Practice
Go to the Yoobee Build Sandbox in Practice Lab's and practice;
Implementing Physical Security
- Backup and Recovery Implementation
Explore
Explore Lesson 16 of the CompTIA A+ resource.Hardware Security and Attacks
In recent decades hardware attacks have become more common.
For example, in February 2014 the FBI charged Marc Heera with selling a cloned version of the Hondata s300, a plug-in module for the engine computer that reads data from sensors in Honda cars and automatically adjusts the air-fuel mixture, idle speed, and other factors to improve performance.
Invasion of the Hardware Snatchers: Cloned Electronics Pollute the Market - FICS Research (ufl.edu)
You can read about CERT NZ Recommendations for combatting similar scenarios in New Zealand. Note: CERT NZ is the organisation responsible for responding to cyber security threats in New Zealand.
The CERT NZ scenarios highlight the potential risks posed by hardware security vulnerabilities and the need for vigilance in securing critical military technology at nationwide levels.
What is IT Security?
The term security in computing refers to the practice of protecting electronic devices, networks, and sensitive information from unauthorised access, theft, damage, or other malicious attacks.
It involves a range of technologies, processes, and practices designed to safeguard digital assets and prevent cyber threats from compromising the confidentiality, integrity, and availability of data and systems.
From the above general description of security, we sort of have a general idea of :
- What we are protecting,
- What we are protecting against, and
- How we protect.
What are we Protecting?
Let's consider what is protected in IT security; primarily it is the organisation's digital assets such as Networks, Data, and Systems. Systems in this context mean Information Systems and their Users include both personnel and customers.
From a security point of view, any component of any Computing or Information System layer may have weaknesses that can generate vulnerabilities. A representation of an information system is in the diagram below:
The representation above shows a multi-layered view of a typical information system:
- At the top of all layers is the user, who interacts with the Information System.
- The highest layer under the user is the communication layer – this is where communication (the exchange of application data) with other systems is enabled through the networks (e.g., the internet) and web services.
- The application layer consists of the application software that performs specific tasks and processes information. For example, your text editor or word processing applications are captured here.
- In order to work, the applications need services provided by the system software (typically the Operating System, firmware, and device drivers), which in turn is the last virtualisation layer on top of the hardware.
- Hardware - At the heart or base of this abstraction is the hardware layer, consisting of the physical components of the information system. This layer supports all other layers by providing the necessary computational and storage capabilities. It stores and processes information. Information here is simply data representation (binary, audio, images, video, etc.) and they are housed inside the hardware.
The IMportance of the HARDWARE layer in security
An attack compromises a component in one of the system layers, the lower layer may either stop the intrusion or become compromised itself, allowing malicious use. Thus, hardware, as the foundational layer, plays a crucial role in information system security.
As the last line of defense against intrusions, the hardware is crucial because it supports all other layers. If the hardware is compromised, it can render all the defenses in the upper layers ineffective.
The presence of hardware vulnerabilities significantly impacts information system security. However, this is not the only role hardware plays in ensuring system security. Hardware also contributes to the overall security architecture by providing foundational support that all other layers rely upon.
From a security point of view, any component of any Information System layer may have weaknesses that can generate vulnerabilities.
What are we Protecting Against?
We can also infer what we are protecting our digital assets from or against from the security definition. Specifically, we are protecting our digital assets including network, data, information systems, and people against:
- Unauthorised Access - Preventing unauthorized individuals or systems from accessing sensitive data and systems.
- Theft - Guarding against the theft of data and digital assets.
- Damage - Protecting systems from damage caused by malware, hacking, and other forms of cyberattacks.
- Malicious Attacks - Defending against a wide range of cyber threats, including viruses, ransomware, phishing, and denial-of-service attacks.
In a nutshell, we are trying to protect our digital assets against exploitation and from their confidentiality, integrity, and availability being compromised.
How do we Protect?
To protect against unauthorised access, modification, theft, damage, and malicious attacks, security experts and system administrators employ a combination of technical, procedural, and administrative controls:
- Technical Controls: These are security measures implemented through technology. Examples include Implementing firewalls, encryption, antivirus software, intrusion detection systems, and secure access controls.
- Procedural Controls: These involve the processes, practices, policies, and procedures that govern security practices. Examples include: Security policies, incident response plans, and regular security training for employees.
- Establishing security protocols, regular system updates, and incident response plans. Practices like conducting regular security audits, training staff on cybersecurity best practices, and ensuring secure software development.
- Administrative Controls: These are the management-based measures that ensure security policies and procedures are followed. Examples include background checks, security clearances, segregation of duties, the principle of least privilege, and two-person integrity.
- Two-person Integrity: The two-person rule is a security strategy that requires a minimum of two people to be in an area together, making it impossible for a person to be in an area alone. The use of the two-person rule can help reduce insider threats to critical areas by requiring at least two individuals to be present at any time.
- Principle of Least Privilege: Ensuring that users and programs have the minimum permissions necessary to perform their tasks reduces the risk of accidental or malicious misuse of resources. Implementing the principle of least privilege helps limit the potential damage from compromised accounts or software vulnerabilities.
- Separation of Duties: By separating duties and requiring multiple users to complete sensitive tasks, access control helps prevent fraud and errors. This principle is essential in environments where high security is necessary, such as financial systems and critical infrastructure.
By combining these controls, security experts and system administrators create a multi-layered defense strategy that significantly enhances the security posture of an organization, reducing the risk of unauthorised access, breaches, and other security incidents.
The CIA Triad
We can also identify our desired security goals, which include safeguarding our digital assets and preventing cyber threats from compromising the:
- Confidentiality,
- Integrity, and
- Availability of data and system
The foundational concept that forms the basis of information security is the CIA Triad (not to be confused with the Central Intelligence Agency). This triad represents our core security objectives: confidentiality, integrity, and availability. These three elements are considered to be the most crucial elements of security:
- Confidentiality - granting access to assets only to those who are authorised,
- Integrity - maintaining assets unchanged between authorised accesses to them.
- Availability - ensuring access to assets when requested.
Watch - What is the cia triad (4:06 minutes)
Watch the video below to reinforce the importance of the three principles that will guide your security measures in the IT industry.
By understanding and implementing the principles of the CIA Triad, individuals and organisations can establish robust security measures to safeguard their data and systems from unauthorised access, tampering, and disruptions.
1. Confidentiality
Confidentiality refers to the protection of sensitive information from unauthorised disclosure. It ensures that only authorised individuals or entities have access to the data.
Confidentiality measures aim to prevent data breaches, unauthorised data access, and information leakage.
Techniques used to protect or enforce confidentiality include:
- Encryption
- Access control
- Data/Information classification
- Secure document storage and communication protocol
- Application of general security policies
- Education of information custodians and end users
- Confidentiality covers two related concepts:
- Data confidentiality: Assures that private or confidential information is not made available or disclosed to unauthorised individuals.
