test hardware quality
- run command-line tools
- conduct risk analysis.
Let us begin.
Assessing hardware tools
Assessing hardware quality standards is crucial as it ensures reliability, performance, and longevity of devices. High-quality hardware reduces the risk of malfunctions, data loss, and security breaches, enhancing user experience and productivity. Adherence to standards guarantees compatibility, interoperability, and compliance with regulations, fostering trust among consumers and stakeholders.
Assessing hardware quality standards before security testing ensures reliable performance, minimising the risk of false positives or negatives due to hardware failures. It establishes a dependable foundation for accurate security assessments, enhancing the effectiveness and credibility of testing procedures while avoiding potential complications and inaccuracies.
Obtaining hardware equipment specifications
Obtaining hardware equipment specifications is vital to assess tool quality. It enables the understanding of capabilities, compatibility, and performance metrics crucial for effective use. Detailed specifications aid in identifying potential limitations, ensuring optimal selection, and maximising utility, thereby enhancing overall efficiency and reliability of hardware tools.
The following are examples of tools used to obtain hardware specifications from systems.
| System information tools | Software utilities such as CPU-Z, Speccy, or HWiNFO provide detailed information on CPU, GPU, memory, motherboard, and other hardware components. |
| Diagnostic tools | Tools like AIDA64 or SiSoftware Sandra perform comprehensive hardware diagnostics, revealing specifications and performance metrics. |
| Manufacturer utilities | Some hardware manufacturers offer proprietary software for monitoring and managing their devices, providing detailed specifications and performance data. |
| Command-line tools | Command-line utilities like PowerShell (Windows) or commands like lshw, hardinfo (Linux) offer detailed hardware information directly from the operating system. |
Running benchmark tests
Running benchmark tests is crucial to assess hardware quality as it provides objective performance metrics and comparisons against standards or competitors. Benchmarks identify strengths, weaknesses, and potential bottlenecks, guiding hardware selection and optimisation efforts. They ensure reliability, compatibility, and efficiency, facilitating informed decision-making and maximising the value and longevity of hardware investments.
System benchmark information can be obtained from websites such as, CPU-World, GPU-Review, or Ark.Intel, as they provide extensive databases of hardware specifications for various components.
Explore
How to Benchmark Your Linux System - Linux Tutorials - Learn Linux Configuration
Cross-Platform, Open-Source Automated Benchmarking Platform | OpenBenchmarking.org
Demo using ‘hardinfo’: A system information utility for Linux
The following video explains and demonstrates using the ‘hardinfo’ utility in a Linux system to obtain hardware information and run benchmark tests.
Practice activity 1
You have been provided with the recommended/minimum hardware specification of the Linux machine to be used to conduct security tests as follows.
- RAM/Memory: 2GB
- Processor: 32 or 64-bit CPU with a minimum 2 GHz of speed or better.
Do the following tasks in the ‘Kali Linux’ virtual machine in your simulated computing environment.
- Install the ‘hardinfo’ utility.
- Obtain processor, memory and network adaptor specifications using the ‘hardinfo’ utility. Note the key specification details.
- Evaluate whether the quality of the ‘Kali Linux’ machine’s hardware meets the required standard for conducting the required security tests. (Hint: Do this by comparing the minimum hardware specification provided.)
- Run the benchmark test ‘CryptoHash’. Examine the results from the benchmark test and note the key findings.

Network tools for problem solving
Using network tools for problem-solving is crucial for identifying and resolving issues efficiently. These tools offer insights into network performance, traffic patterns, connectivity problems, and security vulnerabilities.
For a network administrator, leveraging network tools is paramount for maintaining network health and addressing issues promptly. These tools allow them to monitor network performance, detect anomalies, troubleshoot connectivity problems, and mitigate security threats.
Windows networking tools
The following video will introduce you to Windows networking tools such as, ping, tracert and pathping.
Linux networking tools
The following video will introduce you to Linux networking tools such as, ifconfig, ping, ip route, traceroute, dig, nmap and netstat.
Gathering reported events
Gathering reported security events using Linux command-line tools is crucial for network administrators to maintain a secure environment. To do this efficiently, network administrators need to be familiar with the fundamentals of using Linux command-line tools.
Additionally, knowing how to capture and analyse information from data sources such as the Linux Firewall (i.e. iptables) provides insight into network traffic, allowing administrators to identify potential security breaches, unauthorised access attempts, or denial-of-service attacks.
Linux command-line fundamentals
Learning Linux command-line benefits network administrators by offering powerful tools for network management and troubleshooting. It enables efficient configuration, monitoring, and diagnosis of network issues. Familiarity with command-line utilities enhances productivity, flexibility, and adaptability, empowering administrators to effectively manage diverse network environments and address challenges with precision.
