A 'computer user' is an individual who will access the service of a computer or network for the desired need. This can be for various reasons, including entertainment, communication and work purposes.
Users can range from advanced to beginners or casual to regular users.
They can be broken into field categories and groups based on how they use a computer. Some examples include:
- developer
- gamer
- animator
- graphic designer
- web surfer
- photographer/videographer.
End-user computing needs
An 'end-user' is an individual who enjoys the services of a computer network but is not involved in supporting or maintaining the computer service. They are in contrast to programmers, developers, IT technicians and administrators.
In the work environment, end-users are usually the employees of a business or organisation. Typically, they will have their account and username for many reasons, including:
- allowing the user to authenticate themselves by logging in with their username and password for security purposes
- to receive a level of authorisation to access resources depending on their position and credentials at the organisation
- providing adequate support for functions that pertain to their job role
- account owners are protected from other users
- allows an organisation to support user requirements to develop and improve computer systems.
Scenario 1
You have been contacted by one of your clients. They have stated that there is something wrong with their laptop computer.
Background information
The laptop computer is used by a sales manager, runs Windows 7, and is in her office. The admin password is 'admin'.
Problem description from the user
My internet is not working. I need to present and can't access my Google docs. My meeting is in 10 minutes.
Reflect on this scenario and identify what steps you might take to resolve this.
Share, discuss and compare on the forum with your peers.
Resolving technical issues
When issues occur, and employees find themselves unable to complete their duties, IT technicians are called upon to respond to their requests for support and service.
End-user requirement support includes the diagnosis and resolution of technical problems. This may include:
- installing software and applications
- diagnosing issues
- repairing and maintaining all PC hardware and software to ensure optimal performance.
This will include both onsite support and offsite support.
Offsite support may look a little different as it relies on the employee’s computer skills and ability to explain the issues--and how effectively they can communicate how they occurred. This may cause delays and frustration as the support is not physically there to inspect their desktop/laptop. There are, however, resources that can be used to support offsite IT support--one of which is called TeamViewer.
TeamViewer is a cloud-based remote connectivity platform for instant remote access, remote control and remote support. TeamViewer lets the end-user connect securely from anywhere, across platforms and devices, with IT support just a few clicks away—all without requiring a VPN.
Unlike other remote access software, TeamViewer provides support through collaboration with integrated video conferencing, secure file sharing and easy screen sharing tools.
When trying to resolve an issue, IT technicians need to adopt a 'troubleshooting' process to understand how to systematically approach the issue (i.e. what is causing a problem to fix it).
Troubleshooting requires an organised and logical approach to computers and other components problems which may arrive as:
- random issues which arise during preventive maintenance processes
- customers may contact you with different problems as they find issues.
IT professionals will go through an elimination process of asking questions, testing the hardware, and examining various avenues to help them understand the issue and to form a proposed solution.
Before troubleshooting begins, necessary precautions should be taken to protect data on a computer as some repairs might put data at risk. It's important to first ensure backup is successfully completed to prevent data loss whilst attempting repairs.
Troubleshooting process steps
- Aim to identify the strategy.
- Establish a theory to determine probable cause.
- Test the theory.
- Implement a plan of action.
- Implement preventative measures and check if the problem has been resolved.
- Document findings, actions and outcomes.
End-users may face problems attributed to software, hardware and network; some may be combined.
Some common hardware problems
- A storage device may include problems relating to cable connections, incorrect drives and BIOS settings, and incorrect media formats.
- Motherboard and internal components may include loose cables, incorrect drivers and failed updates.
- Power supply issues can be caused by faulty supplies and loose connections.
- CPU and memory issues can include processor and memory problems. These can be caused by faulty installations, incorrect BIOS settings and inadequate computer device cooling and ventilation.
- Display problems are often caused by incorrect settings, loose connections and incorrect or corrupted drivers.

Manage users (individuals or organisation)
Managing user accounts and permissions is an important task on any network. This is the principal means of controlling access to computer and network resources and rights or privileges.
Businesses will tend to organise user and group accounts by 'security groups' (see above) when they assign permissions based on groups rather than individual users. They can do this by creating a 'group' and simply adding that individual.
Typical user groups
- Administrators: Will usually have the authority to perform all management tasks with access to all files and other system resources requiring specific credentials to access.
- Users: When a new user is added, they will be placed into a 'group' and the specifics of that group will dictate what tasks they can perform and what applications they can access and use. These will typically be employees within the business. They may be separated depending on their role and credentials.