Confidentiality covers two related concepts:
Data Confidentiality: Ensures that private or sensitive information is not disclosed or made available to unauthorised individuals.
Privacy: Ensures that individuals have control over how information related to them is collected, stored, and shared, including by whom and to whom that information may be disclosed.
Privacy ensures that individuals control or influence what information related to them may be collected and stored and by whom and to whom that information may be disclosed. Information collected, used, and stored by an organisation is to be used only for the purposes stated to the data owner at the time it was collected.
Privacy as a characteristic of information does not signify freedom from observation. This means that when we talk about privacy in the context of information, it doesn't necessarily mean that the information is completely hidden or inaccessible. Instead, privacy refers to the control over how information is collected, used, shared, and protected. It means that information will be used only in ways known to the person providing it.
In other words, privacy involves ensuring that information is handled in ways that respect individuals' rights and expectations. This might include:
- Ensuring that personal data is only accessible to authorized individuals or entities.
- Implementing measures to protect information from unauthorized access and misuse.
- Providing individuals with the ability to control how their information is shared and used.
Thus, while information may be observed or accessed under certain conditions, privacy focuses on managing and protecting that information appropriately to safeguard individuals' rights and interests.
This link will clarify the distinction/grey area between confidentiality and privacy:
Understanding data confidentiality - data.govt.nz
2. Integrity
Integrity focuses on maintaining the accuracy, completeness, and reliability of data.
It ensures that information remains unaltered and consistent throughout its lifecycle. Integrity measures aim to prevent unauthorised modifications, data corruption, and tampering.
The data received is the same as it was sent (trustworthy and accurate).
Data integrity can be compromised at two critical stages in the transmission process: first, during the upload or transmission of data, where errors or unauthorised alterations may occur, and second, during the storage phase in databases or collections, where safeguards against corruption or unauthorised access are crucial.
Information integrity is threatened if exposed to:
- corruption,
- damage,
- destruction, or
- other disruption of its authentic state.
Techniques used to protect or enforce integrity include:
- Digital signature, Message Authentication Code, Message Digest, Hash functions, security policy, etc.
- File permission and user access control ensures unauthorised people cannot change data and checksum.
Integrity covers two related concepts:
- Data integrity: Assures that information and programs are changed only in a specified and authorised manner.
- System integrity: Assures that a system performs its intended function in an unimpaired manner, free from deliberate or inadvertent unauthorised manipulation of the system.
3. Availability
Availability refers to ensuring that authorised users have timely and uninterrupted access to the information and resources they require. It involves mitigating the impact of disruptions, system failures, or malicious attacks that can hinder access to data or services. For a system to demonstrate availability, it must have properly functioning computing systems, security controls, and communication channels. Systems defined as critical (power generation, medical equipment, safety systems) often have extreme requirements related to availability.
Critical System Requirements
These systems must:
- be resilient against cyber threats,
- have safeguards against power outages,
- have safeguards against hardware failures and other events that might impact the system availability.
Availability for critical systems is best ensured by rigorously maintaining all hardware and staying up to date with all system upgrades. Providing bandwidth, preventing bottlenecks, and providing disaster recovery are essential.
Techniques used to protect availability include:
- Availability measures prevent disruptions, downtime, or denial of service attacks that may render systems or data inaccessible.
- Strategies such as redundancy, fault tolerance, backup and recovery plans, disaster recovery, and robust infrastructure design are employed to ensure availability.
- Preventing DoS, DDoS, physical protection, access control.
Three key features of functional hardware security are Identification, Authentication, and Authorisation.
Identification
An information system possesses the characteristic of identification when it can recognize individual users. Identification and authentication are essential to establishing the level of access or authorization that an individual is granted.
Authentication
Authentication is the process of verifying the identity of a user or entity, ensuring that they are who they claim to be. It involves validating credentials such as usernames, passwords, biometric data, or digital certificates.
An authentication solution will establish the user's identity and grant them access to the system or resources based on their credentials. Once the user's identity is confirmed through authentication, authorization comes into play. Authentication occurs when a control proves that a user possesses the identity that he or she claims.
Authorisation
Authorisation determines what actions, privileges, or resources the authenticated user is allowed to access or perform within the system. It involves granting or denying permissions based on the user's authenticated identity and their assigned roles, permissions, or access control policies.
You may be asked which one occurs first between authentication and authorisation. In the context of access control in computer systems, authentication typically occurs before authorisation.
To summarise, authentication is the process of confirming the user's identity, while authorization is the process of granting or denying access based on the authenticated user's permissions. Therefore, authentication typically precedes authorisation in the sequence of access control.
Let's compare authorisation and authentication in the table below:
| Authentication | Authorisation |
|---|---|
| Confirms your identity to grant access to the system | Determines whether you are authorised to access the resources |
| Process of validating user credentials to gain user access | Process of verifying whether access is allowed or not |
| Determines whether user is what he claims to be | Determines what user can and cannot access |
| Usually requires a username and a password | Factors required for authorisation may vary depending on security level |
| The first step of authorisation so always comes first | Done after successful authentication |
| Example- students of a particular university are required to authenticate themselves before accessing the student link of the university's official website. | Example- authorisation determines exactly what information the students are authorised to access on the university website after successful authentication. |
The Role of Hardware in Information System Security
Cybersecurity experts have traditionally assumed that the hardware underlying information systems is secure and trusted. However, such an assumption is no longer true. Hardware cannot be considered the root of trust.
Hardware vulnerabilities clearly affect Information System security, but hardware's role in security goes beyond this. Generally, there are three roles that hardware plays in the security of our information systems:
Hardware-Based Security
This security role of hardware involves using hardware to protect the system from attacks that exploit vulnerabilities in other components.
Examples:
- Using a hardware firewall or Intrusion Detection System (IDS) to monitor and protect against network attacks that target software vulnerabilities.
- Trusted Platform Module (TPM): A hardware chip that securely stores cryptographic keys, passwords, and certificates, enhancing encryption and authentication security.
- Hardware Security Modules (HSM): Dedicated devices designed to manage and safeguard digital keys and perform cryptographic operations securely.
- Secure Boot and Firmware Integrity: Ensures that system firmware is not tampered with, and only trusted software is loaded during the boot process, typically through secure boot mechanisms and firmware verification.
Hardware Trust
This security role of hardware focuses on minimising risks from hardware counterfeiting, ensuring the authenticity of hardware devices used in the system.
Examples:
- Utilising hardware security modules (HSMs) that come with built-in mechanisms to verify and authenticate the origin of the hardware, ensuring it hasn't been tampered with or counterfeited.
- Tamper Resistance and Detection: Measures to prevent and detect unauthorized physical tampering with hardware, such as tamper-evident seals, secure casing, and alarms.
- Access Control: Limiting physical access to hardware components to authorized personnel only, using secure server rooms, locks, access cards, and biometric systems.
- Environmental Protection: Protecting hardware from environmental hazards like fire, water damage, and extreme temperatures with fire suppression systems, waterproof enclosures, and climate control systems.