Linux iptables
iptables is a Linux firewall tool that filters network traffic. By configuring rules, it can log specific events, providing valuable threat data. iptables records information on connection attempts, helping analyse potential security threats. Monitoring these logs enhances threat detection, aiding in proactive responses to suspicious activities on the Linux system.
The following video demonstrates iptables in a Linux system.
Practice activitY
Complete the four (4) tasks in the following practice activity using the required tools in your virtual lab environment. The tasks in this activity will help you develop the practical skills required for the formal skills assessments in this module.
Task 1: Execute the correct command in the ‘Metasploitable’ virtual machine to enable firewall logging.
sudo iptables -A INPUT -j LOG --log-prefix “## iptables ##”
Task 2: Generate some traffic to and from the ‘Metasploitable’ virtual machine using a basic command line tool such as ‘ping’. You may ping the IP address of the Kali Linux VM from the Metaspoitable VM and visa versa to generate input and output traffic.
Task 3: View the /var/log/kern.log file in the ‘Metasploitable’ virtual machine using the correct command:
cat /var/log/kern.log | grep “## iptables ##”
Task 4: Examine the log file to interpret the meaning of the results. Make a list of the information that can be obtained from the results.
Task 5: Save the scan result into a file in CSV format and name it 'iptables-log.txt' using the correct command:
cat /var/log/kern.log | grep “## iptables ##” >> iptables-log.txt
Vulnerability scans
The following video demonstrates using some of the vulnerability scanning tools in a Kali Linux system (i.e. nmap, nikto and OpenVAS ) and explains how to interpret the results from these tools.
To learn more about port scanning read the article Metasploitable2 enumeration
Try it yourself: Conduct vulnerability scans
The tasks in the following practice activities will help you develop the practical skills required for the formal skills assessments in this module.
Practice activity 1
Complete the four (4) tasks in the following practice activity using the required tools in your virtual lab environment.
- Conduct a TCP port scan on the Metasploitable virtual machine in your virtual lab environment using the Nmap tool in Kali Linux.
- Experiment with different types and variations of TCP port scans using the available nmap command options.
- Save the scan results into a file in XML format and name it as ‘nmap-tcp.xml’.
- Examine the generated results and try to interpret the meaning. Make a list of the information that can be obtained from the results.
Practice activity 2
Complete the four (4) tasks in the following practice activity using the required tools in your virtual lab environment.
- Conduct a UDP port scan on the Metasploitable virtual machine in your virtual lab environment using the Nmap tool in Kali Linux.
- Experiment with different variations of UDP port scans using the available nmap command options.
- Save the scan results into a file in XML format and name it as ‘nmap-udp.xml’.
- Examine the generated results and try to interpret the meaning. Make a list of the information that can be obtained from the results.
Practice activity 3
Complete the four (4) tasks in the following practice activity using the required tools in your virtual lab environment.
- Find out the IP address of the owasp-juice.shop website using an appropriate command-line tool.
- Conduct a vulnerability scan on the owasp-juice.shop website using the Nikto tool in Kali Linux.
- Save the scan results into a file in CSV format and name it as ‘nikto-webscan.csv’.
- Examine the generated results and try to interpret the meaning. Make a list of the information that can be obtained from the results.
Scanning with ZAP
OWASP ZAP (Zed Attack Proxy) is a security tool for vulnerability scanning in web applications. It identifies and assesses potential weaknesses, such as SQL injection and cross-site scripting, by actively testing the application for vulnerabilities. ZAP helps developers and security professionals enhance the overall security posture of their web applications.
The following video provides a brief overview of the ZAP tool and what it can be used for.
Reading
Examples of alerts raised using the ZAP tool can be found at ZAP Alert Details (zaproxy.org). Refer to the OWASP Web Security Testing Guide | OWASP Foundation by OWASP Foundation
OWASP ZAP Demo
The following video demonstrates how to install and use the OWASP ZAP tool to conduct vulnerability scans.
OWASP ZAP (Zed Attack Proxy) is a security tool for vulnerability scanning in web applications. It identifies and assesses potential weaknesses, such as SQL injection and cross-site scripting, by actively testing the application for vulnerabilities. ZAP helps developers and security professionals enhance the overall security posture of their web applications.
The following video provides a brief overview of the ZAP tool and what it can be used for.
Practice activity 4
Complete the three (3) tasks in the following practice activity using the required tools in your virtual lab environment. The tasks in this activity will help you develop the practical skills required for the formal skills assessments in this module.
