Imagine that Alex and Ngaire lived in a utopian village many years ago, where trust and collaborative law give them a sense of safety and security. Everyone in the village knows one another; visitors are greeted warmly with full respect, vital resources are shared and accessible to all, and information is communicated instantly through an open communication system.
Our digital security cameras, Internet hazards, and genuine data safety concerns fast forward to the digital age. Alex could be charged with trespassing just for grabbing an apple from Ngaire’s garden.
The modern Alex and Ngaire might not grow Apple trees in their backyards, but they will likely have valuable information stored on their Apple iPhones and MacBooks. So how do we handle real-world risk and apply digital security concepts in the modern age?
This topic will cover the concepts, hardware, software, and planning required for a high network security and continuity level.
- Security concepts, appliances, and software
- Common attacks
- Defence against attacks
- Threat mitigation strategies
- AAA (Authentication, Authorisation, Accounting)
- Inventory Management
- Incident and disaster and contingency planning
- Social responsibility in I.T.
All data transmitted via a network is made up of strings of information that eventually become translated into precious digital assets when they reach their destination.
Assets can include but are not limited to:
- Identity data (name, address, drivers' licence, passport, tax file number, etc.)
- Financial data (bank accounts, balance and debt amount, investment, etc.)
- Intellectual-property (images, design, writing, music, etc.).
Applying the necessary measures in security can protect a person or property from harm, which may be intentional or unintentional. Implementing safety measures can sometimes mean sacrifices to user convenience.

Information security protects transmissions and digitally formatted information, known as assets. Organisations rely on having a good system to protect their assets. Securing information is a constant challenge; there are no one-stop answers. There are also many different types of attacks with increased frequency and innovation.
While security also benefits from advancements in technology, we still must deal with issues surrounding:
- software patch management - updates to the software to correct errors (vulnerabilities or bugs)
- smartphone and other BYOD policies
- and the biggest challenge of all – Users.
Research from Kaspersky Lab has found that 52 per cent of people do not password-protect their mobile devices, and only 22 percent of consumers use anti-theft solutions on their phones. A third (35%) of people use their smartphones for online banking. Furthermore, 57 per cent of people regularly use their smartphones to access personal email accounts, and 55 percent use them for social media activities. 29
Of the users who do not use passwords:
- 97% have auto-logon enabled for email
- 50% have auto-logon enabled for online banking
- 77% have auto-logon enabled for social networking
- 65% use this phone to access their company’s network
Millions of unprotected smartphones can go missing, and if the data wasn’t backed up, it would not be recoverable to the owner.
Cryptography studies secure communications techniques that allow only the sender and intended recipient of a message to view its contents. The term is derived from the Greek word kryptos, which means hidden. 30
The following are the various cryptography terms:
- Encryption/decryption is an encrypting or turning a readable document into a non-readable document that can be sent safely over public lines; on the other side, the non-readable document is decrypted or turned back into the original readable document.
- Authentication is a process that validates the identity of a person or entity.
- Non-repudiation is a process in which the sender cannot repudiate or deny being the sender.
- Cleartext is data stored or transmitted without encryption (same data as Plaintext).
- The plaintext is data to be encrypted (input into the encryption algorithm).
- The ciphertext is scrambled text (an output of the algorithm).
- Key is the mathematical value entered into the algorithm to produce ciphertext or, in the reverse process, to decrypt the message.
- A digital signature is used to verify the sender is the source of sending the information.
The basics of information security
The three basic characteristics of data or information security are as follows:
Confidentiality
This component is often associated with secrecy and the use of encryption. Confidentiality in this context means that the data are only available to authorized parties. When information has been kept confidential, other parties have not compromised it; confidential data are not disclosed to people who do not require it or should not have access. Ensuring confidentiality means that information is organized in terms of who needs to have access and the sensitivity of the data.
A breach of confidentiality may occur through different means, such as hacking or social engineering.
Integrity
Data integrity is the certainty that the data is not tampered with or degraded during or after submission.
Certainly, the data has not been subject to unauthorized modification, intentional or unintentional.
There are two points during the transmission process during which the integrity could be compromised:
- during the upload or transmission of data or
- during the storage of the document in the database or collection.
Availability
This means that the information is available to authorized users when needed.
For a system to demonstrate availability, it must have properly functioning computing systems, security controls and communication channels. Systems defined as critical (power generation, medical equipment, safety systems) often have extreme requirements related to availability. These systems must be resilient against cyber threats and have safeguards against power outages, hardware failures and other events that might impact the system's availability. 31
The International Standards Organization (ISO) developed the Open Systems Interconnect (OSI) model in 1981. It consists of seven functional layers that provide the basis for communication among computers over networks, as described in the table below.
You can easily remember them using the mnemonic phrase “All People Seem To Need Data Processing.” Understanding this model will help you build a strong network, troubleshoot problems, develop effective applications, and evaluate third-party products. 31, 32
| Layer | Function | Protocols or Standards |
|---|---|---|
| Layer 7: Application | Provides services such as e-mail, file transfers and file servers | HTTP, FTP, TFTP, DNS, SMTP, SFTP, SNMP, RLogin, BootP, MIME |
| Layer 6: Presentation | Provides encryption, code conversion and data formatting | MPEG, JPEG, TIFF |
| Layer 5: Session | Negotiates and establishes a connection with another computer | SQL, X- Window, ASP, DNA, SCP, NFS, RPC |
| Layer 4: Transport | Supports end-to-end delivery of data | TCP, UDP, SPX |
| Layer 3: Network | Performs packet routing | IP, OSPF, ICMP, RIP, ARP, RARP |
| Layer 2: Data link | Provides error checking and transfer of message frames | Ethernet, Token Ring, 802.11 |
| Layer 1: Physical | Physically interfaces with transmission medium and sends data over the network | EIA RS-232, EIA RS-449, IEEE, 802 |
Digital certificates are utilized in the Public Key Infrastructure (PKI). The digital certificate, an electronic document, is used to bind the public key to the identity of a person or entity. The digital certificate can be used to:
- Restrict viewing of the message to a particular recipient (encryption/decryption)
- Prove the identity of the sender later (authentication)
- Show that only a given sender could have sent the message (non-repudiation)
- Verify that the document was created or sent by a given sender (digital signature)
As mentioned earlier, a digital signature is used to verify the sender is the true source of sending the information.