What does hardware security entail?
Hardware Security refers to all the actions needed to:
- Identify hardware vulnerabilities i.e., detecting potential weaknesses in hardware components that could be exploited.
- Analyse the impact of the identified vulnerabilities on system functionality and security.
- Prevent the vulnerabilities exploitations by implementing strategies to mitigate, reduce, and ideally eliminate the risks posed by hardware vulnerabilities.
- Develop and implement protections and remediation solutions to protect hardware from potential threats and vulnerabilities. Included here are:
- Ensure security by design, that is, incorporating security measures during the design and production phases to avoid vulnerabilities from the outset, ensuring robust hardware security from the beginning.
Note that this definition is not limited by the location or timing of the actions described. While vulnerabilities may exist in hardware and attacks may target these weaknesses, defenses do not have to be at the hardware level. This would be impractical, as most vulnerabilities are found after the hardware is in use and cannot be easily patched. Therefore, any technique to counter hardware attacks is considered Hardware Security, even if applied at higher levels.
Hardware Vulnerabilities, Threats, Exploits and Attacks
To better understand hardware security, you need to have a clear understanding of what makes hardware vulnerable, what can exploit hardware vulnerabilities, what the threats are, and the risk and impact of successful exploitation of hardware vulnerabilities. Finally, you want to know how to prepare for and mitigate intrusions.
Hardware Threats
So, what are the threats to hardware?
Generally, a threat is any event or action that could adversely affect an information system, potentially compromising its confidentiality, integrity, or availability (CIA triad).
Threats can be natural (e.g., floods) or human-induced, ranging from inexperienced "script kiddies" to sophisticated hacker groups like Anonymous and Cozy Bear.
Threats can be intentional or accidental and originate from internal or external sources.
Watch - counterfeit electronics could be dangerous, funding nefarious people (3:33 minutes)
Watch the video below and identify the threats and how hardware security can troubleshoot vulnerabilities in everyday devices.
System on Chip (SoC)
SoC (System on Chip) refers to an integrated circuit that consolidates all components of a computer or other electronic system into a single chip.
SoCs include a central processing unit (CPU), memory, input/output ports, and secondary storage – all on a single substrate. They are widely used in mobile devices, embedded systems, and increasingly in IoT devices due to their compact size and efficiency.
The diagram below shows the System on Chip (SoC) Life Cycle and Associated Threats.
Threats can show up at different levels of the development of a SoC.
Countermeasures must be taken into account throughout the process.
System on Chip - Hardware Threats
There are various reasons why SoC are vulnerable:
- High Integration Complexity: SoCs integrate multiple components, making them complex. This complexity can hide hardware vulnerabilities that are difficult to detect and mitigate.
- Supply Chain Risks: The globalisation of SoC design and manufacturing means various stages are often outsourced. This opens opportunities for malicious entities to introduce hardware Trojans or other vulnerabilities during production.
- Surface Area for Attacks: Because SoCs combine many functions into one chip, the surface area for potential attacks increases. Attackers may target any part of the SoC, such as the CPU, GPU, memory, or peripheral interfaces.
SoCs can have diverse types of vulnerabilities, including:
- Design Flaws: Bugs or flaws introduced during the design phase. In the following diagram you can see the threats which exist in chip manufacturing:
- IP (intellectual properties) sometimes provided by third party vendors
- System integrator combines several IPs into a chip design
- Manufacturer fabricates the chips based on the received design
- Backdoors: Intentionally introduced vulnerabilities, often for debugging purposes, that can be exploited maliciously.
- Side-Channel Leakage: Unintentional emissions (like power consumption, electromagnetic radiation) that can be exploited to gain sensitive information.
SoC Impact on Security
Given their widespread use, vulnerabilities in SoCs can have severe security implications. As you can see in the diagrams above, hardware threats can show up at different levels of development of the System on Chip. A compromised SoC can affect the entire system, potentially leading to breaches in confidentiality, integrity, and availability of data and services.
Hardware vulnerabilities can be classified based on their nature and the domain they affect. The diagram below represents hardware vulnerability classification:
- Nature
Nature may be intentional or unintentional, i.e., the vulnerability may be introduced into the device voluntarily or not during its design and production phases.
Unintentional Vunerabilities:
These unintentional vulnerabilities are further split into:
- Bugs: A bug is an inconsistency between a specification and its actual implementation, introduced by a mistake during a specific design phase which is not detected during the subsequent validation and verification phase
- Flaws: “Flaw: A flaw is a non-primary feature that does not constitute an inconsistency with respect to the specifications. It arises from a misconception by the designer, who did not account for its potential dangers. Unlike a bug, a flaw does not conflict with any specification.
Intentional vulnerabilities
A vulnerability deliberately added can be referred to as a backdoor. This is done to allow subsequent unauthorised access or misuse. Note that the presence of a backdoor exposes the hardware component to threats, regardless of whether it was inserted for a malicious purpose or not. A non-malicious example is the undocumented instructions in processors (e.g., ALTINST opcode).
Malicious Examples:
- IP Piracy (Cloning IP)
- IC Piracy and Counterfeiting (Cloning and Overproduction)
- Hardware Trojans (rogue circuitry for unauthorised actions). Hardware Trojans are malicious circuits added during production. They have specific triggers and payloads, aiming to bypass security or cause harm. They can be introduced at various stages and levels of the hardware design process. They can change the functionality, reduce the reliability and leak valuable information.
Applications that are likely to be targets for attackers:
- Military applications
- Aerospace applications
- Civilian security-critical applications
- Financial applications
- Transportation Security
- IoT devices
- Commercial devices
The Domain
The domain hardware vulnerabilities affect can be either logical or physical:
- Logical Vulnerabilities - are introduced during early design phases.
- Physical Vulnerabilities – are introduced during technology-mapping steps of design process.
For example, a DRAM row hammering is a physical vulnerability where repeated access to memory cells causes neighboring cells to change state, demonstrating the risks of certain hardware technologies.
Other examples of physical vulnerabilities
- Processor vulnerabilities: Meltdown and Spectre. These vulnerabilities exploit flaws in modern processors to access sensitive data stored in the memory. They allow attackers to read information from other programs and the operating system. Such vulnerabilities were not born by a mistake made by the designer, but unintentionally introduced during the optimisation phase.
- Firmware Vulnerabilities: BIOS/UEFI Firmware: Vulnerabilities in BIOS or UEFI firmware can allow attackers to gain persistent and stealthy access to a system, potentially overriding security mechanisms and surviving OS reinstallation.
- Graphics Processing Units (GPUs): Certain GPUs are susceptible to Row hammer attacks, where repeated access to memory rows can cause bit flips in adjacent rows, potentially leading to data corruption or security breaches.
In security, vulnerabilities can be found in hardware, infrastructure, operating systems, firmware, applications, drivers, and APIs. Tens of thousands of software bugs are discovered annually, with details posted on websites like CVE and NVD, along with severity scores.
