To clearly understand the “what” and “why” of the components of an Operating System, let's revisit our computer system and its components.
We can see that without the software components such as Programs (Application and System Programs), Device Drivers, Libraries, and Operating systems, the computer hardware is effectively useless. These software components do not only control the hardware but also make it possible for users to interact with them. This means it would not have been possible for us to be able to do the everyday things we do on our systems like creating documents, modifying them, and saving them on our computer disk. Or complex tasks like running our Python, C++, Java, and so on programs.
Let’s look more into these layers in Figure 1 and discuss how they interact with operating systems.
Application Programs
These are user-oriented programs that perform specific tasks for the user. That is, they are software designed to help users perform specific tasks or activities.
These programs run on top of the operating system and rely on it to interact with the hardware.
Users interact directly with application programs through Graphical User Interfaces (GUIs) or Command-Line Interfaces (CLIs) - We will discuss more what GUIs and CLIs mean in later sections if you do not already know.
Examples of programs every time you work on your PC:
- Office Suites: Microsoft Office, LibreOffice.
- Web Browsers: Google Chrome, Mozilla Firefox.
- Media Players: VLC Media Player, Windows Media Player.
- Games: Any video game software.
- Productivity Tools: Project management software and note-taking applications.
System Programs
Watch - System Programs (12:11 minutes)
Watch the video and make notes about the categories of system programs: File Management, Status Information, File Modification, Programming language support, Program loading and execution, and Communications.
System programs (also called system utilities) are software tools designed to perform essential system-level tasks, such as managing hardware, optimizing performance, and supporting the operating system's functionality
- translating source code into machine code (e.g. compilers and assemblers).,
- manage files and directories (e.g., disk formatters, defragmenters)
- track system performance and resource usage (e.g., Task Manager in Windows, top command in Unix/Linux).
These programs are closely tied to the operating system and help manage the hardware and system resources. System programs provide an interface for users and applications to interact with operating system services. While users do not typically interact directly with all system programs, their actions, and applications can trigger system utilities. For example, when a user installs a new device, the corresponding device driver (a system program) is used to facilitate communication between the operating system and the hardware.
When a user or a user’s application triggers a system program to perform tasks (e.g., compiling a program or checking system performance), this program may make a request to the operating system for certain services. We will explain further how exactly this request is made later.
Some system programs run in the background, and you can view them using built-in tools in your operating system, such as the 'Defragment and Optimise Drives' tool in Windows for managing disk fragments or ‘Task Manager’ for monitoring processes, ‘Disk Utility’ in MacOS.
Categories of System Programs
System programs in a typical operating system are divided into six categories:
File Management Programs: Programs that create, delete, copy, rename, and print files.
Status Information: Programs that provide information about file size, creation time, hard drive space, and other system statuses. For example, you may want to find information about when a file was created, what the size of the file was, and what your hard drive space is. There are utilities usually built-in with your OS that could help you do this.
Command Line Interface (CLI): CLIs provide a text-based way for users to interact with the operating system by writing commands directly to perform various operations, such as file manipulation and system configuration.
File Modification: Text editors and other programs that:
- Create and modify files stored on disks or other storage devices.
- Search for files or transform files.
High-level Language Support: The OS provides programs such as compilers, assemblers, debuggers, and interpreters, which convert high-level programming languages into machine code that the hardware can execute.
Program Loading and Execution: Once a program is assembled and compiled, it must be loaded into memory for execution. The OS offers programs like linkers and loaders, which load program instructions into RAM and prepare them for execution by the CPU.
Communication: Programs that enable network communication, such as those implementing TCP/IP protocols, allowing computers to communicate over a network or the internet.
Device Drivers: Some device drivers also fall into this category, but we will talk more about them under the Hardware Abstraction Layer and run within the kernel. Device drivers act as intermediaries between the operating system and hardware devices, translating communication so that they can understand each other and work together efficiently.
Now that we have a basic understanding of how the first two layers above the operating system interact with it, let's take a closer look at the Operating System component itself.
Operating System and its Components
We will zoom into the Operating System layer and examine its internal structure in more detail. The diagram below shows how most operating systems architecture operate in two modes (user mode and kernel mode), with many different modules within both modes:
Internally, operating systems vary in their organisation, but there are many commonalities that we can explore. Understanding these common aspects helps us gain a comprehensive view of how operating systems function.
In the diagram, we can see some of the key elements of an Operating System. Including the kernel, the operating system services, the system call interface, and the hardware abstraction layer. We will discuss each of these components one after the other.
Each layer shown in the diagram hides the complexity of the layer below it and provides a set of abstract services to the layer above it.
For example, the computer's hard disk stores data in fixed-sized blocks. The operating system hides this complexity and provides the concept of files to the application software. An application, like a word processor, further abstracts this by allowing users to work with documents instead of files.
The operating system (OS) is the most critical of all the software components. It has three main tasks:
- Hardware Abstraction: The Operating System shields the details of the hardware from application programs, and thus from the users. Instead of interacting directly with hardware, application programs interact with the Operating System, which provides a standardized interface to the hardware. This abstraction allows applications to run on different hardware configurations without needing to be rewritten for each type of hardware.