- Guests: Guests are individuals with limited rights and access to resources. They may be able to browse the network and save documents; however, they will be limited in performing tasks.
Creating a new user
To create a new user for a separate employee, follow these steps.
- Right-click the Windows start menu button
- Select Control Panel
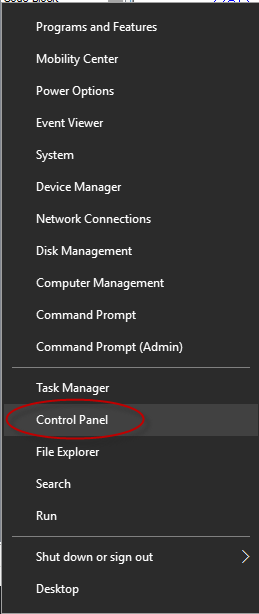
- Select User Accounts
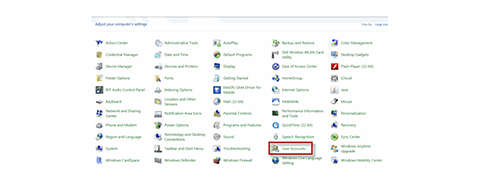
- Select Manage Another Account
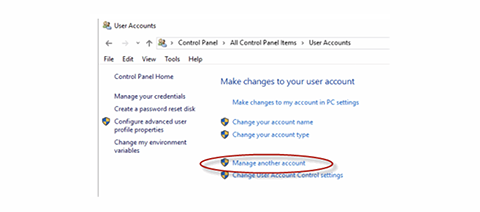
- Select add a new user
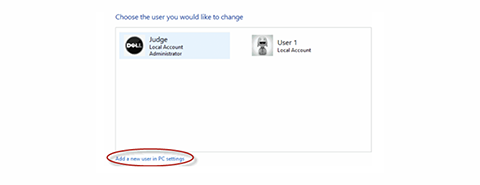
- Use the ACCOUNTS tab to configure the new account
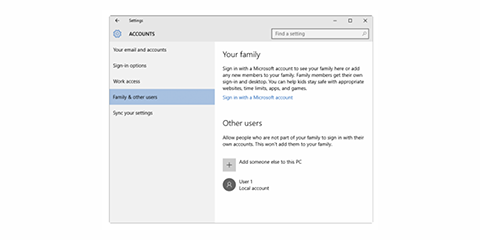
Adding a new user to a group
When a user has been created and is made a group member, the user obtains all the permissions allocated to that group. A user can be a member of more than one group account. To add a user to a group or remove a user from a group, right-click the group account and select Properties.
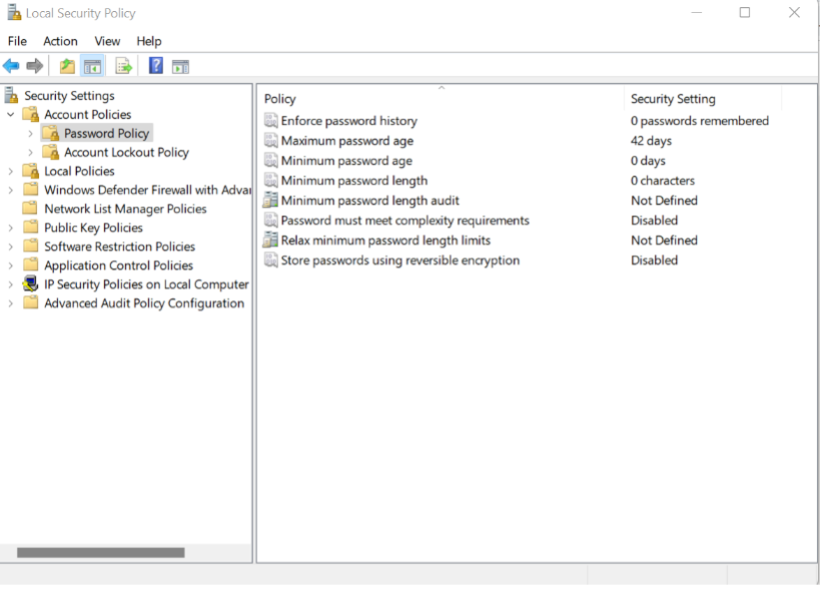
Local security password
Administrative tools can configure passwords and account policies in Local Security Policy.