The digital certificate is based on the X 509 standard; it uses the serial number, issuer, validity, and subject elements to identify the document sender. Watch this video to learn how digital certificates are created and what they include:
Digital certificates are referred to as keys. PKI uses two keys, a public key and a private key. When to use the public or private key depends on the intended use.
Symmetrical Key Encryption
When you use the same key to encrypt (lock the message) and decrypt (unlock the message) a file, you use a symmetrical key.
The sender uses the key to encrypt the message, and the recipient uses the identical key to decrypt the message. Although using the same key for encryption and decryption is quick, it is not very safe. It is difficult for two people, especially those who have never met, to share a key without others discovering the key and decrypting the message intended for only one other person.
Think of it this way. You could lock the door of your home, then leave your key under the mat for someone else to use, like your friend who will check on your pet while you are away. But that would run the risk of others finding your key under the mat when it was meant for your friend alone.33
Asymmetrical Key Encryption
Asymmetrical key encryption, by contrast, uses both the public key and private key to unlock each other.
The public key is shared with everyone and is published where others can retrieve it; the private key, on the other hand, is used by only one person. Asymmetrical key encryption allows for sharing a symmetrical key, encryption, digital signature, and non-repudiation.
Key sharing
We noted above that asymmetrical key encryption allows for sharing a symmetrical key. Key sharing requires multiple steps. At its simplest, key sharing can be thought of as a two-step process:
Step 1: Asking for a shared key. The public key is accessed and used to encrypt (lock) the request for a shared key.
Step 2: Providing a shared key. The shared key is placed in the message and used for further encryption and decryption.
The following are the layering techniques and defences against attacks:
- Layering
- Diversity
- Limiting
- Obscurity
- Simplicity
Layering
Information security must be created in layers to make it harder to penetrate the systems.
Diversity
Layers must be different (diverse); if attackers get through 1 layer, they can’t use that same approach on all the layers.
Limiting
Limiting access to critical data, only those who use data are granted access. Access is a ‘need to know only basis. Example:
- Accounting - may need access to payroll information AND customer sales information.
- Sales - only need access to customer sales information. Each salesperson only needs access to their customer sales information, not ALL sales data.
Obscurity
Obscuring inside details to outsiders.
- Not revealing details about systems (i.e., not publishing SSID; not listing specific information on WHOIS server; not revealing brand of routers)
- Creating servers with inaccurate or false information (“honeypots”)
Simplicity
A secure system should be simple for insiders to understand and use but complex from the outside. If the system is too complex, trusted users will compromise for ease of use, such as complex password rules.
Identifying the basic steps of an attack
Specifics of personal attacks may vary; however, it is possible to define the phases of a cyber-attack. This provides a common basis for understanding how and when threats arise to optimise vigilance, prevention, and effective responses. (DNV, 2022)
- Probe for information (on users, systems, anything that can be used to launch an attack)
- Penetrate the defences and launch an attack
- Modify security settings (enabling control of the computer)
- Bounce to other systems in that network
- Paralyze networks and devices on the network
Network attacks category
There are many different types of attacks on the network. Here are some of the major categories:
- Web application attacks
- Client-side attacks
- Buffer overflow attack
- Denial of service attacks
- Interception and poisoning attacks
Web application attacks
The commonality for all web app attacks is that they would all have code injection. Attackers inject their code into the website, such as HTML, SQL, XML, LDAP, etc.
SQL Injection
Targets SQL servers by injecting commands into input fields that are not being validated. If input validation is on, SQL injection won’t work.
Validation Check Example - Incorrectly formatted e-mail address
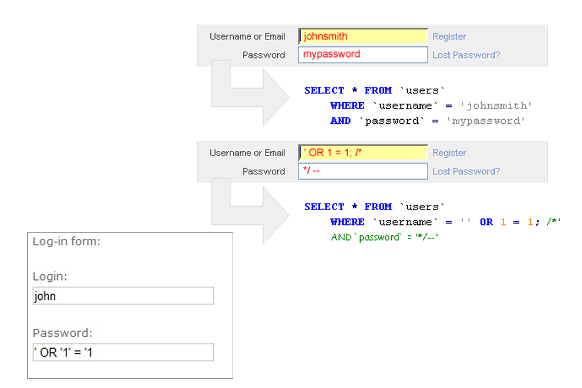
Attack steps:
- Inject your SQL into a statement that the application will use to query the database
- The attacker enters an incorrectly formatted e-mail address
- Response lets the attacker know whether the input is being validated
Injected SQL to:
- Bypass Authentication
- Retrieve Data (or database!)
- Upload Scripts
- Delete Database(s)
- Execute Commands
Cross-Site Scripting (XSS)
The method employed by the attacker for XSS is by injecting scripts into a Web application server and waiting patiently for the next action to be performed by the victim. When the victim visits injected site, malicious instructions are sent to the victim’s browser. Browsers cannot distinguish between valid code and malicious script.
HTML & XML Injection
This attack is similar to a SQL injection attack, where the attacker discovers a website that does not filter user data and injects XML tags and data into the database. The Xpath injection contains a specific type of XML injection attack and attempts to exploit XML Path Language queries.
Client-side attacks
The previous web application attacks are server-side attacks. Client-side attacks, on the other hand, target vulnerabilities in client applications. Attackers interact with a compromised server, followed by the client initiating a connection with the server, resulting in an attack.
Buffer overflow attacks
Computers are made up of math and movement at their core, and a buffer is a place to store data temporarily.
In physical memory storage (RAM), data is stored. It is received from an input device before sending it to an output device, moving data between processes. The attack attempts to store data in RAM beyond the boundaries of a fixed-length storage buffer.
Data overflow into adjacent memory locations may cause the computer to stop functioning. The attacker can change the “return address” and redirect to a memory address containing malware code.