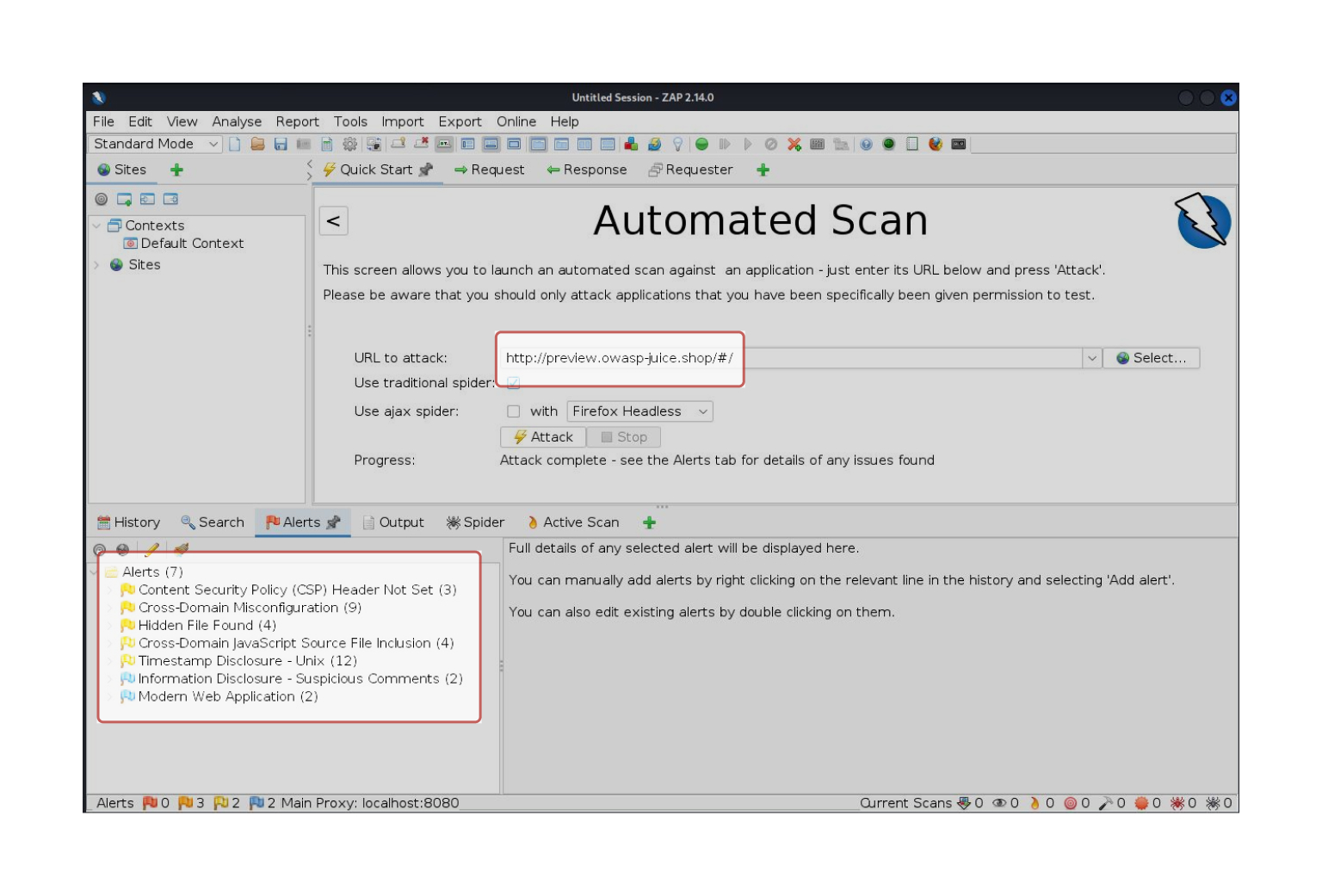
- Use the ZAP tool from the Kali Linux virtual machine in your virtual lab to conduct a vulnerability scan of the https://preview.owasp-juice.shop/#/ website.
- Investigate the types of alerts generated from the scan.
- Save the scan result into a file in CSV format and name it ‘ZAP-webscan.csv’.
The following screenshot demonstrates how the ZAP tool is used to conduct a vulnerability scan of the https://preview.owasp-juice.shop/#/ website and the scan results show eight (8) types of alerts.
How did you go?
Congratulations on completing the topic Apply network tools .
In this topic, you learnt about:
- conduct hardware quality tests
- run command-line tools
- conduct risk analysis.
Assessments
Now that you have learnt the basic knowledge and skills for this module, you are ready to complete the following assessment event.
Assessment 5 (Portfolio)
