Keeping your digital devices safe in the online world has never been more important, we show you how in this topic.
The internet as a vast public space. When you're in a public space you wouldn’t share your personal information like your home address, phone number, or bank details with strangers, so you would follow the same rules when you are on the internet.
Just like in the physical world, there are people on the internet who might want to take advantage of your personal information. They could use it for scams, identity theft, or other malicious activities. By keeping your data private, you can protect yourself from these dangers.
Use strong and unique passwords
Creating strong passwords is essential for protecting your online information, check out these tips below to help you when you are setting your passwords:
- Use a mix of characters
Combine upper-case letters, lower-case letters, numbers, and special characters (!, @, #, $, %). This makes the password more complex and much harder to guess. - Make a long password
Aim for a minimum of 12 characters or more. Longer passwords are generally more secure. - Avoid using information that is easy to guess and personal information
Do not use easily obtainable information like your name, birthdate, or common words as part of your password. - Don't use obvious patterns
Avoid using simple patterns like ‘12345,’ ‘abcd,’ or ‘password.’ These are among the first combinations attackers try as it is surprising how many people use these.
- Use passphrases
Consider using passphrases, which are long phrases or sentences that are easier to remember but still hard to crack.
For example, Beach$Waves*GoldenSand&Shells - Create unique passwords for each account
Never use the same password for multiple accounts. If one account is compromised, other accounts will also be easily hacked. This also includes simply adding numbers or symbols at the beginning or end of a word for each password. This is a common tactic and can be easily cracked.

- Consider using a reputable password manager
Consider using a password manager application. These tools can generate strong, unique passwords for each of your accounts and store them securely. Research carefully for a reputable password manger that uses strong encryption standards like AES (Advanced Encryption Standard) to protect your data. - Change your passwords regularly
Change your passwords regularly, especially for critical accounts like email and banking. - Do test your password strength
Some websites offer this feature when you're creating an account. They will let you know if you have created a weak or strong password.
Enable Two-Factor Authentication (2FA):
Two-Factor Authentication (2FA) for your important accounts, is like having two locks on your front door instead of just one to make it more secure.
How does it work:
- The password: The first ‘lock’ is usually something you know, which is your password. You input this like usual when logging in.
- Something physical: The second ‘lock’ is something you physically have, like your mobile phone. After you enter your password, the website or app sends a code to your phone. You will need to enter this code to finish logging in.
This makes your accounts much safer because it's much harder for someone to break in, even if they guess your password, they would also need to access your phone to be able to log into your account or app.
Phishing is pronounced like ‘fishing,’ and just like the sport of trying to catch fish, it's a cybercrime technique where scammers pretend to be trustworthy sources (like banks, email providers, or government agencies), to trick (catch) people into revealing sensitive information (like your usernames, passwords, credit card numbers, pin numbers or personal details).