Denial of service attacks
Denial of service attacks attempts to prevent the system from performing normal functions.
ICMP attacks
ICMP stands for Internet Control Message Protocol and is the most used protocol in networking technology. A connectionless protocol, ICMP does not use any port number and works in the network layer. ICMP is commonly used for diagnostic purposes, error reporting or querying any server, and right now, attackers are using ICMP to send payloads, which we will discuss here. The popular ping command will use ICMP. (Infosec 2018)
Ping is a command-line utility available on virtually any operating system with network connectivity that acts as a test to see if a networked device is reachable. The ping command sends ICMP echo request packets to a specific device over the network. Successful ping results in a response from the computer pinged back to the originating computer. (Paessler 2018)
Examples of ICMP attacks are:
- Network Discovery (aka ICMP Sweep) - Discover information about hosts that are on the network
- Smurf DoS Attack - Broadcast a ping request to all computers in the network but change the address to the target. Each computer responds to the target and overwhelms it.
- ICMP Redirect - ICMP redirect packet sent that asks hosts to send its packets to another “router”, which is a malicious device.
- Ping of Death - Malformed ping sent to victim’s computer that exceeds the size of an IP packet which causes crash (max length = 65535 octets)
- Distributed Denial of Service (DDoS) - Attacker uses many zombie computers in a botnet to flood a device with requests. Virtually impossible to identify & block the source of the attack.
Interception and poisoning attacks
Man-in-the-Middle
Man-in-the-Middle attacks perform interception of legitimate communication. Attacks can be passive or active. Passive attack records transmitted data, whereas active attack alters transmission contents before sending to the recipient.
Replay attacks
Similar to the previous man-in-the-middle attack, the attacker makes a copy of the transmission to be used later. Example - Capturing login credentials.
Variations to replay attacks can be more sophisticated:
- The attacker captures the network device’s message to the server
- Later sends an original, valid message to the server
- Establishes trust relationship between attacker and server
Poisoning Attacks
Poisoning attack uses ARP (Address Resolution Protocol) and replaces valid addresses with fraudulent addresses. It resolves network layer addresses (IP addresses) into data link layer addresses (MAC addresses).
ARP Poisoning
The attacker modifies the MAC address in the ARP cache to point to a different computer.
DNS Poisoning Attack
DNS poisoning attack substitutes malicious IP addresses in the DNS cache; they can be done in the localhost table or external DNS server. However, it can be prevented by using the latest version of the DNS server.

You have now been exposed to a long list of threats that can be loosely categorised into these objectives:
- steal personal data and login information
- modify security settings to take control of devices
- stop essential services to paralyse networks services.
You have also learned about some of the security measures taken to mitigate these risks. We are now going to expand on that information. You may remember that security is provided in physical protection procedures such as locking laptops in drawers at the end of a workday and using key cards to get in/out of the building and digital protections by devices and software, such as two-factor authentication and firewalls.
If someone gains access to the server room or paper file storage, for example, and physically destroys machines, routers, and switches, or steals employees' personal information, you need to:
- Know what information was compromised by knowing what information is stored on which servers or file drawers.
- Know how to isolate the attack as quickly as possible to prevent further breaches.
- Identify the person that entered the room and created the chaos.
- Communicate the problem and steps taken to solve it.
To accomplish all of this, you need to start with considered planning, careful execution of the plan, monitoring and tweaking as threats appear, and a clear line of communication internally and externally to those outside the organisation who will be impacted by the downtime, or delay caused by the attack.
Physical security controls
Businesses protect people, equipment, and sensitive information by ensuring only those who have a right to enter the premises can do so, and only those who require access to information can get to it.

This is an example of a charging station that stores laptops behind a lock. These types of secure cabinets are often used in libraries and school campuses.
When you want to protect your home, what tasks might you do to protect the people and materials inside your house?
Did you think of any of these?
- Lockable doors – control who gets in and out by giving only some people keys.
- Lockable windows – ensure that any potential leaks are sealed securely.
- Security alarm – While you sleep or are away from the house, it's still being monitored.
- Guard dog – A (secondary) alert system that flags entry into a private area.
Most businesses don’t use guard dogs to protect data, but if an intruder gets into the front door, the warning bark of a dog is the real-world equivalent of a flag or digital alert indicating unauthorised access to a database.
The concepts of home security apply to network security as well. Complete the following activity to remind yourself of the physical aspects of information security.
Firewalls
A firewall, like a password, is a crucial part of the overall security of a network to protect against cyber threats. For enterprise and medium-sized businesses with high-security needs, cloud-based firewall services—called Firewall as a Service (FaaS) and a Hardware Firewall—a physical device or set of devices tasked with network security—may be required. Homes and small businesses may have enough protection from adding and configuring firewall software on a personal computer. All firewalls offer a wall of protection between the outside world and the network.
All traffic must be routed through the firewall where all users can be authenticated at login and have only as much authorisation as necessary. At the same time, the system monitors activity and flags anything suspicious.
Your planning should include:
- a documented security policy
- traffic checkpoints for monitoring
- activity logging
- limiting exposure to your internal network.
Firewalls are used for specific and broad network protection, and it will depend on the business needs as to which is best for any particular network setup. Many businesses will use a combination of the following systems.
Packet-filtering firewalls
Due to some limitations, a basic firewall that can be run on a standalone firewall device or general-purpose computers and routers is best for SOHO networks. This type of firewall is configured for the following:
- address where the packet originated
- destination address
- protocols in place to transfer the data.
Proxy service firewalls – This system filters messages at the application layer, serving as a gateway between your network and servers on the web.
Stateful multi-layer inspection (SMLI) firewalls – A step up in firewall types, this filters traffic based on state, port, and protocol, along with the rules and context an administrator configures. The use of multi-layer monitoring makes this a stronger choice for bigger organisations. However, it cannot distinguish between harmful or harmless web traffic, so additional software should be used to cover all the bases.
Unified threat management (UTM) firewalls – This firewall combines the functions of the SMLI firewall and adds intrusion prevention and antivirus protection.