Responsible vendors release timely patches to fix these vulnerabilities. However, many high-profile attacks occur because organisations fail to apply these patches. A zero-day vulnerability is a newly discovered weakness without an existing patch.
Hardware Attacks
An attack is the act of exploiting or taking advantage of the vulnerability in the system for malicious purposes.
Exploiting a hardware vulnerability constitutes a hardware attack, which can only occur when the hardware is operational – For instance, modifying a design to introduce a backdoor is a vulnerability insertion while exploiting it is an attack.
A diagram showing the classification of hardware attacks is below:
A hardware attack can be classified into four groups:
Goal
The goal is the malicious action that the attacker wants to take against an asset of the attacked hardware (the target).
An attacker can launch an attack to:
- Steal a target (e.g., a cryptographic key, a secret password, an intellectual property, a resource, etc.).
Remember Confidentiality the CIA triad? Stealing is an action carried out in violation of confidentiality since the attacker takes possession of an asset to which she/he does not own the rights of access or use. - Corrupt a target (e.g., a memory word, a permission file, functionality to make it folded to one’s advantage, etc.).
Remember Integrity in the CIA triad? Corrupting is an action carried out in violation of Integrity since the attacker modifies an asset without being authorised to do it. - Inhibit a target (e.g., a service, a set of critical data, a defense mechanism, etc.). Remember Availability the CIA triad? Inhibiting is an action carried out in violation of Availability since the attacker prevents an asset from being properly accessed or used by those who hold the right to do that.
Target
The target can be the information that the hardware is housing, but also a component of the hardware itself.
Domain
Hardware attacks always have a domain in which they are implemented. The domain could be logical or physical.
Logical attack
An attack belongs to the logical domain if it is implemented starting from the upper layers concerning hardware. That is when a hardware vulnerability, logical or physical, is exploited through actions not directly on the hardware itself, but on the software, levels running on top of it. This domain includes privilege escalation attacks exploiting the row-hammer vulnerability or those that exploit vulnerabilities in processor microarchitectures like Meltdown, Spectre, and Cache-based attacks.
Physical attack
An attack belongs instead to the physical domain if it is implemented through actions directly performed on the attacked hardware device.
Modality
A hardware attack can be classified based on the modality in which it is carried out. An attack could be invasive or non-invasive.
Invasive Attack
An attack is invasive when the actions taken against the attacked hardware include physical intrusions such as desoldering, de-packaging, and disconnection of its internal component.
Some examples of Invasive Attacks:
- Micro probing: The attacker extracts information by measuring electrical quantities.
- Reverse Engineering: The attacker aims at understanding the structure of a semiconductor device and its functions, i.e., at stealing the intellectual properties of the designer. Deep knowledge and expertise in advanced IC design are obviously required to succeed.
- Data Remanence: The attacker recovers data from volatile memory after power-off.
Non-Invasive Attacks
Non-invasive attacks do not require physical intrusion and can be passive (observing physical clues) or active (inducing faults).
Passive attacks can manifest as side-channel attacks, which exploit physical clues such as timing information, power consumption, and electromagnetic radiation to extract sensitive data from a system.
Side-channel attacks exploit indirect physical information to compromise hardware security.
The most well-known classes of side-channel attacks are:
- Timing Attacks: Measure computation time to extract data.
- Power Attacks: Analyse power consumption to recover data.
- Electromagnetic Attacks: Capture EM radiation to reconstruct signals.
- Electromagnetic Leaks: Exploiting electromagnetic emissions from hardware to gather sensitive information without direct access to the system.
- Acoustic Attacks: Use sound emissions to infer information.
- Optical Attacks: Detect light emissions to steal data.
Active Attacks
Active attacks include fault attacks which induce faults to extract information. Fault attacks deliberately introduce errors into hardware to extract information or cause damage.
Types of fault attacks are mostly clustered according to the fault injection techniques. The most relevant are:
- Supply Attacks: Manipulate power supply to induce faults.
- Clock Attacks: Alter clock signals to corrupt data.
- Heating Attacks: Increase temperature to cause bit flipping or damage.
- Radiation Attacks: Use EM pulses to induce faults or destroy components.
Other Examples of Hardware Attacks
Physical Attacks such as Tampering: Physically accessing and tampering with hardware components, such as inserting hardware keyloggers or modifying circuits to create backdoors.
Supply Chain Attacks such as Infected Components: Introducing compromised hardware components during manufacturing or shipping, which can later be activated to perform malicious activities.
Firmware Malware such as Rootkits: Malware that infects firmware, such as UEFI rootkits.
Hardware Exploits
Exploit means or method of taking advantage of a vulnerability for malicious purposes. An exploit (noun) is a tool, often in the form of code, that leverages a vulnerability to grant unauthorized access to a system. As a verb, "exploit" means to take advantage of such a vulnerability.
Exploit code for many vulnerabilities is publicly available on sites like Exploit-DB and the dark web.
Organised groups and nation-state actors often develop their own exploit code. While exploit code is not available for every vulnerability, it is usually developed for those in widely used products with high attack potential, making the feasibility of threats more significant.
Some examples of Hardware Exploits:
- Row hammer Exploits - Tools that exploit the Rowhammer vulnerability to induce bit flips in memory, potentially allowing privilege escalation or code execution.
- Malicious USB Devices such as BadUSB: A type of exploit where a USB device is reprogrammed to act maliciously, such as emulating a keyboard to execute commands or spreading malware.
- Firmware Exploits such as Thunderstrike: An exploit targeting Apple's Thunderbolt firmware, allowing attackers to overwrite firmware and gain control over the system.
- Side-Channel Exploits such as Spectre/Meltdown Exploits: Proof-of-concept code that demonstrates how to exploit Spectre and Meltdown vulnerabilities to read sensitive data from memory.
Mitigating Hardware Attacks
Mitigating hardware attacks requires a multi-faceted approach that combines preventive measures, detection mechanisms, and responsive strategies.
General Mitigation Strategies
Let’s consider some general mitigation strategies for various hardware attacks categorized by their types:
1. Design-Level Security:
- Security by Design: Integrate security features during the hardware design phase. This includes secure boot mechanisms, encrypted firmware, and tamper-resistant design.
- Hardware Root of Trust: Implement a hardware root of trust (HRoT) to ensure that the boot process is secure and that the system starts in a known good state.
- Trusted Execution Environments (TEEs): Utilise TEEs to isolate sensitive operations from the rest of the system.
2. Access Control and Monitoring:
- Physical Security: Implement strong physical security controls such as secure facilities, tamper-evident seals, and restricted access to hardware.
- Access Logs and Monitoring: Continuously monitor and log access to critical hardware components. Implement anomaly detection systems to detect unauthorized access.
3. Software-Level Protection:
- Firmware Updates: Providing and applying regular firmware updates to patch vulnerabilities and improve security features.
- Code Obfuscation: Use code obfuscation techniques to make reverse engineering more difficult.