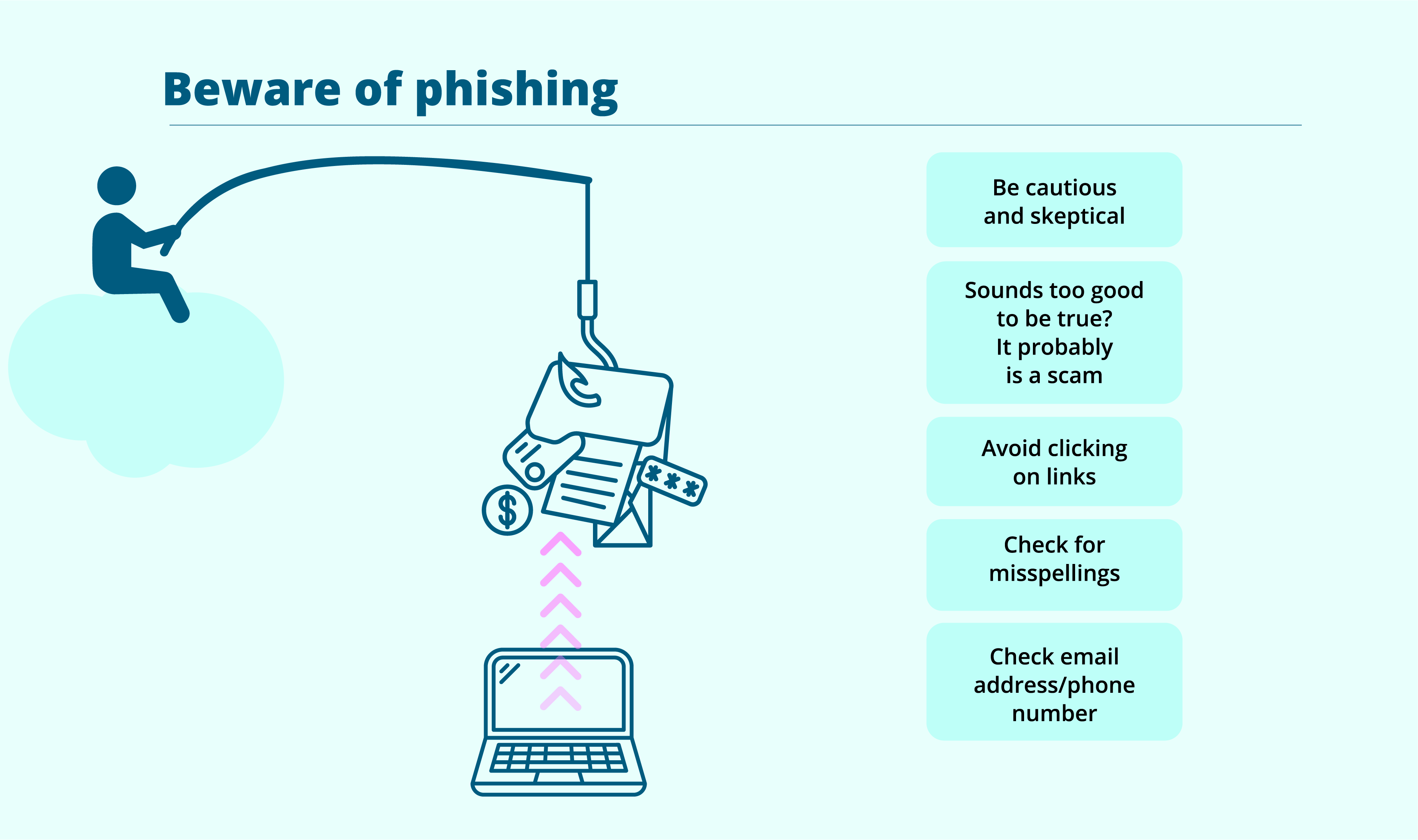
These scammers are ‘phishing’ for your private information, below are some important tips to make them unlucky phishers:
- Stay cautious and sceptical
We have all be targeted by online scams and fraud whether an email, phone call or a text.
Be very cautious of unsolicited emails, phone calls, or messages asking for personal information, money, or sensitive details.
Frequently scammers use urgency to solicit a response and their messages may induce a sense of panic in you to act urgently. If you are unsure, contact the organisation they say they are from independently to verify the information. - If something seems too good to be true...
It probably is a scam. Ask a trusted family member or friend to check the validity of the message if you are unsure. - Verify the email sender/phone number
Check the sender's email address or phone number. Legitimate organisations use their official web name, not generic ones.
If in doubt, look up the organisation they say they are from and contact them to check independently to check the validity of the email or phone call. - Avoid clicking on links
Instead of clicking on links in emails, manually type the web address of the website into your browser or use a trusted search engine to find it. - Check for misspellings
Phishers can't spell! Their emails often contain spelling and grammatical errors. If something doesn't look right, it might be a scam. - Never share sensitive/personal info
Never share sensitive information, such as passwords, PIN numbers, or credit card details, through email, text, or over the phone, especially if you didn't initiate the request. - Stay informed and up to date
It is important to keep software and operating systems on your devices up to date, use reputable antivirus software, and educate yourself about common online threats.