Next-generation firewalls (NGFW) – A highly sophisticated option, it has more security levels by looking at the packet header and the contents and source. They are successful in preventing the most current type of cyber threats.
Network address translation (NAT) firewalls – A strict protocol that only allows inbound web traffic if a device on your network solicited it.
Choosing a firewall is a combination of business needs, budget, location, and network topology.
Network-based vs. host-based firewalls
You may find that you need both types of firewalls protecting your network.
- Network-based firewalls are used for businesses with a large number of devices and data filter traffic going to and from the internet to the LAN or WAN. It protects against malicious attacks by monitoring communications between the computers within the network and the outside world, and it can block specific websites, IP addresses, or other services.
- Host-based firewalls are software applications or part of the native OS and are stored locally on a single computer or device and allow for a good deal of customisation. They would be installed on each server.
There are many ways to set up a firewall, and the risks of getting it wrong can be catastrophic for the business. Here are a few tips to help you avoid some more common configuration errors.
Let's look at a network topology that includes a firewall device. Take note of the positioning between the web services and the entire rest of the network.
Proxy Servers
A proxy is a substitute for something else. For example, a person who votes on behalf of someone unable to do so is called a proxy voter. In networking, the proxy server acts as a substitute IP address to the outside world for the private IP address of the client on the corporate network.
Using a proxy server provides security between the corporate (internal) network and the Internet (external). All Internet traffic from the corporate network must be routed through the proxy server, where it is checked against the whitelist or blacklist to see whether it is authorised to reach the Internet.
If the transmission is allowed by the proxy server, it will connect to the Internet on behalf of the originating client. This protects the internal network by not allowing individual workstations to directly connect to the Internet without going through the proxy as a filter for authorisation and masked IP.
Network security can be enforced on the proxy server to reduce threats from the Internet and control the websites accessed from the network by only allowing communication with legitimate sites, further reducing the risk of harm.

A combination of policies, protocols, and personal responsibility will keep the network secure.
Authentication, authorisation, accounting (AAA)
AAA describes a framework for intelligently controlling access to computer resources, enforcing policies, auditing usage, and providing the information necessary to bill for services. These combined processes are considered important for effective network management and security.
- Authentication: Prompts the user to present credentials to access the network.
- Authorisation: The process of determining what types or qualities of activities, resources, or services a user is permitted after they are authenticated.
- Accounting: Monitor the activity of the users on the site.
Train employees to take security seriously
To keep everyone and everything safe from security threats, all employees need to get on board with the security policies and measures the business has implemented. A business is vulnerable when a single key card is lost or stolen. A password is given to an outsider, or more obvious when an employee with a grudge accesses sensitive information and provides it to a competitor.
To protect the business, all employees can do is simply lock their workstations when they are unattended. Network admins can put rules to make this easier to comply with, which will be covered a bit later in the course.
You need to stay on top of the current technological thinking and innovations in network security to stay ahead of would-be attackers. The website, CERT NZ, has a section for IT specialists. It is an excellent place to stay on top of the latest threats to cyber security. Once you have opened the link, bookmark it for future use, then close the tab to return to this learning.
Authentication
Access control – authentication factors
Put policies, software or even hardware (a server dedicated to authentication) in place to make sure that only authenticated users can access your network
Controlling who does and does not have access is the cornerstone of every security operation.
The IT team will provide credentials to the user through authentication factors (such as a password or fingerprint recognition). When users attempt to access the network, they must satisfy the authentication requirements to log in to the network. As you would expect, each authentication factor must be unique to the individual requesting access. There are generally three types of authentication factors.:
- Something you know (e.g., a password)
- Something you have (e.g., a smart card)
- Something you are (e.g., your fingerprint).
1. Something you know – your password
Most online services require a password, so the concept will not be new to you. A username accompanies your password—the combination of which, when kept completely confidential, is a robust system if used properly.
Hackers have become extremely adept at 'guessing' passwords, and again, once the password is compromised, the system breaks down. For the password to be safe, it must be hard to guess, no matter how much computer power a potential attacker throws at the 'guesses.' This type of attack is referred to as a 'brute force attack.' The IT team can implement protocols that don't allow for weak passwords. For example, you may have noticed a red or green light indicating a weak (red) or strong (green) password when setting up access credentials for an online service, such as a bank. In that case, the IT team have put in parameters to keep your data safe.
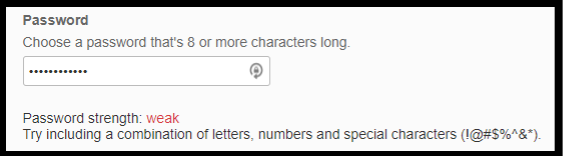
TradeMe have put in these parameters for their passwords to keep your account safe.
Hackers might not even try to guess the password—they might try and pretend to be an individual and then change the password to gain access. Security questions are often put in place to prevent this from happening.
To gain access to passwords or clues, hackers might resort to some savvy tactics:
- They might cycle through dictionary files containing popular words and phrases and attempt to log in with your email address or name as the username.
- They can investigate your background to look for likely passwords or answers to security questions such as anniversary dates and schools attended.
- Sophisticated outfits will fish for clues by posting personal questions on social media, such as "What was the number one song when you graduated high school?" Your answer supplies your approximate birth year. Or they might ask you to comment, "What was your first pet's name?" which you might even recognise as a standard security question. Answering may leave you vulnerable, so only that information to trusted sources.
- Hackers might steal username/password combinations from sites with weak security (maybe you signed up for a newsletter for dog lovers?) and then run the combination through a site with much greater security, such as your bank. Never reuse passwords.
The following rules make passwords difficult to guess:
- Unique – Every password used should be different from each other otherwise, if one is stolen, your entire online life could be vulnerable to hackers.
- Long and strong – between 8 and 14 characters at the minimum. Administrative accounts should have longer passwords.
- Four or more words – string words together to make a phrase you can easily remember
- Include numbers and symbols – Substitute numbers and symbols for the letters of your phrase. Also, use both upper- and lower-case letters. For example:
Phrase: Today is a great day to be me!
