Cloud Computing, more popularly known as “The Cloud”, is an internet-based computing solution where applications, servers, storage and platforms are shared and accessed by multiple users from a single system. This allows users to access their computer data and applications using other computers and/or from mobile devices.
Previously, computer systems featured heavy and expensive mainframes that had to be housed in large secure facilities. Over the years, these have evolved into smaller servers that can be maintained within the workplace, but they still require a lot of resources and can be expensive to maintain. They can also be difficult to access remotely and will have a finite storage capacity.
Data storage is a big concern for businesses. By having a centralised cloud-based data system, no data is stored on individual devices and there is no need for a server facility on-site. Data security is also centralised, making it safer from attacks.
To utilise a cloud computing system users require a device that is connected to the internet and has applications (apps) or software that can access their information from the cloud. These cloud-based computing services can be acquired from third-party providers.
The main benefits of a cloud computing system are:
- Productivity - Staff can access systems anywhere, anytime. This helps if the workforce is spread out, working from home, or travelling.
- Scalability - Cloud systems can easily grow to accommodate business needs at any given time.
- Reduction in capital spending - There is no expensive server equipment to purchase or maintain.
- Reduction in ongoing operating costs - Due to cloud service providers having multiple clients they are able to offer a reduced price for technical support and platform inclusions. They also offer different types of pricing levels, payment plans, and bulk rates for larger user numbers.
- Security - Cloud systems have high levels of security, including standard encryption, password access, security codes, two-factor identification, facial and voice recognition, and security questions. The reasons for the additional security is because cloud systems can be accessed more easily by external people. Therefore, cloud systems providers have extremely robust security features in place. This is not to say that cloud systems are infallible. Due care still needs to be taken to protect data from unauthorised access.
- Data-Loss Prevention - The loss of data is drastically reduced as cloud-based computing automatically saves data. There is no need to have several hardware backups in case the equipment malfunctions.
- Privacy - Maintained through permission settings, only individuals who have been granted access can view or download certain files. This benefit also links to security. Due care must be taken to ensure unauthorised access is not allowed.
- Online Technical Support- Most cloud systems have a support system in place such as FAQ pages, helplines and chat forums. This lessens the wait time for service provider technicians to address concerns, minimising the waste of time and money.
Cloud systems are divided into two models, these are explained in detail later in this topic:
-
Deployment Model - A specific configuration of environment infrastructure and storage size. Deployment models can vary depending on who controls the infrastructure and where it is located.
-
Service Model - The different types of service provisions that cloud computing hosts provide for companies. Service models vary depending on the unique needs of the business.
Traditional computer systems consisted of mainframes (the 1960s) that needed to be housed in large secure facilities with cooling systems that were often equivalent in size to a large shipping container. Over several decades this infrastructure has evolved into smaller servers that could be accommodated on the premises of the business, but the resources were intense and expensive. Each user had a hard drive on which programmes were installed which included a license for each installation.
Data storage was challenging to manage as users protected their work with passwords on their hard drives or removable storage devices. This meant that data was often outdated and was never the same from one user to the next; which could result reconciliations and financial reports not being accurate.
By having a centralised cloud-based data storage system which other applications can access, eliminates the need for users to store data on their own devices. Security is also centralised and ensures that company information and data are safe from malware and hackers. This also means that only one installation of security software needs to be maintained.
Obtaining cloud-based computing systems and programs is conducted via third-party providers. These providers provide the infrastructure, software, and applications at a reduced price to a wide range of clients to take advantage of economies of scale. Users only need an internet-connected device to access the relevant application and data to complete their task.

There are three main types of Clouds (or Deployment Models) that have their own privacy, security and management requirements:
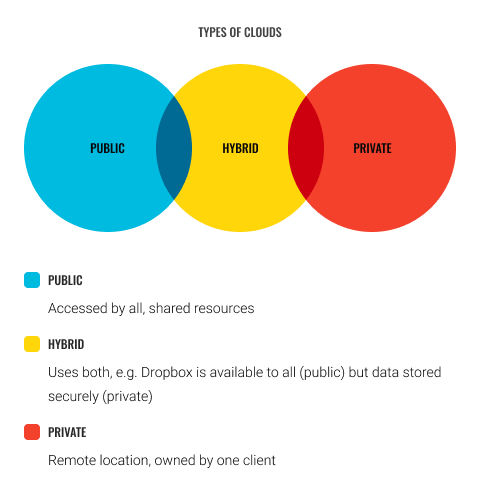
- Public Cloud - In this type, the infrastructure (network) is provided by a cloud service provider. These are shared resources and are the most vulnerable to attacks from hackers and malware. Customers have no physical control of the infrastructure. Gmail is an example of a Public Cloud service. Whilst emails are protected by a password, the hardware on which they are stored is shared by over 1 billion people (as of 2017).
- Private Cloud - This is where the infrastructure (network) is used solely by a single organisation. It is still housed off-site (ie. in the cloud) and hosted but is not shared with others. While more expensive, this gives the owner physical control of the structure and provide more security layers through the use of company firewalls.