- Abstract Services: Operating System provides abstract services to replace physical hardware services. These services translate into real hardware operations, allowing users and applications to interact with devices through a standardised interface, regardless of the specific hardware.
- Resource Management (Resource Allocator): Because the resources in a computer (CPU, memory, disk space) are limited, we need a resource manager that will protect the computer resources from misuse. Operating System does this. It manages the computer’s resources, optimising their use and protecting them against misuse and abuse. When a system provides multiuser or multitasking capabilities, resources must be allocated fairly and equitably amongst a number of competing requests.
The Kernel
The kernel is a computer program at the core of a computer's operating system and is the primary interface between software programs and the hardware of a computer. The kernel manages system resources, such as the CPU, memory, and devices, ensuring everything works together smoothly and efficiently.
Watch - What is a kernel and what does it do? (7:04 minutes)
This video explores the kernels of Linux, Windows, and MacOS and the various layers that interact with a kernel to make it work. Kernels are used throughout all operating systems and are the driving engine for your operating system.
We can say kernel is the “engine” of the operating system responsible for critical tasks such as interfacing with hardware devices, managing system resources and making them available for users and programs, initializing essential components, and more.
Software running within the kernel operates with direct access to hardware resources, making it extremely sensitive. For instance, when you install hardware drivers, because they operate within the kernel space of the operating systems. This means, the drivers run or execute with privileged access to system resources and have direct interaction with hardware components.
The kernel allocates and balances the sharing of these resources among the programs within the user space. (We will discuss user space in a moment but for now, just note that it is the space in within the computer system memory where the user’s programmes run. The vast majority of programmes run in ‘user space’).
It is named a 'kernel' because it operates inside the Operating System, just like a seed inside a hard shell.

More precisely, the term 'kernel' draws its analogy from the edible part of a nut or seed which is encased within a protective shell. In a walnut, for example, the kernel represents the soft interior surrounded by the hard shell. This metaphor effectively illustrates the structural role of the kernel within a computer system. Before we look at other components of the Operating systems, you will also notice that the kernel mode, and the user mode is loosely broken down into two parts: What do we mean by this?
Kernel Mode and User Mode
Operating systems operate in two modes: the kernel mode and user mode. Remember that we mentioned earlier that some programs, particularly application programmes and users, are restricted from directly interacting with the computer’s hardware.
The computer's CPU provides two modes of operation which enforce the protection needed to achieve this. As an operating system must hide the computer's hardware, and manage the hardware resources, it needs to prevent the application software from accessing the hardware directly. Without this sort of protection, the operating system would not be able to do its job (remember the three main tasks of OS discussed earlier?). Hence, in an operating system, user mode and kernel mode are two distinct execution environments that provide different levels of privilege and access to system resources.
When we run any application, we are in user mode, but as you know, all the resources can be controlled or accessed through Kernel. So, when a user program needs to access hardware (CPU, RAM, Hard Disk or I/O devices, etc.), it makes a system call and goes into kernel mode.
Example: When you open an Excel sheet, the application runs in user mode. If you update some data on the sheet and want to save these changes to the hard disk, the application (MS Excel) makes a system call to the kernel. The system switches to kernel mode to handle the request. The kernel manages the actual writing of data to the hard disk. Once the save operation is complete, the system returns to user mode, and Excel continues running.
Similarly, when you want to display text on the monitor (e.g., using System.out.println() or echo or print ()), the request goes to the kernel through a system call. The system switches to kernel mode to handle the display operation, and the kernel manages the output to the monitor. After completing the task, the system returns to user mode.
The operating system runs in kernel mode, also known as supervisor mode or privileged mode. In kernel mode, the software has complete access to all of the computer's hardware and can control the switching between the CPU modes.
The User Mode
The User mode has the following characteristics:
- Limited Privileges: Programmes running in user mode have restricted access to system resources. They cannot directly interact with hardware or critical system data.
- Isolation: User mode processes are isolated from each other and from the kernel. This isolation ensures that if a user mode process crashes, it does not affect the stability of the system.
- When a program in user mode needs to perform operations that require higher privileges (like accessing hardware), it makes a request to the operating system’s kernel for relevant services (this request is called a system call).
- Safety: Running programs in user mode enhances the overall security and stability of the system, as it limits the potential damage from bugs or malicious actions.
The Kernel Mode
The Kernel mode has the following characteristics:
- Full Privileges: In kernel mode, the operating system has unrestricted access to all hardware and system resources. It can execute any CPU instruction and reference any memory address.
- Critical Operations: The kernel handles critical tasks such as managing hardware devices, memory, and processes. It ensures the smooth operation and coordination of the entire system.
- Direct Access: Programs running in kernel mode can directly interact with hardware, manage system memory, and perform other low-level operations that user mode programs cannot.