Password: 24ay!3aGR84ay2BeMe!$!
Personal password management
It can be very hard to remember all those passwords, and it's not a great idea to write them down or store them in a file on your computer in case it is stolen. In a Windows environment, the system can manage passwords that can be used with applications compatible with the Kerberos authentication mechanism used by the domain. This is referred to as single sign-on. The MAC uses 'Keychain', and individual browsers will offer to store them for you. There are also third-party options, such as LastPass and RememBear, which can be used across multiple devices to store and create robust logins. A good network security program will require the password to be changed periodically (usually 1x or 2x per year).
The following video by CERT NZ reiterates these ideas and best practices for password security.
BIOS/UEFI PASSWORDS
As mentioned previously, admin passwords require a more sophisticated approach. Examples are the Bios or Unified Extensible Firmware Interface (UEFI) system password required to boot the operating system.
2. Something you have – smart cards and tokens
A user can have a physical card or token. These chips are embedded in them that store account details in a digital certificate. A logon application loaded onto a card reading device ensures the credentials are legitimate before allowing access. Some are even more sophisticated and rely on radio frequency identification (RFID) which can be read wirelessly. Another token in use is the RSA SecurID, which uses a key fob and offers several factors to authenticate, including session-specific codes dynamically generated in real-time.
Can you think of the primary concern with access based on something you have?
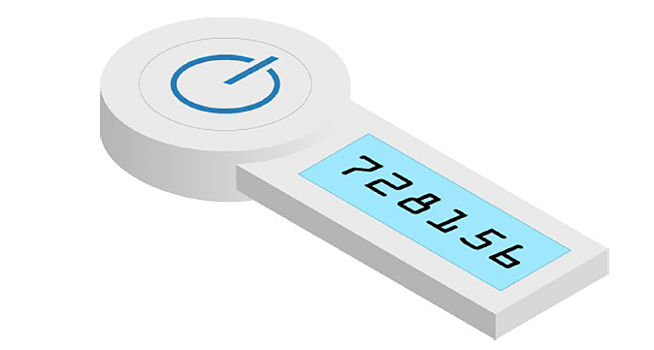
This SecurID key fob provides dynamic codes for a high level of security.
Did you wonder what would happen if you no longer have the physical access card or token due to loss or theft? That is the biggest risk with this type of authentication factor.

3. Something you are: biometrics
As with many other technological advances, biometrics keeps networks secure today. Many smartphones offer this same level of security, though it is also marketed as a convenience. Biometrics offers a way to ensure the person trying to gain access is the authenticated person. Several parts of the body can be scanned and recorded, e.g.,
- Fingers – fingerprints
- Eyes – retina or iris
- Face – facial recognition.
It is no longer science fiction to use irises and retina scanning to enter the most secure networks.
The drawback to this sort of authentication factor is that it isn't quite as foolproof as one might think, and there can be concerns about whether the person is, in fact, the authenticated individual. For example, a photo can trick some facial recognition scanning. Also, biometrics can be prone to false-positive and negative identification, admitting or denying access incorrectly.
Multifactor Authentication (2FA, 3FA)
Using more than one factor to authenticate a user has become the norm for many credentialing systems. We have provided several individual factors above, such as passwords, tokens, and fingerprints. Each of the factors on its own has vulnerabilities but used in combination with two or even three factors increases security greatly.
Can you think of a business you support that requires at least two factors? Write down the authentication factors and which type they are to get a sense of what you are already doing to protect your data.
Did you think of sites requiring you to enter a username and password combination (factor one) and a code automatically texted to your phone (factor two)? This combines something you know (your password) with something you have (your unique phone number) for strong security.
More than half of all enterprise companies use [multifactor authentication] to secure their sites, and more embrace the technology each year.Okta.com
A pin+keycard with a fingerprint reader is an example of three-factor authentication. The pin is something you know; the keycard is something you have, and the fingerprint is something you are.
Combining different factors is best
For a login to be 2FA, each authentication factor must be different. You cannot use two of the same type to be considered multi-factor. For example, a password and security question is still just one factor because both are categorised as something you know. A fingerprint and eye scan fall into the same issue.
Software tokens
Imagine if you were reading a news article behind a paywall and left the page for a moment to look up the definition of a word, and when you returned to the article, you had to sign in all over again. Or, at work, when you use the same password every single day, on the same computer, from the same network, you are booted out of the network every time your computer is unlocked. That would be frustrating.
The system can issue a software 'token' that enables the computer to bypass the login. It can last only a day, a week, or longer. Sometimes that is managed by the user themselves in the form of a checkbox that they can select if they would like to remain logged in for two weeks. Traditionally, this has been managed using 'cookies' stored on the local machine. However, more commonly now, it is JavaScript Object Notation (JSON) Web Tokens, called JWT. To prevent a replay attack (where an attacker obtains the token from someone's device, perhaps in transmission, and uses it to gain access under a false identity), the token is often retired at the end of the session, day, or another time limit.
Remote authentication
Enterprise-level companies have hundreds or thousands of users and many remote and wireless access technologies and devices to manage and synchronise.
Remote Authentication Dial-in User Service (Radius)
offers scalable authentication architecture. Under this protocol, AAA is performed by a dedicated server. Network access devices, such as routers, switches, wireless access points, or VPN servers, function as client devices of the AAA server. Rather than storing and validating user credentials directly, they pass this data between the AAA server and the user.
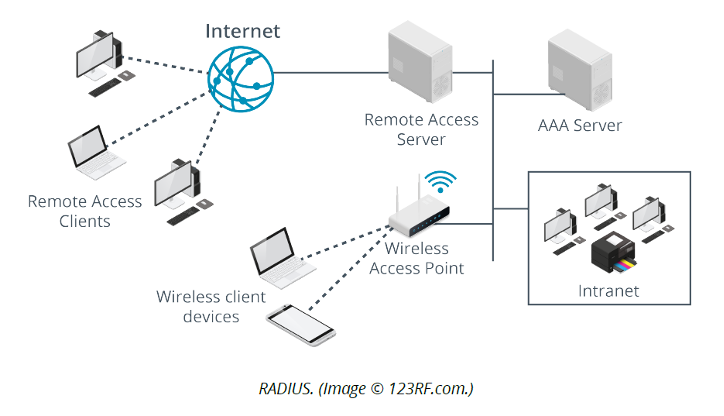
Terminal Access Controller Access Control System Plus (TACACS+)
is a similar protocol to RADIUS but designed to be more flexible and reliable. It is supported on many third-party and open-source RADIUS server implementations. Where RADIUS is often used to authenticate connections by wireless and VPN users, TACACS+ is often used in authenticating administrative access to routers and switches.