- Hybrid Cloud - In this type, both Public and Private clouds are used. An organisation may use a public cloud to interact with customers but keep their data secured in a private cloud.
- Community Cloud- This is where the infrastructure is shared between organisations including shared data. An example of a community cloud is a local government where clouds can be located both on and off the premise.
Another lesser-used type of deployment model is known as Community Cloud. This cloud is shared between organisations including the data. Local government community clouds are good examples of this. They can be located both in and out of the office premises.
Benefits of Cloud Computing
Although cloud computing has been around for some time, business has been slow in adopting this service. This is due to the perceived risks the new technology and business models pose.
However, with service providers proving that they can manage those risks, cloud computing is gaining more acceptance and business is moving rapidly towards adopting the various service offerings.
Cloud computing provides a way for a business to manage its computing resources online.
Some of the key benefits of Cloud computing are:
- It allows businesses to access their information virtually, creating a flexible and global way of accessing their data in any place, at any time.
- If experiencing a natural disaster, power failure or other crisis, having data stored in the cloud ensures it is backed up and protected in a secure and safe location.
- Instead of buying their own IT requirements, a business can rent capacity (server space or access to software) from a cloud service provider, and connect over the internet, paying for only the resources they use.
- It allows for flexibility of work practices and collaboration efficiency.
- A business can scale up or scale down their operation and storage needs quickly to suit their situation, allowing flexibility as needs change. Rather than purchasing and installing expensive upgrades or hardware themselves, their cloud computing service provider can handle everything.

It is advisable to review a wide range of service providers. Ensure unbiased information is used as the first basis for provider choice, Government or Industry Associations are a good place to start any research. After an initial decision is made more comprehensive research can be conducted directly with certain companies via their websites or a customer service agent.
Some examples of common cloud-based computing system service providers are:
- Amazon Web Services
- Microsoft Azure
- Google Cloud.
Each provider will have a range of different product options with varying inclusions and costs depending on business needs.

Due to the rapid growth and popularity of cloud-based computing, there are several different models and strategies which have been developed to meet the needs of different types of users. The foundation services are based on the following:
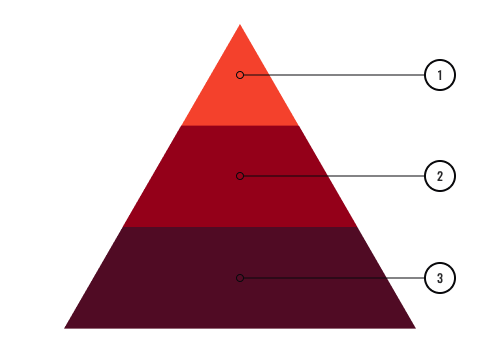
- End-user (SaaS Software)
Google Docs, Xero, MYOB, QuickBooks - Developers (PaaS Software)
Google App Engine, MS Azure - System Administrators (IaaS Software)
Amazon Web Services (AWS), Go Grid
Software as a Service is a complete product that is run by a service provider and is often referred to as an end-user application. Most SaaS applications are web-based. The user does not need to deal with anything as the service provider maintains everything about the application, including updates.
Examples of SaaS include:
- Dropbox
- Salesforce
- MailChimp
- Slack
- DocuSign
- QuickBooks Online
- Xero.
Platform as a Service takes away the need for infrastructures such as hardware and operating systems. Offering access to cloud-based environments in which users can build and deliver applications without the need to install and work with integrated development environments.
- Provides the framework on which to build other applications
- Makes the testing of applications quick and cost-effective
- Lessens the time to deploy new applications and/or updates.
Examples of PaaS include:
- AWS Elastic Beanstalk
- Heroku
- Google App Engine (GAE)
- OpenShift
This model has the highest level of flexibility and control over the IT resources used in current systems. IaaS provides the following:
- The infrastructure to run the other models [PaaS, SaaS]
- Security and availability are ensured by the service provider.
Examples of IaaS include:
- DigitalOcean
- Rackspace
- Amazon Web Services (AWS)
- Cisco Metacloud.
Virtualisation VS Scalability
Virtualisation
Virtualisation duplicates or simulates an environment. Within cloud computing, virtualisation essentially means that a user can access an application, data, or an operating system from any device from any location and it will look the same on all devices.
Virtualisation is the process of creating a virtual environment on an existing server to run your desired program, without interfering with any of the other services provided by the server or host platform to other users. The virtual environment can be a single unit or a combination of many such as operating systems, network or application servers, computing environments, storage devices and other similar environments.
Virtualisation makes it possible to run multiple operating systems and multiple applications on the same server at the same time. It makes servers, workstations, storage and other systems independent of the physical hardware.
Scalability
Scalability means that companies pay as they use applications, data, or infrastructure and they're not tied to licensing fees. If the organisation needs to employ an additional five consultants for three months to help with their year-end processes, no additional license fees will be applied. Companies can also identify new service offerings quickly, without having to go through a development and testing cycle; businesses are becoming more agile in their business models.
The various layers of the cloud stack deliver a range of additional services which are offered by providers. All of which decrease the costs to clients to run similar services and technologies. The following is a brief overview of several additional cloud-based services which organisations can establish as part of their business operations.