- System Calls Handling: The kernel processes system calls made by user mode programs, performing the requested operations and returning the results to the user mode programs.
System Calls
Now, let us further explore the components of the Operating system, and see how users, programmers, and operating system designers view Operating systems. In the operating system diagram above we can see that the System Call interface layer is between the programs and the kernel.
Watch - System Calls (12:39 minutes)
Watch the video about system calls in an operating system and how the user mode and kernel mode interact.
Users do not interact directly with system calls. Instead, when an application program needs to perform a task that requires OS services (such as reading a file or creating a process), it makes system calls. These system calls are handled by the kernel.
Recall the example from the system programs section: When a user or an application uses a system program to perform tasks like compiling a program or checking system performance, the system program may request services from the operating system. This request is called a system call, which is the interface between the system programs and the operating system's kernel. The kernel, which manages essential services such as process scheduling, memory management, and I/O operations, handles these requests.
When a program needs to perform a task requiring higher privileges (e.g., accessing hardware or saving a file), it makes a system call. Remember, when you open a Microsoft Excel sheet , the application runs in user mode. If you update some data on the sheet and want to save these changes to the hard disk, the application (MS Excel) makes a system call to the kernel. The system switches to kernel mode to handle the request. The kernel manages the actual writing of data to the hard disk. Once the save operation is complete, the system returns to user mode, and Excel continues running.
Similarly, when you want to display text on the monitor (e.g., using System.out.println() or echo or print() ), the request goes to the kernel through a system call. The system switches to kernel mode to handle the display operation, and the kernel manages the output to the monitor. After completing the task, the system returns to user mode. For example:
- User Mode: Applications like MS Excel and game programs run with limited privileges, handling most of their tasks in the user mode.
- System Call: When an application needs to perform a task requiring higher privileges (e.g., accessing hardware or saving a file), it makes a system call.
- Kernel Mode: The system switches to kernel mode to execute the requested operation with full privileges, ensuring safe and controlled access to hardware and system resources.
- Return to User Mode: After completing the operation, control returns to user mode, allowing the application to continue its tasks.
Categories of System Calls
Since a user needs to access many resources, the types of system calls depend on the type of resource or service they manage.
In a general-purpose operating system, there are typically hundreds or even thousands of system calls. For instance, Windows 10 includes over two thousand different system calls. However, we can categorise system calls into six common groups:
- Process Control
- File Manipulation
- Device Manipulation
- Information Maintenance
- Communication
- Protection
Process Control: These system calls manage processes, allowing for tasks such as process creation, termination, execution
Examples include:
- fork(): Creates a new child process.
- (Windows Equivalent: CreateProcess())
- exit(): Terminates a process.
- (Windows Equivalent: ExitProcess())
- kill(): Abnormally terminates a process.
- (Windows Equivalent: TerminateProcess())
Other process controls include: load, wait, allocate and free memory and control.
File Management: These calls handle file operations, including creating, deleting, opening, closing, reading, and writing files.
Examples in UNIX Operating systems include:
- create(): Creates a new file.
- ( Windows Equivalent: CreateFile() with the CREATE_NEW flag.)
- open(): Opens an existing file.
- (Windows Equivalent: WriteFile())
- write(): Writes data to a file.
- (Windows Equivalent: WriteFile())
- mkdir(): Creates a new directory.
- Windows Equivalent: CreateDirectory()
I/O devices Management: The I/O devices management system calls are used to control the devices and allows the users to read and write the data from devices.
Examples in UNIX OS include:
- ioctl(): Controls device-specific operations. Windows Equivalent: DeviceIoControl()
- read(): Reads data from a device., write(): Writes data to a device.
- Windows Equivalent: ReadFile() and WriteFile()
Information Maintenance: These system calls retrieve and set information about processes, files, and devices. If we need to get information about the devices or processes, then we use information-related system calls
Examples include:
- getpid( ): To find the id of the process (metadata of the file size, permission and types etc.)
- Windows Equivalent: GetCurrentProcessId()
- stat(): Provides file metadata such as size, permissions, and type.
- Windows Equivalent: GetFileAttributesEx() or GetFileInformationByHandle()
- settimeofday(): Sets the system date and time.
- Windows Equivalent: SetSystemTime()
Communication: The communication related system calls are used to create and delete the communication and forward/receive messages.
Examples include:
- socket(): Creates a communication endpoint.
- Windows Equivalent: WSASocket() or socket()
- send(): Sends a message.
- recv(): Receives a message.
- Windows Equivalent: send() and recv() in Winsock API.
Protection: These system calls manage permissions and access controls for resources, ensuring secure operations. Examples include:
- chmod(): Sets file permissions.
- Windows Equivalent: SetFileSecurity()
- chown(): Changes file ownership.