Authorisation
Once the user is in the system, the authorisation process handles the permissions of the account accessed. Does the user have the authority to perform the task they are attempting to do? Authorisation activities determine and configure the activities, resources, or services a user can access.
Accounting
While authenticated users access only areas, they are authorised to access, accounting measures the resources a user consumes while logged in. The amount of time in each session or the amount and nature of the data accessed is logged in the session statistics. This is used for oversight such as authorisation monitoring, billing, and capacity planning.
Password and account policies
We have discussed good password management on the user level, such as picking strong passphrases and not reusing passwords. Still, along with reminding users to be good security citizens, the network admins need to set up policies and protocols that enforce good behaviour (i.e., password complexity requirements).
Access Control List (ACL)
As the name suggests, this is a list of users and devices with access to the network. The list also indicates what privileges they have been granted to access resources such as files and directories or network connections in the case of a firewall ACL.
The following policies provide a best practice look at using ACLs:
- A computer used at home and work can be configured through Windows to recognise the network and prompt for a password in the office, but not at home.
- Change default admin user—rename default accounts so attackers cannot use
- known account names to access the system.
- Change default user passwords—as well as default usernames, appliances ship with
- a default password, such as "admin" or "password." To secure the device, you must
- change this when first setting it up.
- Restricting user permissions (least privilege)—least privilege is a basic principle of
- security stating that someone (or something) should be allocated the minimum
- necessary rights, privileges, or information to perform their role. Users can be
- configured either as administrators or standard users.
Windows local security policy and group policy
On a standalone workstation running Windows, password and account policies can be configured via the Local Security Policy snap-in (secpol. msc) or the Group Policy snap-in (gpedit.msc). On a Windows domain network, Group Policy Objects (GPO) can be saved as collections of group policy settings.
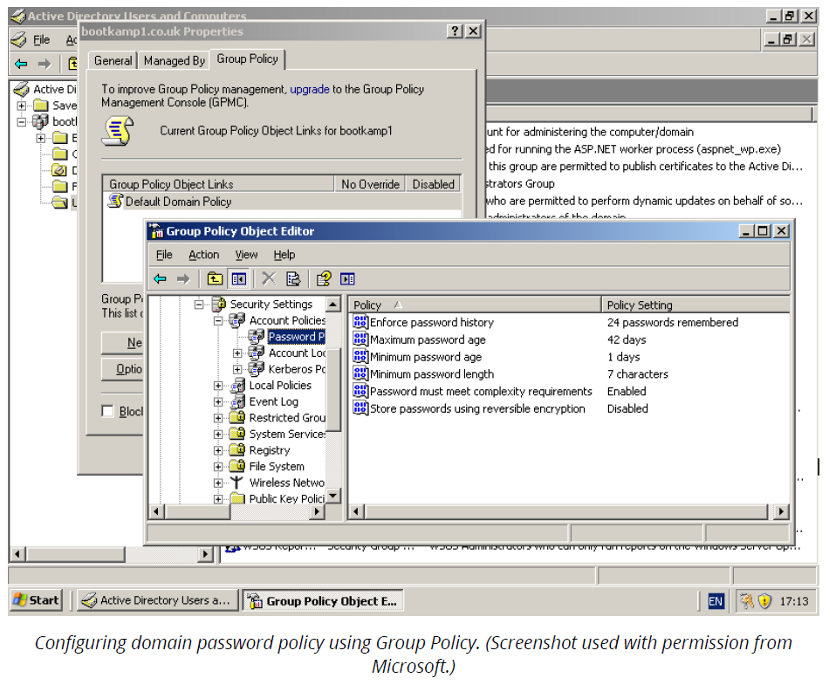
Account restrictions – limit authorisation
By restricting the user to areas of the network where they have a business need, you can help prevent breaches from spreading into sensitive areas. The following table provides good security practices while a user is in a session.
| Policy | Description |
|---|---|
| Logon time restrictions | Set time restraints on user accounts, so access to the server is restricted during certain times of the day or night. The server will make checks periodically to ensure the user still has the right of access and log them out if necessary. |
| Station restrictions | User access to the server can be restricted to a particular workstation or a group of workstations. |
| Concurrent logins | You can limit the number of connections to the network a single user can make at one time. Remember to consider mobile devices that may be used simultaneously as desktop machines. |
| Account expiration date | Setting an expiration date means that an account cannot be used beyond a certain date. This option is useful for accounts for temporary and contract staff. |
| Failed attempts lockout | The network administrator may specify a maximum number of incorrect sign-in attempts within a certain period. Once the maximum number has been reached, the server disables the account for a set amount of time or until the user contacts an administrator to enable it again. This helps prevent hackers from brute force attacks. |
Help users remember to lock unattended workstations
One problem with the credentialing system is that the system trusts the workstation entirely once signed in. If a user leaves the workstation unattended, someone else could take over the machine—sometimes referred to as a 'lunchtime attack'. To prevent the possibility of this happening, users should be trained to lock the workstation whenever they leave it.
The simple way to lock a Windows machine is to press Windows+L. Another way of locking the computer is to set the screen saver to require a password to dismiss it. The screensaver can also timeout and lock the desktop after an inactivity period. macOS have settings that enable the user to position the mouse in the corner of the screen to engage the screensaver, which can be configured to require the password to dismiss it.