Specific Mitigation Strategies for Hardware Attacks
1. Micro probing Attacks
- Shielding: Use protective shielding around the chip to prevent physical probing.
- Mesh Sensors: Implement active shield meshes that detect probing attempts and can trigger tamper responses.
- Dummy Wires: Introduce dummy wires to confuse attackers attempting to probe the circuit.
2. Reverse Engineering Attacks
- Anti-Reverse Engineering Techniques: Use techniques such as obfuscation, secure memory encryption, and layout randomization to protect intellectual property.
- Chip-Level Encryption: Encrypt critical parts of the chip design to prevent reverse engineering.
3. Data Remanence Attacks
- Memory Scrubbing: Implement memory scrubbing techniques that periodically overwrite memory contents.
- Secure Erase Functions: Use secure erase functions to ensure data is completely wiped from memory devices.
- Environmental Controls: Ensure proper temperature control to prevent cold boot attacks.
4. Side-Channel Attacks
- Timing Attacks: Constant-Time Algorithms implements algorithms that execute in constant time to prevent attackers from inferring data based on execution time.
- Power Attacks: Noise Introduction introduces random noise into power consumption patterns to obscure useful information.
- Power Analysis Countermeasures: Use power balancing techniques and on-chip capacitors to smooth out power usage patterns.
- Electromagnetic Attacks: Shielding and Filtering uses electromagnetic shielding and filtering to reduce emissions.
- Acoustic Attacks: Noise Generators employ noise generators to mask acoustic emissions.
- Secure Enclosures: Use secure, sound-proof enclosures for sensitive hardware.
- Optical Attacks: Light Shielding applies light shielding techniques to prevent optical emissions from being captured.
- LED Activity Control: Ensure that LEDs do not emit data-revealing patterns.
5. Fault Attacks
- Supply Attacks: Voltage Monitors use voltage monitors to detect and respond to abnormal power supply conditions.
- Clock Attacks: Clock Signal Integrity implements integrity checks and redundancy in clock signals to prevent glitches.
- Heating Attacks: Temperature Sensors use temperature sensors to detect and respond to abnormal temperature increases.
- Thermal Management implements robust thermal management systems to maintain safe operating temperatures.
- Radiation Attacks: Radiation Shielding uses materials that shield the device from electromagnetic interference.
- Robust Design: Design circuits to tolerate transient faults induced by radiation.
6. Response and Recovery Strategies
- Incident Response Plan: Develop and regularly update an incident response plan specifically tailored for hardware attacks.
- Backup and Redundancy: Maintain regular backups and redundant systems to ensure continuity in the event of a hardware attack.
- Hardware Redundancy: Implementing redundant hardware components such as power supplies, hard drives (RAID configurations), and network interfaces to ensure system availability and reliability.
- Forensic Analysis: Implement forensic tools and processes to analyze hardware post-attack and identify vulnerabilities.
- Performance Optimisation: Using high-performance hardware to reduce the risk of bottlenecks and ensure that security processes (e.g., encryption and intrusion detection) do not degrade system performance.
7. Regular Maintenance and Upgrades:
Ensuring that hardware components are regularly maintained, updated, and replaced to prevent failures and security vulnerabilities, including firmware updates, patch management, and proactive replacement of aging components.
Hardware Vulnerability Summary
So far in this course we have looked at common enterprise hardware and the client-server relationship in an enterprise network. The diagram below illustrates the types of threats to the security of some of the infrastructure we discussed and the points over the network at which these threats are prevalent.
The diagram shows contemporary security challenges and vulnerabilities of computer systems.
You will notice that each of the components of an enterprise network has some vulnerabilities associated with it. Some problems occur at the client computer, others through the network lines, corporate servers, or in corporate hardware and software.
Each of these components presents security challenges and vulnerabilities. Floods, fires, power failures, and other electrical problems can cause disruptions at any point in the network.
As a sysadmin, you need to pay attention to each of the components and secure them. By addressing these areas, organizations can significantly enhance the security and resilience of their information systems, protecting against both physical and digital threats.
Let's test our understanding of some of the security concepts and vocabulary.
Look at the diagram below.
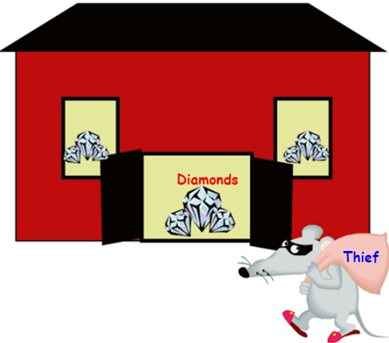
Can you identify:
- Threats
- Risks
- Vulnerabilities
- Exploits
- Assets?
Source: Lincke, S. (2015). Security planning. New York, NY: Springer International.

Defining Risk
Risk is the potential for loss, damage, or any other negative outcome resulting from a particular action, event, or decision. A risk arises when a threat exploits a vulnerability, resulting in an attack on a system or asset, potentially resulting in damage or loss. Running any enterprise involves inherent risks across various aspects, including hardware, personnel, manufacturing, and more. These risks can range from hardware failures and cybersecurity threats to hiring the wrong personnel or encountering manufacturing defects. Recognising and managing these risks is crucial for ensuring the organization's stability and success.
Before we jump right into how to identify hardware risks and manage them, there are two key points to understand:
No Vulnerability, No Risk.
If a vulnerability has no matching threat or a threat has no matching vulnerability, there is no risk. For example, if an organisation patches a software bug/vulnerability, the risk from that specific vulnerability is eliminated.
However, to protect yourself completely, you would have to avoid all vulnerabilities: never connect to the Internet or any network, turn off your wireless connection, and never load files from external sources. However, even with these measures, your computer is still at risk from physical access or manufacturing vulnerabilities (as we saw in the opening case of Hardware security).
Let's say you have a computer that is connected to the internet for various purposes like browsing, downloading files, or accessing online services. If this computer is not adequately protected with up-to-date antivirus software or firewalls, it is vulnerable to malware infections.
Now, if this infected computer is part of a network, either a home network or a corporate network, it poses a significant risk to other devices connected to the same network. The malware could spread through the network, infecting other computers, servers, or even IoT devices.
If you are unwilling to disconnect and isolate this infected hardware from all networks completely, you must accept the risk that the malware could spread further, potentially causing data breaches, system failures, or other damaging consequences.
Risk impact varies – The impact of risks can vary greatly depending on the context of the organisation.
For instance, a server going down in a kebab shop might lead to inconvenience for customers and loss of sales for the duration of the outage. However, in a banking business, the same server outage could result in severe financial losses, regulatory compliance issues, and damage to the institution's reputation. Understanding the specific impact of risks within the context of the organization is essential for effective risk management.
Remember, you can only minimise risks, not eliminate them.
Potential for Risk Always Exists
The potential for risk always exists because new exploit code can be developed for known vulnerabilities, and new vulnerabilities will be discovered. Attackers are constantly seeking new vulnerabilities to exploit.