- Windows Equivalent: SetSecurityInfo()
setuid(): Sets user ID for a process
Examples of Windows and Unix system calls
| Windows | Unix | |
|---|---|---|
| Process control | CreateProcess () ExitProcess() WaitForSingleObject() |
fork() exit() wait() |
| File manipulation | CreateFile() ReadFile() WriteFile() CloseHandle() |
open() read() write() close() |
| Device manipulation | SetConsoleMode() ReadConsole() WriteConsole() |
ioctl() read() write() |
| Information maintenance | GetCurrentID() SetTimer() Sleep() |
getpid() alarm() sleep() |
| Communication | CreatePipe() CreateFileMapping() MapViewOfFile() |
pipe() shmget() mmap() |
| Protection | SetFileSecurity() InitialiseSecurityDescriptor() SetSecurityDescriptorGroup() |
chmod() umask() chown() |
Source: https://www.cs.uic.edu/~jbell/CourseNotes/OperatingSystems/2_Structures.html
Types of Kernels
There are different types of kernels. Each type of kernel has its own strengths and trade-offs. The choice of kernel architecture depends on the specific requirements of the operating system, such as performance, security, stability, and ease of development.
Understanding these different types of kernels helps in designing and choosing the right operating system for a given application or environment
Monolithic Kernel
In a monolithic kernel, all operating system services run in kernel space. This means the kernel provides a wide range of services such as device management, file system management, and system call handling, all within a single large kernel binary.
Examples of Monolithic Kernel:
Linux, Unix, BSD variants (FreeBSD, OpenBSD, NetBSD).
Advantages of Monolithic Kernel:
- High performance due to direct communication between services. Monolithic kernels are generally faster than other types of kernels because they don’t have to switch between user and kernel modes for every system call, which can cause overhead.
- Monolithic kernel operating system services run in kernel space, allowing efficient communication and easier implementation of complex functionalities and optimizations.
- Monolithic kernels are simpler to design, implement, and debug due to their unified structure.
Disadvantages of Monolithic Kernel:
- Stability Issues: Monolithic kernels can be less stable than other types of kernels because any bug or security vulnerability in a kernel service can affect the entire system.
- Security Vulnerabilities: Since all the operating system services are running in kernel space, any security vulnerability in one of the services can compromise the entire system. A bug in one service can potentially crash the entire system.
- Maintenance Difficulties: Monolithic kernels can be more difficult to maintain than other types of kernels because any change in one of the services can affect the entire system.
- Limited Modularity: Monolithic kernels are less modular than other types of kernels because all the operating system services are tightly integrated into the kernel space. This makes it harder to add or remove functionality without affecting the entire system.
Microkernel
A microkernel architecture separates the basic kernel functions (such as process management and inter-process communication) from higher-level services (like device drivers, and file systems) which run in user space. Only the most essential services run in kernel space.
The basic idea behind micro kernels is to remove all non-essential services from the kernel, and implement them as system applications instead, thereby making the kernel as small and efficient as possible.
Examples of Microkernel:
Minix, QNX, L4, Mach, AmigaOS,, K42, etc.
Advantages of Microkernel:
- Improved System Stability and Security: Faults in user space services do not crash the entire system, enhancing overall stability and security.
- Reliability: Microkernel architecture is designed to be more reliable than monolithic kernels. Since most operating system services run outside the kernel space, bugs or security vulnerabilities in a service are less likely to affect the entire system.
- Flexibility: This architecture allows for greater flexibility, as different operating system services can be added or removed without impacting the whole system.
- Modularity: The microkernel's modular design means each operating system service runs independently. This independence simplifies maintenance and debugging.
- Portability: With most services running outside the kernel space, microkernels are more easily portable to different hardware architectures.
Disadvantages of Microkernel:
- Performance: Microkernels can be slower than monolithic kernels due to the increased number of context switches between user space and kernel space.
- Complexity: The architecture can be more complex because it requires more communication and synchronization between various operating system services.
- Development Difficulty: Developing microkernel-based systems can be more challenging than monolithic systems, as it demands careful design of communication and synchronization mechanisms.
- Higher Resource Usage: Microkernels may consume more system resources, such as memory and CPU, due to the overhead associated with additional communication and synchronisation.
Hybrid Kernel
A hybrid kernel combines elements of both monolithic and microkernels. It runs some services in kernel space for performance reasons while others run in user space for stability.
Examples Of Hybrid Kernel
Windows NT, macOS (XNU kernel).
Advantages of Microkernel:
- Performance: Hybrid kernels can offer better performance compared to microkernels, as they reduce the number of context switches required between user space and kernel space.
- Reliability: By isolating drivers and other kernel components in separate protection domains, hybrid kernels can provide better reliability than monolithic kernels.
- Flexibility: Hybrid kernels allow for greater flexibility, as they enable the addition or removal of different operating system services without affecting the entire system.
- Compatibility: They tend to be more compatible than microkernels, supporting a wider range of device drivers.
Read
Other what include Exo kernel and Nano Kernel.
Now, let us further explore the components of the Operating system:
Operating-System Services
Here, we look at services provided by the Operating System. An operating system provides an environment for the execution of programs and offers various services to programs and the users of those programs. If you have been paying attention very well, you would have noticed some of these services in the previous sections, especially in the system call section.