When you browse on the internet, there are important safety measures you can take to ensure your personal information is secure.
| Importance of HTTPS and secure connections |
HTTPS (Hypertext Transfer Protocol Secure). Websites that use HTTPS have an added layer of security, which is particularly important for websites that handle sensitive information like login credentials, financial data, or personal details. Most web browsers now display a padlock icon in the address bar to indicate that a website is using HTTPS. It's generally recommended to avoid entering sensitive information on websites that do not use HTTPS, especially for online shopping or financial transactions. |
|
Google ranking |
Google prioritises secure websites when it gives you search rankings. This means that websites using HTTPS are more likely to appear higher in search results. So if you search for something, these websites will show up first. |
| Web browser warnings | Some browsers like Chrome and Firefox display warnings when you visit websites without HTTPS, informing you that the connection is not secure. This helps users make informed decisions about sharing sensitive information. |
| Ensure your Wi-Fi network is secure | Ensure your home Wi-Fi network is secured with a strong password. An easily guessed and weak password makes it easy for someone to hack into and expose your data. |
| Avoid public computers for sensitive tasks | Computers that are available to the public, like in libraries or internet cafes, should be avoided for sensitive online tasks like online banking, as these computers may not be secure. |
| Avoid oversharing | Be cautious of oversharing personal information on social media (Facebook etc). Details like your home address or phone numbers should never be shared publicly. |
Privacy settings are controls and options that allow you to manage and customise the level of privacy you have when using digital services, devices, or online platforms. These settings enable you to decide how much of your personal information is shared, who can access your data, and how your data is used.
Privacy settings are essential for safeguarding your personal information and ensuring that you have control over how your data is used and shared in the digital world. It's a good practice to review and adjust these settings regularly to align with your privacy preferences.
Privacy settings in popular programs and platforms can vary widely, but here are some common settings you might encounter in widely used services.
Social media (e.g. Facebook, Instagram, Twitter):
| Profile privacy | You can often choose who can see your profile information, such as your posts, photos, and personal details. Options typically include ‘Public’ (everyone), ‘Friends’ (only people you've accepted as friends or followers), or custom settings. |
| Post visibility | You can control who can see your individual posts. This setting can be adjusted for each post, allowing you to share with the public, friends, specific groups, or only yourself. |
| Follower/Friend requests | Decide who can send you friend or follower requests. You can set it to ‘Everyone,’ ‘Friends of Friends,’ or ‘Only Me.’ |
| Location privacy | Some platforms allow you to disable location services or limit who can see your location. |
Email (e.g. Gmail, Outlook):
| Email encryption | You can enable encryption to secure the content of your emails during transmission. |
| Two-factor authentication (2FA) | Enhance your email security by requiring an additional verification step when signing in. |
| Advertising personalisation | Control how ads are personalised based on your email content or browsing history. |
Web browsers (e.g. Chrome, Firefox):
| Cookies | You can manage how websites use cookies to track your online activity. Options often include ‘Block all cookies,’ ‘Block third-party cookies,’ or ‘Accept cookies.’ |
| Privacy mode | Most browsers offer a private browsing mode that doesn't save your browsing history, cookies, or site data. |
Operating systems (e.g. Windows, macOS, Android, iOS):
| Privacy settings | These settings let you control which apps or services can access your location, camera, microphone, contacts, and other device features. |
| Privacy dashboard | Some operating systems provide a privacy dashboard or centre where you can review and adjust privacy settings at a glance. |
Smartphones and tablets:
| App permissions | Manage which apps can access your device's features like location, contacts, camera, and microphone. |
| Device lock | Set up screen locks (e.g., PIN, fingerprint, facial recognition) for added security. |
| Privacy controls | Review and adjust privacy settings for app tracking, ad personalisation, and location services in the device settings. |
To customise your privacy settings effectively, it's essential to explore the Settings menu within each specific program or platform and choose the options that align with your privacy preferences.