Knowing your Organisation
To better understand the risk associated with your organisation, you need to know your assets, their value to your business, the impact of losing them, and how to avoid that.
Knowing your organisation in this context requires:
- identifying which information assets are valuable to the organization (critical to the organization's business process – they cannot do without these assets),
- categorising and classifying those assets, and
- understanding the impact of losing them and how they are currently being protected.
Knowing Your Enemy
Once your organisation becomes fully aware of itself – as in knowing its information assets and defensive posture, then the next step is to understand your enemy.
You will do this by identifying, examining, and understanding the threats and vulnerabilities facing the organisation’s information assets. This is what risk management is all about!
Risk Management is the process of identifying risks, assessing their magnitude (severity/impact), and taking steps to reduce them to an acceptable level.
To be able to assess and manage risk effectively, you must be able to answer the following key questions:
1. Risk identification process:
- Where is the risk to my information assets?
2. Risk assessment process:
- What assets and what risks exist?
- How severe is the risk to my organization’s information assets?
3. Understanding the organisation’s risk appetite:
- What does this risk cost?
- What asset should we prioritise?
- How much risk is acceptable to my organisation?
- Should we avoid the risk?
- Should we reduce it?
- Should we transfer to insurance?
- Should we just accept it and the consequences?
- What do we need to do to bring our current level of risk down to an acceptable level?
4. Understanding how to mitigate and control risk or risk treatment:
- What control is suitable to achieve the level of risk we can accept?
Let's address each of these questions one at a time and look at the steps and procedures required to answer them.
Identifying Risk
The first step to safeguarding your assets is to start by identifying the crucial elements that require protection. These assets span various categories: from IT components like databases and documents to hardware, software, and personnel. Additionally, non-IT assets such as buildings, equipment, products, supplies, personnel, cash, and reputation also need consideration.
The key is to distinguish between the vital assets—the invaluable treasures of your organisation—and less critical information and resources.
The process will follow as:
Identify important assets -> classify and categorize them into groups -> prioritise them based on their overall importance.
So, important questions to consider when identifying risk include:
- What is the value of this asset to our organisation or business?
- How much does this asset contribute to our revenue?
- How much would it cost to recover or replace this asset?
- What potential liabilities could we face if this asset were compromised?
Remember the CIA TRIAD – Each of these questions should be asked relative to confidentiality, integrity, and availability.
- Is the availability of this asset (e.g., web server) important for conducting business operations?
- Would a breach of confidentiality regarding this information render the organization liable under privacy laws?
- Could unauthorised tampering or manipulation of this hardware, impacting its integrity, lead to potential legal repercussions? OR
- Could unauthorised alteration of the information stored in the hardware, compromising its integrity, result in potential legal action?
The diagram below shows the process of steps to identify risk in an organisation:
The steps outline above to identify risk are:
- Creating an inventory of information assets.
- Classifying and organizing those assets meaningfully.
- Assigning Value to each information asset.
- Identifying threats to the assets
- Identifying asset’s vulnerabilities to specific threats.
Let’s look at a fictitious example of a risk table that identifies sample threats, vulnerabilities, and assets in an organisation like Yoobee Colleges Ltd:
| Asset Names | Threat | Vulnerability | Impact | Risk Level |
| Student Records | Data Breach | Weak Password Policies | Legal penalties, Reputation damage | High |
| Financial Data | Ransomware Attack | Outdated Security Software | Financial loss, Data unavailability | High |
| E-learning Platform | DDoS Attack | Insufficient Network Bandwidth | Service disruption, Learning delays | Medium |
| Faculty Devices | Phishing | Lack of Security Awareness Training | Data theft, Credential compromise | Medium |
| Campus Network | Malware Infection | Unpatched Software | Network downtime, Data loss | High |
| Registration Server | Unauthorised Access | Poor Access Control | Data manipulation, Service outage | High |
| Library Systems | Insider Threat | Inadequate User Monitoring | Data theft, System misuse | Medium |
| Research Data | Intellectual Property Theft | Lack of Encryption | Loss of proprietary information | High |
| Point-of-Sale Terminals | Payment Fraud | Outdated Payment Processing Systems | Financial loss, Legal issues | High |
| Building Security Systems | Physical Intrusion | Weak Physical Security Measures | Equipment theft, Unauthorised access | Medium |
The table above illustrates the classification of assets based on their criticality to the organisation’s business processes and the associated risk level, categorized as “High,” “Medium,” or “Low.” The table clearly maps specific threats and vulnerabilities associated with each asset.
We can also address this from a financial perspective and see the direct value of each asset, the cost of replacement, and the consequential financial loss if threats exploit the vulnerabilities and what happens to the CIA (confidentiality, integrity, and availability). Let’s look at the impact on CIA of the value loss in the table below:
| Asset Names | Value (NZD) Direct Loss |
Value (NZD) Consequential |
CIA Remarks |
|
Student Records |
$10,000 per student (tuition) | Forensic analysis and Investigation Costs: $100,000, Reputation: $500,000, Lawsuit: $500,000 |
e.g., Student records stolen and published on the dark web. Affects Confidentiality and Integrity. Forensic help would be needed to determine the breach's root cause. |
| Registration Server | $10,000 | Breach Notification Law: $500,000, Registration loss per day: $16,000, Forensic Help: $100,000 |
Affects: Confidentiality, Availability. Loss of registrations and Downtime. |
| Grades Server | $10,000 |
Lawsuit: $500,000 Forensic Help: $100,000 |
Reputation Affects: Confidentiality, Integrity. |
| Point of Sale Devices | $4,000 per unit | Payment Card Fines: $500,000 | Affects: Confidentiality, Integrity. Affects: Registration, Cafeteria, and Online sales handled by qualified service provider |
| Network Server | $5,000 per server | Replacement: $50,000, Downtime Costs: $10,000 per hour | Availability (e.g., minimizing downtime to maintain operations) Ensuring uninterrupted access to critical data and services is paramount for business continuity. |
| Data Storage Systems | $15,000 per system | Replacement: $30,000, Data Recovery Costs: $20,000 |
Integrity (e.g., ensuring data remains accurate and unaltered), Confidentiality (e.g., safeguarding sensitive information) Protecting data integrity and confidentiality is essential to prevent costly breaches and regulatory violations. |
| Access Control Systems | $5,000 per unit | Replacement: $10,000, Security Breach Costs: $50,000 | Confidentiality (e.g., restricting access to sensitive areas), Integrity (e.g., ensuring only authorized personnel can modify settings) |
The first column lists important assets. The second column shows the direct replacement value if an asset is compromised or destroyed. The fourth column details issues related to confidentiality, integrity, and availability. The third column includes the consequential costs, such as daily operational losses, lawsuit costs, regulatory fines, and reputation damage. To consider all costs, use the following equation (Lincke, 2015):
Tangible Costs = Cost of loss of integrity + Cost of loss of availability + Cost of loss of confidentiality
Note that the values in the table above were made up but are somewhat reasonable. Usually, you will rely on real data including data from the web, historical data from the organisation’s business processes, experience, and expert judgment to determine these values.