While specific services vary between operating systems, we can identify common categories. Here are the Services provided by the Operating System:
It shows the various services an operating system offers to users and applications. These services are essential for the efficient management and execution of programs and for providing a user-friendly environment.
An easy way to categorise these services is by their purpose:
- One set of operating system services provides functions that are helpful to the user.
- Another set of operating system functions ensures the efficient operation of the system itself. Let’s start with the set of operating system services that provide functions that are helpful to the user.
User Interfaces
The User Interface (UI) is a place through which, the user can give input, get feedback (output), or interact with the computer systems.
Almost all operating systems have a user interface (UI). UI plays a crucial role in how users and developers perceive and utilise the operating system. These interfaces provide different ways for users to interact with an operating system.
This interface can take several forms. They can be graphical-based, touchscreen, or command-line-based.
Graphical User Interfaces (GUIs) are an essential aspect of modern computing. They provide users with an intuitive and user-friendly way to interact with a computer system. GUIs are a significant improvement over the command-line interfaces used in the early days of computing. We will look at:
- The history of graphical user interfaces
- Benefits of GUI
- Customisation of the GUI
- Limitations of GUIs
The history of graphical user interfaces (GUIs) is a fascinating story of innovation and evolution. From the early experiments at Stanford Research Institute (SRI) to the modern mobile devices we carry with us everywhere, GUIs have played a critical role in making computing more accessible and user-friendly. Microsoft’s Windows and Apple's MacOS have been particularly influential in shaping the modern GUI, with their designs heavily influencing the way we interact with our devices today. The rise of voice-activated assistants is the latest chapter in the story of GUIs, offering a new and exciting way for users to interact with their technology. It will be interesting to see where this technology goes in the future and how it will continue to shape how we interact with our devices.
The original GUIs were simply interfaces to make it easier to do things like open applications. Rather than typing a command like “winword” (The command that opened Microsoft’s word processor) you double-clicked on an icon.
Over time the GUI has developed processes and can trigger a series of actions. The search no longer simply searches the hard drive for a file, it also searches the contents of files and the internet.
How it started
The first graphical user interface was created in the late 1960s by researchers at the Stanford Research Institute (SRI). The system, called NLS (oN-Line System), was designed to make it easier to access and manipulate information. It featured a mouse, windows, icons, and menus, which are now standard components of modern GUIs.
The Xerox Alto, released in 1973, was the first commercial computer to feature a graphical user interface.

The Alto was not a commercial success, but it was a significant milestone in the development of GUIs. The Alto's user interface featured icons, a mouse, and a desktop metaphor that has since become standard in modern GUIs.
The Xerox Star, released in 1981, was the first commercial computer to feature a GUI that was similar to what we use today. The Star was a high-end workstation that was not widely adopted, but it was an influential design that inspired the development of the Apple Macintosh and Microsoft Windows.
Successful GUIs
The Apple Macintosh, released in 1984, was the first widely successful computer to feature a GUI. The Macintosh's user interface was heavily inspired by the Xerox Star, but it was more affordable and accessible to consumers. The Macintosh introduced many features that are now standard in modern GUIs, such as the menu bar and the trash can.
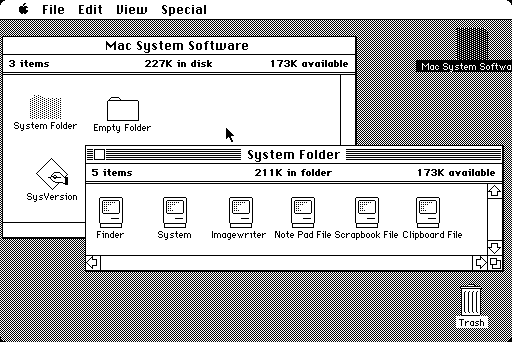
Microsoft Windows, first released in 1985, was an attempt to bring a GUI to the IBM PC. The first version of Windows was not very successful, but subsequent versions, particularly Windows 3.0, were much more successful. Windows 3.0 was the first version of Windows that could compete with the Macintosh in terms of user interface and usability.
Windows 95, released in 1995, was a significant milestone in the development of GUIs. It was the first version of Windows to feature the Start menu, taskbar, and support for long filenames. Windows 95 was a massive commercial success and helped to establish the dominance of the Windows operating system. Interesting fact – Microsoft’s Windows 95 came on 1.44Mb floppy disks or 1 CD, but very few computers had an optical drive.
Mobile GUIs
The rise of mobile computing in the 21st century has led to the development of GUIs for mobile devices. Apple's iOS, first released in 2007, was the first successful mobile operating system to feature a GUI. The iOS user interface was heavily inspired by the Macintosh and featured many of the same design elements, such as icons and a dock.
Google's Android, first released in 2008, was another significant development in the history of GUIs. Android was designed to be an open-source alternative to iOS, and it has since become the most widely used mobile operating system in the world. Android's user interface is similar to iOS, but it is more customisable, allowing users to change the look and feel of their device.