The network administrators must have, at all times, a clear picture of what is going on in the network, who is doing it, and where they are doing it. Most companies have software or even dedicated machines to keep track of the systems running on the network and monitor their activity. In addition, a record must be kept of the data stored on each machine, so in the case of a breach, it is quick to resolve what exactly may have been compromised.
Simple Network Management Protocol (SNMP)
This is a framework for management and monitoring network devices. SNMP consists of:
- agents – a process that runs on an SNMP device
- management system – the software application that monitors and displays the activity of the agents
Agents
Each agent process maintains a database called a Management Information Base (MIB) that holds statistics relating to the activity of the device, e.g., the number of frames per second handled by a switch. The agent can also trigger 'trap operations', alerts or flags in the case of notable events, such as port failures or suspicious login activity.
Agents can be run on any SNMP-compatible device, such as a:
- Switch
- Router
- Server
The management system
This software program monitors all agents by polling them at regular intervals for information from their MIBs and displays the information for review. It also displays any trap operations as alerts for the network administrator. SNMP devise queries over UDP port 161; traps are communicated over UDP port 162.
This is a sketch of an SNMP system communicating with agents.
Endpoint management server
In the diagram above, the agents run on devices called' endpoints' within the networking framework, requiring security protocols. A security principle called defence in depth calls for policies that provide robust security to workstations (including mobile devices and printers) to ensure they cannot be compromised and used to attack the network. An endpoint management server facilitates this process by securely configuring the devices running on the network. These activities include:
- Applying OS and antivirus updates automatically
- cataloguing software applications installed on each device
- applying strong security policies
- retrieving and analysing log files
- monitoring performance and acting on status alerts.
Microsoft has the System Centre and Configuration Manager (SCCM) for Windows (plus support for other device types). Many other products provide this service.
Syslog
Capturing logs from connected devices is an important tool in network management. It is much easier to review logs and respond to alerts if the logs are consolidated in a single system. With the development of event subscriptions, logging can be configured to forward all events to a single computer, enabling holistic oversight of network events.
The equivalent system in UNIX and Linux is usually syslog. This system allows for a centralized collection point for events on various machines. It also provides an open format for event logging messages, which has led to it becoming the standard for logging events from various systems.
Here is an example of a Windows-based syslog from Stackify.com.
The preventative security measures that users can take, along with those the network administers put in place, such as firewalls with anti-malware scanners, will help stop problems from becoming disasters. Understanding what data is most useful to an attacker will ensure high risk or high impact areas of the business have strong security measures in place.
We previously mentioned that network security includes alerts when suspicious or simply unusual activity or traffic. Two systems will manage those activities, and each third-party solution adds its connectivity options for sensor placement, configuration, and reporting tools.
- An intrusion detection system (IDS)
- Intrusion protection system (IPS)
Intrusion detection system (IDS)
This system includes a sensor with an analysis engine that monitors network traffic for signs or threats to security policies. The network admin will need to program the signatures of known intrusion attempts and must be kept up to date to remain effective. IDS can use behavioural or heuristic (a method of detecting viruses by examining code for suspicious properties) techniques to expose active threats. Unlike a simple packet filtering firewall configured to recognise IP addresses and application protocol ports, a network-based IDS goes deeper and examines the contents of the application layer payload in the packet.
When an IDS detects a threat, it creates a log entry and can also send a text or other alert to an administrator if appropriate. One of the drawbacks of IDS detection is that it can provide too much information, and the alerts become pointless because there are too many of them, and the events that trigger them are not genuine threats.
Understanding the size, impact, or level of anticipated threat will help inform the decision to run the IDS on a server or computer or purchase a network appliance dedicated to it.
Intrusion Protection System (IPS)
An Intrusion Protection System (IPS) adds some sort of real-time blocking (aka shunning) functionality on top of the basic IDS. An IPS may drop packets, reset connections, or run a script to trigger a response on another server or network device, i.e., a firewall, switch, or router.
Many vendors supply IDS and IPS software and appliances (computers or devices dedicated to networking activities). The underlying detection engine for most of these products is based on either Snort, an open-source, free IDS for Linux and Windows or Suricata, which also includes network monitoring in its software package.
Unified threat management (UTM)
UTM combines several security systems and centralizes threat management, providing simpler configuration and reporting than isolated applications spread across several servers or devices.
In addition to IDS and IPS, UTM solutions usually offer the following features:
- Antivirus – leveraging databases of known virus signatures.
- Anti-malware – Known and new threats are managed by keeping the signature file up to date and rules that analyse the behaviour and characteristics of an information packet to detect malicious intent.
- Firewall – The first layer of protection between web services and the network. The firewall protects against viruses, malware, phishing attacks, spam, and intrusion attempts. They can also prevent malware from spreading across the network.
- VPN – A virtual network creates a private network that tunnels through a public network, giving users the ability to send and receive data through the public network without others seeing the data. All transmissions are encrypted, so even if someone were to intercept the data, they couldn't interpret it.
- Web filtering – You can exclude certain URLs from the network so users cannot send and receive data from them. This might be done according to business needs or culture. You can prevent employees from accessing social media or porn sites while on the network.
- Data Loss Prevention – You can configure the UTM to flag all attempts to download data without proper authorisation.
Major UTM vendors and products include Barracuda, Sophos, Check Point, Fortinet, Cisco Meraki, Juniper SRVX, and SonicWall.
There are two basic ways of implementing network connectivity for IDS and IPS or UTM server services and appliances:
- Install the appliance in line with the network—this means that all network traffic passes through the server or appliance, which allows it to block suspect traffic easily. The drawback is that a single appliance with so many functions could represent a massive incident if one of those functions were mission-critical. For example, if the forwarding function of the appliance were to fail, no traffic would be able to pass into or out of the network. This can be mitigated by using two or more appliances for redundancy.
- Install the appliance as a sensor—this means that the device has a tap or mirror that enables it to view the traffic passing over a network link or switch. This makes prevention slower and more complex as the device needs to trigger a script for the preventive action to be enacted by another device (switch, router, or firewall).
In both cases, the ability to deal with high traffic volumes is critical. If the device is overwhelmed by the traffic volume, it won't be able to inspect it all and could be allowing malicious traffic to pass undetected. A dedicated security appliance should perform better than running the security service on a server or router.