You can also ask simple questions to determine and assign values to your assets:
- Which asset is the most critical to the success of the organisation?
- Which asset generates the most revenue?
- Which asset generates the highest profit?
- Which asset is most expensive to replace?
- Which asset is most expensive to protect?
- Which asset’s loss or compromise would be the most embarrassing or cause the greatest liability?
Many organisations use asset inventory systems to keep track of their hardware, network, and software components. This could also be done with a precise manual or semi-automated process but could be overwhelming if a large quantity of data is needed to be collected.
How do you identify threats to your assets?
We have already discussed various threats associated with specific hardware or information assets -Remember the natural, intentional, and non-intentional classes of threats from the diagram?
Physical Threats
There are three types of physical threats; natural unintentional and intentional physical threats:
- Natural: Flood, fire, cyclones, hail/snow, plagues, and earthquakes.
- Unintentional: Fire, water damage, building collapse, loss of utility services, and equipment failure.
- Intentional: Fire, water damage, theft, and vandalism.
Non-physical Threats
Non-physical threats range from ethical to individual hackers:
- External Environmental: Industry competition, contract failure, changes in market conditions, political changes, regulatory changes, and technological changes.
- Internal Organisational: Management errors, IT complexity, poor risk evaluation, organizational immaturity, accidental data loss, mistakes, software defects, and personnel incompetence.
- Ethical/Criminal: Fraud, espionage, hacking, identity theft, malicious code, social engineering, vandalism, phishing, and denial of service.

Ethical/Criminal Threat Agents
For the ethical/criminal category possible threat agents include individuals who perform intentional threats, such as:
- Crackers
- Criminals
- Industry spies
- Insiders (e.g., fraudsters)
- Terrorists/hacktivists
Identifying threats to an information asset involves several steps:
- Asset Inventory: List and categorize all information assets (e.g., databases, documents, software systems).
- Understand the Asset's Value: Determine the importance of each asset to the organization. Consider the asset’s role in business processes, the sensitivity of the data, and regulatory requirements.
- Identify Potential Threats: Consider various threat sources, such as:
- Human: Insider threats (employees), external attackers (hackers), social engineering, human error.
- Technical: Malware, phishing, system failures, software vulnerabilities.
- Physical: Theft, natural disasters, hardware failures.
- Environmental: Fire, flood, power outages.
- Evaluate Vulnerabilities: Assess the weaknesses that could be exploited by the identified threats. This includes weak passwords, unpatched software, lack of encryption, insufficient access controls, etc.
- Analyse Historical Data: Look at past incidents, both within the organisation and industry-wide, to identify common threats and patterns.
- Consult with Experts: Engage with IT security professionals, conduct risk assessments, and use threat intelligence services to gain insights into current and emerging threats.
- Use Risk Assessment Tools: Utilise tools and frameworks like NIST, ISO/IEC 27001, and other risk management methodologies to systematically identify and evaluate threats.
- Regular Updates: Continuously monitor and update the threat identification process to adapt to new threats and changes in the organization’s environment.
By following the above steps, you can systematically identify and assess threats to your information assets, allowing you to implement effective security measures.
How do we identify vulnerabilities?
System vulnerabilities can be classified as follows:
| Behavioural | Misinterpretation | Coding | Physical vulnerabilities |
|---|---|---|---|
| Disgruntled employee, uncontrolled processes, poor network design, improperly configured equipment | Poorly-defined procedures, employee error, insufficient staff, inadequate management, inadequate compliance | Security ignorance, poorly-defined requirements, defective software, unprotected | Fire, flood, negligence, theft, kicked terminals, no redundancy |
Assessing Risks
Risk assessment (or risk analysis) involves the determination of the extent to which an organisation’s information assets are exposed to risk. Once the relevant vulnerabilities associated with each asset have been identified, we can then assess the risk based on:
- the likelihood (or probability) that a certain threat will exploit a specific vulnerability, and
- the impact, that is, the potential consequences or severity of the damage if the threat does occur.
- the current control applied to reduce or mitigate risk. For example, if you have a security manning your server room, the risk of physical damage or theft would be reduced. Hence, we have to consider existing control measures when assessing risk.
Risk Assessment Steps
Risk Assessment Steps from Risk Identification to Risk Appetite are shown in the following diagram:
Risk Assessment Estimate Factors
We can use a simple arithmetic model to simplify the above description – call it risk assessment estimate factors:
| RISK |
| = |
| The LIKELIHOOD that the threats to an asset will result in an adverse impact |
| X |
| The LEVEL OF IMPACT on the value of an asset as a result of a successful attack |
| – |
| The PERCENTAGE OF RISK MITIGATED by current control |
| + |
| The DEGREE OF UNCERTAINTY of current knowledge of the threat/asset environment |
How do we determine the Likelihood of a Threat Event?
Usually, this is all based on the probability that a threat will occur. We need to consider:
- What is the probability this threat will occur?
- What is the extent of the vulnerability?
In terms of vulnerabilities, some may be more easily exploited than others, and controls may fully or partially mitigate them. All of the factors of vulnerabilities could influence the probability that a threat would occur.
Although there are good estimates out there, there is no accurate forecast, with past experience perhaps being the best – if you have experienced a problem before. For example, how do you know if your laptop would be stolen (vulnerability) this year by a thief (threat)? Maybe if your laptop was stolen last year and the year before – then the probability is high.
A simple method of assessing risk likelihood is to score the event on a rating scale, similar to the one shown in the table below:
| Risk Likelihood | |||
| Rank | Description | Percent Likelihood | Example |
| 0 |
Not Applicable |
0% likely in the next 12 months | Will never happen |
| 1 |
Rare |
5% likely in the next 12 months | May happen once every 20 years |
| 2 |
Unlikely |
25% likely in the next 12 months | May happen once every 10 years |
| 3 |
Moderate |
50% likely in the next 12 months | May happen once every 5 years |
| 4 |
Likely |
75% likely in the next 12 months | May happen once every year |
| 5 |
Almost Certain |
100% likely in the next 12 months | May happen multiple times a year |
By using the scale in the table above the chance of a system being damaged by a water leak might be rated as 1, while the chance of getting at least one virus-infected email in the next year might be rated as 5. You could also use a different scale, like 1 to 10 or 1 to 100, depending on how detailed you need to be. Whatever scale you choose, make sure to use expert judgment and experience to assign ratings consistently.