In recent years, Microsoft has been working to improve the user interface of Windows. Windows 8, released in 2012, was an attempt to bring a touch-friendly interface to Windows, but it was not very successful. Windows 10, released in 2015, was a significant improvement over Windows 8, with a more user-friendly interface that is designed to work well with both touch and non-touch devices.
The future of interfaces
The most recent development in the history of GUIs has been the rise of voice-activated assistants such as Apple's Siri, Amazon's Alexa, and Google Assistant. These assistants provide a new way for users to interact with their devices, using natural language to perform tasks and retrieve information. The user interface for these assistants is primarily auditory, although they often have a visual component as well.
Voice-activated assistants have become increasingly popular in recent years, with many people using them in their homes and on their mobile devices. They offer a more natural way of interacting with technology, and they can be particularly useful for people who have difficulty using traditional graphical user interfaces.
Other developments include predictive text, which is an operating system feature that attempts to guess what words you are typing based on your past inputs and those of other users. The accuracy of the predictions increases with the amount of typing you do.
As has been mentioned in the section on “what do operating systems do?” they have a number of functions such as manage files and devices. With the advent of a GUI the way that these have been done has changed.
A GUI allows users to interact with electronic devices or software applications through visual elements such as icons, menus, and buttons. This means that the icons can launch more than applications.
Some of the benefits of GUI include:
GUIs are considered more user-friendly than command-line interfaces because they use visual elements that are easy to recognize and use. Users can easily navigate through the software, perform tasks, and access information.

GUIs can improve productivity, particularly for less experienced users by reducing the time required to perform complex tasks. With a GUI, users can quickly perform operations without researching or memorising complex commands.
GUIs can make software applications more accessible to users with disabilities. By using visual cues and other features, users with disabilities can interact with the software more easily.
GUIs can increase user engagement by providing a more interactive experience. With a GUI, users can see the impact of their actions in real-time, which can help to keep them engaged.
GUIs can provide a standardized interface that can be used across different applications. This makes it easier for users to switch between different applications without having to learn a new interface each time.
GUIs are generally easier to customize than command-line interfaces. Users can easily change the appearance of the interface, add or remove features, and create custom workflows.
On modern devices can have more than one window open at a time. This allows for things like copy and pasting between applications.

Every digital device needs an operating system to manage all the resources that the device can access, such as CPU tasks allocation, memory management, file storage, and access to peripherals. The operating system is also responsible for providing an interface for the user, which is important because it allows users to run applications. One of the main advantages of a graphical user interface (GUI) is that it provides an intuitive and user-friendly way to interact with the operating system and run applications.
For example, an Apple TV device is not suitable for use as a fitness monitor because it lacks the necessary physical sensors or size. However, it is well-suited for entertainment purposes, as it can stream services like Netflix, TVNZ on demand, and others. The operating system on an Apple TV is designed to make it easy for users to select the service they wish to watch, with a GUI that provides an intuitive way to navigate through options.
Similarly, devices like Fitbit and Apple Watch have their own specialized operating systems, designed to make them easy to use for their specific purposes. The GUI on these devices provides an intuitive and visual way for users to access and interact with their fitness data, monitor their health metrics, and receive notifications from their phones.
Embedded systems are specialized computer systems designed to perform specific functions or control specific hardware devices. These systems are often used in devices like appliances, cars, and medical equipment, where the operating system and hardware are tightly integrated to perform a specific task.
In some cases, these embedded systems do not use graphical user interfaces (GUIs) because the devices are not intended for human interaction. For example, a thermostat may use a simple, text-based interface to allow the user to adjust the temperature settings, but it does not require a GUI because it is a standalone device that does not need to display complex graphics or multimedia content.
Instead, embedded systems typically use command-line interfaces (CLIs) or other text-based interfaces or control buttons that allow users to input commands or receive feedback from the system. These interfaces are typically simpler and more lightweight than GUIs, which makes them ideal for use in embedded systems with limited resources.
In summary, an operating system is essential for every digital device, and a GUI provides an intuitive and user-friendly way for users to interact with the operating system and run applications. The examples of Apple TV, Fitbit, and Apple Watch demonstrate how specialized operating systems and GUIs can be tailored to specific user needs and make devices more accessible and easier to use.
Activity
In today's world, we rely on technology more than ever before. From smartphones to laptops to smartwatches, we use a variety of devices to stay connected, stay informed, and stay entertained. But with so many different devices and operating systems out there, it can be hard to keep track of everything.
To help you better understand the devices you own and how to keep them up to date, create a list of your devices and note the operating system on each one to better understand of how they work and what makes them unique.
- Create a list of all your devices, including laptops, desktops, tablets, phones, smartwatches, and your router.
- For each device, list the operating system it uses. Examples include Windows, macOS, Android, iOS, and Linux.
- Describe how the interface of each device helps you use it. For example, you might mention that the touchscreen on your tablet makes it easy to navigate and select apps or that the keyboard on your laptop allows you to type quickly.
- Don't forget to include your router in your list of devices! Make a note of whether you know how to access it.