Imagine that you are the network administrator for a company called MedAlert that monitors health bracelets and dispatches medics in the case of a medical emergency. Any downtime in that scenario, where the offline monitoring system is mission-critical and the literal difference between life and death. Your continuity and contingency planning for this eventuality must include an entire backup system that can be called into action in a very short time. You need multiple redundancies to keep everything running so a catastrophic failure does not turn into a loss of life.
Most situations won't be anywhere near that dramatic, but each business has its services, and some of them may be critical to the business needs and the services they provide.
Ensuring that data, applications, client computers, servers, and all network appliances are accessible and in good working order is an important responsibility that rests with the IT team. You need a solid plan before hardware fails or a natural disaster strikes.
Disaster prevention and recovery
A disaster sounds like it must be referring to an 8.0 earthquake or 3-Alarm fire, but, depending on the circumstances, it could be anything from a loss of power to a network appliance to genuine disasters, such as fires, earthquakes, terrorism, or accidents. All organizations need to develop an effective, documented Disaster Recovery Plan (DRP) that accomplishes the following:
- Identify scenarios for natural and man-made disasters and options for protecting systems.
- Identify tasks, resources, and responsibilities for responding to a disaster.
- Train staff in the disaster planning procedures and how to react well to change.
When a disaster occurs, the recovery plan will swing into action to get the failed part of the network operational as soon as possible. Examples of these are:
- Disk fail? Swap it out.
- Network appliance failed? Remove and replace or repair the component asap.
- Data becomes corrupted or lost? Action your data restoration plan.
A backup strategy and disaster prevention and recovery must be made well in advance of any incident so you can act quickly and confidently in the case of an incident.
As part of disaster prevention, you will need to have these procedures.

A data backup plan
Ensure you have thought through the issues of hardware, location, connectivity, accessibility, and communication to ensure your backup procedures are robust.
Determine the level and content requiring backup
Perform backups of data and configuration files regularly, which might be hourly, daily, weekly, etc. This should be at the file and image level and critical applications.
- File-level backups allow the restoration of user-generated data files in a shared folder or user profile.
- Image-level backups record a whole installation (OS, third-party software and drivers, and custom settings), which can be used to reinstall a computer or recover a Virtual Machine (VM).
- A critical application backup saves data and settings kept by a specific software product. This is likely to involve a database backup.
Backup implementation
You will need to ensure the business needs are driving backup plans and activities. They involve budget issues, service levels, and the business impact of outages on various aspects of the network.
- Determine and document data retention needs in both the short and the long term.
- Determine whether you need to perform full+incremental or full+differential backups and execute accordingly.
- Create at least one custom recovery image for use in restoring a computer.
- Test backups after they are created.
- Perform a test restore and validate the files.
- Run an integrity check on the media, such as using chkdsk on a hard drive used for backup.
- Backup software can often be configured to perform an integrity check on each file during a backup operation.
- Perform an audit of files included in a backup against a list of source files to ensure that everything has been included.
- Determine where backups will be stored, locally and offsite, in more than one location
- Cloud services can be utilised for extra capacity, and they have disaster mitigation as part of the service.
- Document account recovery methods and communicate them to staff.
- Consider a password recovery mechanism for users who have forgotten a password.
- Ensure profile data is backed up so that it can be restored in the event of file corruption or damage to a disk. If a profile cannot be restored, the account would have to be recreated. In that case, you would need to have documented the security group memberships and permission so you can reassign them.
- There may also need to be some provision for configuring a backup and recovery key to restore encrypted data
Be aware that when you restore data from a backup, the data is only as current as of the backup you are restoring, so some data might need to be recreated.
Emergency responses
As a network administrator or IT support, all eyes will be on you in a network failure. Knowing exactly what you need to do in contingency situations will help you stay calm and help get services back up and running as quickly as possible.
If you have an advanced warning of an impending potential disaster, you should already be thinking about how you can protect data, equipment, and supplies specific to the expected incident. For example, a tornado warning may elicit a different response from flooding.
- Communicate emergency response actions
- Policies and procedures relating to human safety, facilities, and property protection should be immediately accessible, communicated, and actioned.
- Everyone in the organisation needs to be familiar with the location of the emergency exits and the appropriate responses to each of the emergencies discussed within the contingency plan.
You may not have advanced warning and be caught by surprise. You will need to prioritise actions based on the situation to minimise potential losses. In the case of an evacuation, you need to know what you have time to do and what needs to wait until that action can be performed safely. However, this is one suggestion; you will need to go over this with the business leaders to ensure it matches their expectations and priorities.
- Human safety issues (including evacuation from the building) and 'critical' personal belongings protection
- Records and software protection
- Electronic hardware and equipment protection
- Furniture and less critical records and property protection
Instructions
As an IT professional, you may be surprised to discover that you are in a great position to help a company deliver on their goals of Corporate Social Responsibility (CSR). Using the knowledge you have gained about networking best practices, consider the practical ways you can be a part of a corporation's efforts to participate in positive change for society.
MDPI.com, whose website says they are " A pioneer in scholarly, open-access publishing", published a paper called Municipal Social Responsibility of Statutory Cities in the Czech Republic. Its focus in the Czech Republic doesn't mean it isn't relevant here in New Zealand; rather, it highlights that social responsibility needs to be part of everyone's business worldwide.
The excerpt below is provided to examine the economic and environmental responsibility areas that offer opportunities for you to participate. Don't be limited by these ideas.
Economic responsibility
- Ensuring transparency and openness
- Care for the quality and safety of goods
- Creation and implementation of innovations
- Strengthening relations with owners, investors, suppliers, customers, and other stakeholders.
Environmental responsibility
- Saving energy and other resources
- Minimization of waste and support for recycling
- Support for the preservation of resources and biodiversity
- Preventing and correcting negative environmental impacts
- Encouraging initiatives promoting a responsible approach to the environment.
Share your ideas on the forum, describing the specific activities or behaviours that would help drive CSR in a business.