Next let's look at examples of threats by industry and the likelihood of occurrences in the following table:
| 40% or Higher | 20-39% | 10-19% | 5-10% | |
| Accommodation | PoS Intrusion-75% | DoS-10% | Insider Misuse-8% | |
| Administrative | Misc. error-43% | Theft/Loss-12% | Web App Attack-8% | |
| Construction | Crimeware-33% |
Insider Misuse-13% Theft/Loss-13% Cyber Espionage-13% |
PoS Intrusion-7% Misc. Error-7% |
|
| Education | Misc. error-20% |
Web App Attack-19% Theft/Loss-15% |
Insider Misuse-8% Crimeware-6% |
|
| Entertainment |
DoS-32% Web App Attack-22% |
Misc. Error-12% Insider Misuse-10% |
PoS Intrusion-7% Theft/Loss-7% |
|
| Finance |
Web App Attack-27% Payment Card Skimmer-22% DoS-26% |
Insider Misuse-7% Misc. Error-5% |
||
| Healthcare | Theft/Loss-46% |
Insider Misuse-15% Misc. Error-12% |
PoS Intrusion-9% | |
| Information | Web App Attack-41% | Crimeware-31% | DoS-9% | |
| Management | DoS-44% |
Web App Attack-11% Payment Card Skimmer-11% Cyber Espionage-11% |
Insider Misuse-6% Theft/Loss-6% Misc. Error-6% |
|
| Transportation | Cyber-Espionage -24% | Web App Attack -14% |
Insider Misuse -9% Crimeware -8% |
|
| Manufacturing | Cyber-Espionage -24% | Web App Attack -14% |
Insider Misuse -9% Crimeware -8% |
|
| Retail |
DoS -33% PoS intrusion -31% |
Web-Attack -10% | Payment Card Skimmer-6% |
How do we determine the potential impact of an attack on an asset?
After listing important assets and likely threats, we have an estimate of the probability these threats will occur. Next, the organisation looks at the possible impact or consequences of a successful attack.
This is the level of harm that can be expected to result from the consequences of unauthorized disclosure of information, unauthorised modification of information, unauthorised destruction of information, or loss of information or information system availability (compromising CIA). One major concern is the loss of asset value.
The impact of an attack, often seen as a loss in asset value, helps determine where to focus protection efforts.
The tables used in risk identification can help understand the magnitude of a successful breach.
Another good source of information is media reports on successful attacks in other organisations.
Most commonly, organisations create multiple scenarios to better understand the potential impact of a successful attack.
The table below shows an example that highlights the potential impact of various risks, from minor interruptions with no data exposure to severe interruptions involving significant data breaches and financial loss.
| Rank | Description | Example | Number of records | Productivity hours lost | Financial impact |
| 0 | Not Applicable (N/A) | No impact | N/A | N/A | N/A |
| 1 | Insignificant | No interruption, no exposed data | 0 | 0 | $0 |
| 2 | Minor | Multi-minute interruption, no exposed data | 0 | 2 | $20,000 |
| 3 | Moderate | Multi-hour interruption, minor exposure of data | 499 | 4 | $175,000 |
| 4 | Major | One-day interruption, exposure of data | 5000 | 8 | 2,000,000 |
| 5 | Severe | Multi-day interruption, exposure of data | 50000 | 24 | 20,000,000 |
Risk Mitigation and Controls
During a risk assessment, whether for an existing information system or a new development project, it is common to find pre-existing controls that mitigate some of the identified risks.
These controls aim to reduce either the likelihood of an event occurring, its impact, or both.
We can generally classify the different types of controls into four types. Control can be:
- Deterrent control – this is a control intended to discourage people or potential attackers from deviant behavior. An example would be a policy of firing and/or prosecuting people for security violations or crimes, or a warning message on the log on screen.
- Preventive control – this is a control intended to minimise the likelihood of an incident occurring. For example, restricting server room access to authorized personnel, configuring appropriate rules on a firewall, or implementing an access control list on a file share.
- Detective control – this is a control intended to identify when an incident has occurred. For example, review of server or firewall security logs or Intrusion Detection System (IDS) alerts.
- Corrective Control – this is a control intended to fix information system components after an incident has occurred. For example, data backups, SQL transaction log shipping, or business continuity and disaster recovery plans.
Deterrent and Preventive controls are mostly used to reduce the likelihood of specific threats exploiting certain vulnerabilities.
Detective and Corrective controls are usually applied during or after impact (that is after a vulnerability has successfully exploited a threat) to correct the damage done or detect the incident.
Combining different layers of controls is the most effective risk management strategy. The diagram below illustrates the component of risk that each type of control reduces or discover:
Residual Risk After Treatment and Risk Appetite
Let's look at different ways of treating risk.
You have residual risk after applying the controls.
Although implementing additional mitigating controls is typically beyond the scope of the risk assessment process, identifying and selecting them is not. The business owner can choose to avoid, treat, transfer, or accept the risk.
Below are the different options for treating risk:
- Risk Avoidance: Stop the activity that would give rise to the risk, thus eliminating the risk. Risk avoidance is not commonly selected as it typically results in not being able to exploit the associated opportunity. Example: Do not use Social Security Numbers to avoid identity theft risks.
- Risk Mitigation: Implement controls to reduce the likelihood and/or impact of the risk eventuating. Risk mitigation is the most commonly selected risk management option. Example: Purchase and configure a firewall to minimize vulnerability to cyber attacks.
- Risk Transference: Transfer or share all or part of the impact of the risk eventuating with a third party like an insurance company. The most common risk transfer techniques are insurance and outsourcing. Note that while the financial impact can be transferred, legal responsibility cannot. Example: Buy malpractice insurance to transfer the financial impact of potential lawsuits.
- Risk Acceptance: The business owner may choose to accept a risk. Risks are usually accepted when they are assessed as being within the business’s defined risk tolerance level. However, they may also be accepted when it is not practical to avoid, treat, or transfer the risk. Example: Accept the risk of a comet hitting, as the exposure is negligible.
Residual Risk
After a risk management plan is complete, any risk that has not been covered by avoidance, mitigation, or transference is called residual risk.
If the residual risk is unacceptably high (as decided by management at the appropriate level – process owners or senior staff), you need to revisit the plan and improve your controls until the residual risk is at a level the organisation can live with, i.e., accept. This means the residual risk is not greater than the organisation’s risk appetite.
Acceptance should be considered when the cost of controls exceeds the probable cost of the risk eventuating. This shows how risk is reduced by risk treatment, resulting in the final residual risk.
Example of how to use Equation 1
Remember the equation for estimating risk below?
| RISK |
| = |
| The LIKELIHOOD that the threats to an asset will result in an adverse impact |
| X |
| The LEVEL OF IMPACT on the value of an asset as a result of a successful attack |
| – |
| The PERCENTAGE OF RISK MITIGATED by current control |
| + |
| The DEGREE OF UNCERTAINTY of current knowledge of the threat/asset environment |
Wrapping up
There are two key takeaways here:
1. Risk is the intersection where threat and vulnerability overlap. This means risk arises when a threat can exploit a vulnerability in an asset. Understanding and managing this overlap is crucial for effective risk management.
2. As IT engineers, our security objectives are to ensure that confidentiality, integrity, and availability of our resources are not compromised or are secured.