- Find out how the operating system on each device gets updated. Is it automatic, or do you have to do it manually? Note down the process for each device.
- If any of your devices have applications installed on them, find out how those apps get updated. Again, note down the process for each device.
Share your findings in an Activity Forum post.
With the increase in computing power, software developers have been able to incorporate more advanced customization features into graphical user interfaces (GUIs). These customization features include real-time previewing of customization options, support for high-resolution graphics and animations, and more complex layout and styling tools. To illustrate the impact of increased computing power on GUIs, consider the difference between early mobile phone interfaces, which were basic and static, and the highly customizable and dynamic interfaces of modern smartphones.
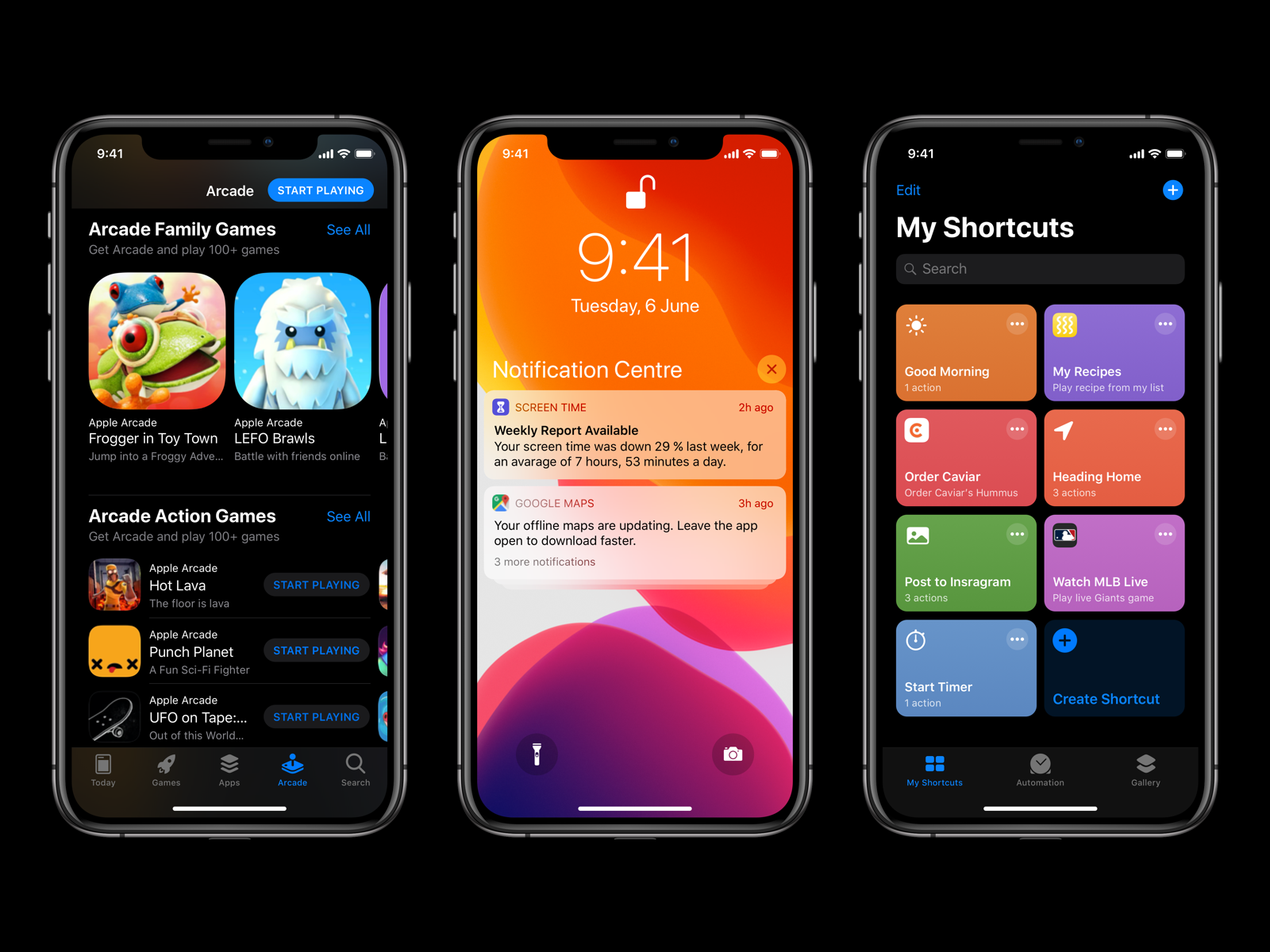
Customising Graphical User Interfaces (GUIs) is essential for enhancing user experience by making software more intuitive and user-friendly. Users can tailor the software interface to suit their preferences by modifying the layout, choosing which features and functions to display, and adjusting the colour schemes and fonts. These customisations can make the software more accessible to users with specific requirements, such as increasing the font size or changing the colour contrast of the interface for users with visual impairments.