Other cloud computing services include:
- Storage as a Service (STaaS) - Provides storage facilities on a pay-for-what-you-use service.
- Security as a Service (SECaaS) - Provides focused cloud security services on a subscription service to secure data and applications from attack.
- Data as a Service (DaaS) - Users access a data repository being managed by a provider. Examples are ERP and CRM systems.
- Test Environment as a Service (TEaaS) - Provides specialised platforms so that developers can test their applications.
- Desktop as a Service (DTaaS) - A software that allows the user access to applications from any location and on any device.
- Application Programming Interface (API) as a Service (APIaaS) - This provides developers with technology and other resources to develop APIs.
- Communication as a Service (CaaS) - Communications systems delivered to clients via the internet, eg. Video conferencing or VoIP.
- Business Process as a Service (BPaaS) - This provides standard business processes for clients to access their current business processes.
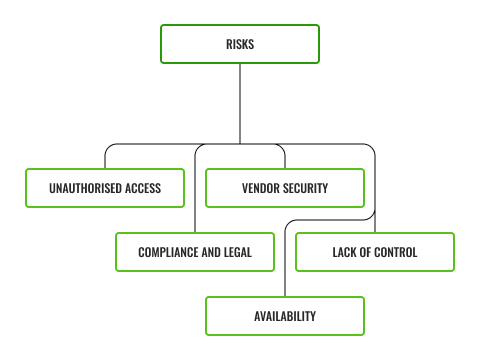
The implementation of a cloud-based system brings many benefits to organisations and their customers, however, there are a number of risks to implementing a cloud-computing service that must be considered and mitigated, some of them are:
Unauthorised Access
Cloud computing essentially means that all company data is stored within a centralised location run by a third-party provider. Whilst these providers have vast resources at their disposal to implement robust data security mechanisms there will always be the risk of unauthorised access from hackers, malware and/or internal threats/leaks.
Centralised data storage also makes it easier for regulatory authorities to gain access to information. Whilst, in theory, these agencies require permission/warrants to view or download this information there may be exceptions to these rules.
Having a private in-house data storage system (ie. not cloud computing) does not provide a completely secure environment, however, it certainly makes the process of third-party access more complex. It is easier for anyone, criminal or regulatory, to access, view, download, amend, and/or corrupt data that is stored remotely and shared with others.
Vendor Security Risks
Utilising a cloud computing service from a third-party provider opens up the risk of vendor security-related issues. The main concerns are in relation to factors such as the character of the vendor's employees, the type of security mechanisms they have in place, and also how the vendor uses information that it has access to through the provision of cloud computing services.
There have definitely been issues reported in the mainstream media over the years related to security concerns with company and personal data that has been entrusted to a third-party provider and then leaked, shared, or even sold to other interested parties for a variety of reasons.
Compliance and Legal Risks
Certain industries, and also certain countries/regions, have different data security regulations in place to protect individual privacy. This may affect a company that is operating within an environment in which extremely sensitive information is collected and stored, such as healthcare, banking, or government.
If a company has operations across multiple geographical locations they have a compliance and legal obligation to be aware of the local rules relating to privacy and storage of sensitive information and ensure that any cloud computing system/provider they are utilising meets these standards. This may mean that the provider has to house their data servers in a certain region (ie. Europe or Australia) and/or must have higher than normal standards of security and access privileges.
Risks Related To Lack Of Control
Working with a third-party organisation means that a certain amount of individual control is removed from the company and entrusted to the service provider. Factors which may be unable to be addressed may include:
- Pricing structures
- Network configuration
- Software features
- Security provisions.
Availability Risks
Cloud computing is reliant upon a steady internet connection and infrastructure workability, at both ends of the spectrum.

If a business loses internet access as a result of not paying invoices or through a natural disaster that affects infrastructure, then employees will not have access to shared drives or files until the situation is rectified.
At the service provider's end, there may be scheduled maintenance, upgrades, security threats, legal concerns, or in extreme situations third-party provider closure/bankruptcy, which may affect the availability of data.
There are many sources of information related to cloud computing. Before making a choice regarding a service or provider it is important to obtain all the necessary information from unbiased, credible sources.
Remember, private cloud computing service providers are essentially trying to sell their product/service. Whilst this doesn't mean that the information they provide is wrong or incomplete, it will be biased towards their product/service which may not be the best option for a particular business. As a general rule, Government websites dedicated to small business information and/or accredited industry associations are the best options for unbiased information.
Some Government and/or Industry Association information relating to cloud computing are listed below:
- Business Queensland - Cloud computing for business.
- CPA Australia - A guide to the cloud
- Department of Infrastructure, Transport, Regional Development and Communication (federal) - Cloud computing and privacy (small business factsheet)
- Business.gov.au - Understand the benefits of going digital
Before deciding which service provider or platform/software type to utilise it is worth comparing different products in the market. One resource that can assist with this task is the Public Cloud Services Comparison Tool, which details the inclusions, benefits, costs, and other features of a variety of well-known providers.