You would use this to force users to choose more complex or longer passwords or prevent users from reusing old passwords.
Supporting end-user requirements
Supporting end-user requirements will lay the foundation for effective functionality and for all stakeholders to work cohesively together.
Some examples of how to ensure best practices are followed, while supporting the needs of users, include:
- defining the scope of role and objectives
- identifying the tasks, projects and resources needed
- clearly outlining what is needed to support end-users to complete requirements successfully
- involving the users from the start
- having all key stakeholders review the requirements, along with continual improvement.
When identifying user needs, the starting point of all requirements begins at gathering information. This can be completed through verbal or written methods conducted between the business, end-user and IT professional.
Why identifying end-user needs matters
- Correctly identifying end-users’ needs is essential for ensuring customer satisfaction and loyalty. If you fail to identify customers’ needs properly, or if you are indifferent to their needs, they will take their business elsewhere.
- Users may have unique needs, and being able to understand the resources needed to help fulfil their roles will help in meeting their needs.
- Often, end-users aren’t clear about what they need or don’t know what they want. Effective IT service providers/technicians need to be trained to ask the right questions, listen and tailor suggestions to assist end-users satisfactorily.

Documenting client requirements
There are different ways you can document client needs. In the ICT industry, client needs are identified at the start of the project; however, the client can request different things throughout, and at the time of completing, the project.
You need to document any additional client needs in writing and get approval from management before you act on those requests.
You may use different formats to document client needs:
- update the contract
- update the project plan
- prepare sub-contract.
Product Requirements Document (PRD)
A Product Requirements Document (PRD) contains all the requirements for a certain product.
It is written to allow people to understand what a product should do. However, a PRD should avoid anticipating or defining how the product will do it to allow interface designers and engineers to use their expertise to provide the optimal solution to the requirements.
The most common objectives of the PRD are to:
- gain agreement with stakeholders
- provide a foundation to communicate to a technology service provider what the solution needs to do to satisfy the customer/business needs
- provide input into the next phase for this project
- describe what solution (not how a solution) will meet the customer/business needs.
These objectives are important because they are the foundation for all subsequent project deliverables, describing what inputs and outputs are associated with each process function.
Example: When examining the business solution, the BRD should answer the question, 'What does the business want to do?' For example, 'The business wants to serve 100 bottles of red wine each night during a 3-day conference, and the wine must be 57 degrees Fahrenheit when poured'.
The technical solution should support the business solution. For example, 'The company would need a wine cave or refrigeration storage unit to hold 300+ bottles operating between 48 and 52 degrees Fahrenheit'.
Who should be involved?
- Project core team
- Business partner(s)
- Process owner(s) or representatives
- Subject matter experts
- Change/project/product management, quality department and IT management as needed or available.
Some items require detailed documentation to ensure successful implementation. The documentation may address aspects such as:
- Who is the intended user?
- How many users are there? Are they the same type of user or different?
- What level of computer experience will the users have (or is needed)?
- What is the required security?
- Are there hardware constraints–networked or stand-alone?
- What technical support is necessary and available in-house?
- What other systems need to integrate/communicate?
- Backup. Describe the current backup regime (e.g. tape back-up one/day).
- Deliverables. What are the expectations–system, help files, documentation, full source code, training, support, etc.
Scenario 2
When the user turns on the PC, it does not always come on, and sometimes it just shuts itself down abruptly, with no warning. When she turns on the system again, there is no fan noise. She uses a legacy database application and the data is corrupted during the improper shutdowns.
Reflect on this scenario and identify what steps you might take to resolve this.
Share, discuss and compare on the forum with your peers.
Troubleshooting Cisco technical issues
Cisco is a multinational technology corporation that develops, manufactures and sells hardware software and networking equipment.
Click here to see a list of products they manufacture.
The following table identifies some symptoms, problems and solutions regarding Cisco hardware.
| Symptom | Problem | Solution |
|---|---|---|
| All LEDs, including OK LED, are off. | No power to the router. | Perform the following steps:
|
| No connection to Ethernet device. (Ethernet 1 LED is off.) |
A cable-related problem:
|
Perform the following steps:
|
| No connection to ADSL link. (The CD LED on the front panel has been off for a long time.) | Improperly connected cable. | To make sure that you have connected the ADSL cable properly, ensure that the connectors at both ends of the cable are securely seated. |