GUI customisation can also improve productivity by allowing users to access frequently used functions more easily. Users can create shortcuts to frequently used commands, arrange tools and buttons logically, or group similar functions together. This can save users time and make their workflow more efficient.
Furthermore, GUI customisation can increase software adoption and reduce user frustration. Developers can provide users with the ability to customise their interface, which helps users feel more in control of the software and gives them a sense of ownership over their workspace. This can increase user satisfaction and reduce the likelihood of users abandoning the software due to frustration or difficulty.
The user can experience numerous benefits from GUIs as they continuously advance and become more responsive to user needs and environmental factors. For instance, GUIs can automatically shift into "night mode" on your phone to reduce blue light emission, which can disrupt your sleep cycle. This feature allows the user to seamlessly transition from using their phone during the day to preparing for a good night's sleep. Through these intelligent features, GUIs are able to adapt to the user's needs and create a personalised experience that maximises convenience and ease of use.
GUI customisation provides users with a plethora of features and tools to make their software interface uniquely tailored to their preferences. Among these options are:
These are sets of visual styles and colour schemes that can be applied to the software interface. Users can select a pre-designed theme or create their own.
Users can rearrange the position and size of interface components such as buttons, menus, and panels to suit their preferences.
Users can customize toolbars and menus to include frequently used functions and commands, or hide those that are rarely used.
Users can create keyboard shortcuts or hotkeys for frequently used commands to speed up their workflow.
These include options for changing font size, colour contrast, and other visual settings to make the interface more accessible to users with specific requirements.
Users can use scripting or programming languages to create custom tools, macros, or plugins to extend the functionality of the software and automate repetitive tasks.
In conclusion, the customisation of GUIs is a critical feature that enhances user experience by enabling users to tailor software interfaces to meet their specific requirements. Developers provide users with as many customization options as possible to increase user satisfaction, improve productivity, and reduce frustration.
Activity
On two of your devices, find as many ways as you can to access the settings or preferences of the operating system.
- How many ways did you find?
- How do you usually access the settings or preferences?
Microsoft usually has at least three ways to get to something. Why do you think that Microsoft developed so many different ways?
Share your results in a forum post, and comment on at least two other posts.
- Does anyone else usually use the same methods as you?
- Has anyone found a method you’ve never seen?
GUIs have become the standard interface for modern computer systems, but they also have some disadvantages. Here are some of the common disadvantages of GUIs:
GUIs often require some time to learn how to use them effectively, and users may need to learn new vocabulary and concepts. This can be particularly difficult for users switching between different types of GUIs (e.g. iOS and Android or MacOS and Windows). The differences can often be very frustrating for users.
While GUIs are designed to be user-friendly, they can be slower and less efficient than using command-line interfaces for certain tasks. This is because graphical interfaces require more system resources and more user input to accomplish the same tasks. An example is if you need to rename files. To rename a file in a GUI requires right-clicking, selecting rename, clicking in the name box, and typing in the new name. The number of clicks and selecting from menus can be very time-consuming. If doing a large number of files, this is very inefficient.
Check out some examples here – How to Batch Rename & Mass Delete Files in Windows.
GUIs often limit the user's ability to customize and automate tasks. GUI wizards also tend to only present a few widely used options. If customisations that are not in the wizard are required, users may need to rely on developers to add new features.
GUIs consume more system resources (e.g., RAM, processing power) than text-based interfaces, which can be a disadvantage on low-end or resource-constrained devices.
GUIs consume more system resources (e.g., RAM, processing power) than text-based interfaces, which can be a disadvantage on low-end or resource-constrained devices.
GUI security
Complex software layers and multiple components in GUIs can introduce vulnerabilities that malicious actors can exploit. For instance, malware can exploit a vulnerability in a popular GUI software component to gain access to a user's system. Once the malware gains access, it can use the GUI interface to display fake error messages or pop-ups, which can trick users into downloading additional malware or providing sensitive information.
GUIs also tend to rely heavily on user input, which can make them more susceptible to social engineering attacks. Malicious actors can design fake GUIs or manipulate existing ones to trick users into giving up passwords, financial information, or other sensitive data. GUIs can create a larger attack surface for malware, as complex software layers and multiple components can introduce vulnerabilities that malicious actors can exploit.
While many tools and techniques are available to secure GUIs, the complexity of these interfaces can make them more difficult to protect than other types of interfaces. As such, users and developers must be aware of the potential security risks associated with GUIs and take steps to mitigate them, such as keeping software components up-to-date, implementing strong access controls, and using multi-factor authentication.

In conclusion, while GUIs have become the standard interface for modern computer systems, they do come with limitations. GUIs can have a steep learning curve, which can be particularly challenging for users switching between different types of GUIs. They can also be slower and less efficient than using command-line interfaces for certain tasks, as they require more system resources and user input to accomplish the same tasks. GUIs may also limit the user's ability to customize and automate tasks and can be resource-intensive on low-end or resource-constrained devices. Furthermore, GUIs may not always be accessible for users with certain disabilities or impairments.
