In this topic, we will explore the fundamental concepts and techniques of cryptography, an essential field in ensuring the security and integrity of digital information.
Cryptography plays a vital role in protecting sensitive data and enabling secure communication across various networks. By the end of this topic, you will have gained a solid understanding of cryptographic techniques and their application in ensuring the confidentiality, integrity, and availability of data. These skills will be invaluable as you navigate the complex landscape of cybersecurity and contribute to safeguarding digital systems and information.
In the realm of cybersecurity, protecting sensitive information and maintaining the integrity of data is paramount. The fundamental concept that forms the basis of information security is the Triad of CIA (not to be confused with the Central Intelligence Agency):
- Confidentiality
- Integrity
- Availability
Watch the following video from Eye on Tech which further explains the CIA Triad:
By understanding and implementing the principles of the CIA Triad, individuals and organizations can establish robust security measures to safeguard their data and systems from unauthorized access, tampering, and disruptions. In this learning content, we will explore each element of the CIA Triad in detail and discuss how to achieve its objectives effectively.
These three elements are considered to be the most crucial elements of Cybersecurity. Let's review each component of the CIA Triad:
Confidentiality
Confidentiality refers to the protection of sensitive information from unauthorized disclosure. It ensures that only authorized individuals or entities have access to the data. Confidentiality measures aim to prevent data breaches, unauthorized data access, and information leakage.
Confidentiality can be achieved through the following mechanisms:
- Authentication with Authorization
- Encryption
Authentication Vs Authorization
Authentication and authorization are two distinct concepts in the realm of information security and access control. While they are closely related, they serve different purposes. Here's an overview of their differences:
Authentication
Authentication is the process of verifying the identity of a user or entity attempting to access a system, application, or resource. It confirms whether the claimed identity is valid or not. Authentication is typically performed by presenting credentials such as usernames, passwords, or other authentication factors (e.g., biometrics, tokens) to a system. The purpose of authentication is to ensure that the user is who they claim to be.
Examples of authentication mechanisms include:
- Username and password: The user provides a unique username and a corresponding password to prove their identity.
- Two-factor authentication (2FA): In addition to a password, a second factor such as a fingerprint scan, SMS code, or authenticator app is required.
- Biometric authentication: This involves using unique physical characteristics like fingerprints, facial recognition, or iris scans to authenticate a user.
- Single sign-on (SSO): Users authenticate once, and subsequent authentication is automated across multiple systems or applications.
Authorization (Access Control)
Authorization, also referred to as access control, is the process of granting or denying permissions and privileges to authenticated users or entities. Once a user's identity is confirmed through authentication, authorization determines what actions they are allowed to perform and what resources they can access within a system or application. The purpose of authorization is to enforce restrictions and protect sensitive information from unauthorized access.
Authorization can be based on various factors such as user roles, group memberships, permissions, or access control lists (ACLs). It defines the level of access a user has, and it can be specified at a granular level to restrict certain operations or data.
Examples of authorization mechanisms include:
- Role-based access control (RBAC): Users are assigned roles, and permissions are associated with those roles. Users inherit the permissions of their assigned roles.
- Access control lists (ACLs): Individual permissions are assigned to specific users or groups for finer-grained control.
- Attribute-based access control (ABAC): Access decisions are based on a set of attributes about the user, resource, environment, and other contextual information.
- Mandatory access control (MAC): Access decisions are based on a predetermined security policy enforced by the system, typically used in high-security environments.
Confidentiality in Practice: Two-Factor Authentication
Online banking is commonplace across most segments of society and while traditionally user IDs and passwords constitute standard procedure, to ensure confidentially and security, two-factor authentication (2FA) is becoming the norm.

Are you the person you say you are? Prove it …..Twice.
Two-factor authentication (2FA), also known as multi-factor authentication (MFA), is a security mechanism that adds an extra layer of protection to user accounts and systems. It requires users to provide two separate and distinct pieces of evidence to verify their identity, making it more difficult for unauthorized individuals to gain access. This provides a higher level of security than authentication methods that depend on single-factor authentication (SFA). 2FA is done by using two factors from the following categories:
- Something You Know: This factor refers to information that only the legitimate user should know, such as a password, a PIN, or the answer to a security question.
- Something You Have: This factor involves possessing a physical or digital device that is unique to the user, such as a mobile phone, a smart card, or a hardware token. This device generates a one-time code or receives a verification message that the user must provide during the authentication process.
- Something You Are: something physically inherent in the user like a fingerprint, facial, voice recognition, or iris scan.
Case Study: ASB Online Banking Two-Factor Authentication

In 2004, ASB was the first bank in New Zealand to introduce the concept of two-factor authentication. Initially, 2FA was implemented for any transfer over the value of $2,500 NZD to a third-party account. Customers would receive an eight-digit text message which needed to be entered online within three minutes to complete the transaction.
The ASB two-factor authentication system ‘Netcode’ was developed using technology from the US firm RSA Security.
Since 2004, 2FA has come a long way and in 2018 ASB partnered with VIX Verify to roll out a new biometric-based mobile app that allows customers to remotely verify their identity by comparing a selfie with a photo of their eligible driver's licence or passport.
Sources:
https://www.smh.com.au/national/nz-bank-adds-security-online-20041109-gdk2my.html
https://www.biometricupdate.com/201811/vix-verify-develops-biometric-mobile-id-app-for-asb-bank
Bimoteric Verification
Biometric verification is any means by which a person can be uniquely identified by evaluating one or more distinguishing biological traits. These biological identifiers include fingerprints, hand and earlobe geometries, retina patterns, voice prints and written signatures.
Common Types of Biometric Verification
- Facial recognition
- voice recognition
- fingerprint recognition
- iris scanners
- handwriting recognition
Other ways to keep data secure
- Applying encryption to the data
- Security tokens, key fobs or soft tokens
- Users can take precautions to minimize the number of places where information appears
- Minimize the number of times data is transmitted to complete a transaction
Integrity
Integrity focuses on maintaining the accuracy, completeness, and reliability of data. It ensures that information remains unaltered and consistent throughout its lifecycle. Integrity measures aim to prevent unauthorized modifications, data corruption, and tampering.
The data received is the same as it was sent (trustworthy and accurate).
There are two points during the transmission process during which the integrity could be compromised:
- during the upload or transmission of data
- during the storage of the document in the database or collection
File permission and user access control ensures unauthorized people cannot change data, and checksum and backup save data from non-human threats such as electromagnetic pulses or server crashes.
Availability
Availability refers to ensuring that authorized users have timely and uninterrupted access to the information and resources they require. It involves mitigating the impact of disruptions, system failures, or malicious attacks that can hinder access to data or services.
For a system to demonstrate availability, it must have properly functioning computing systems, security controls and communication channels. Systems defined as critical (power generation, medical equipment, safety systems) often have extreme requirements related to availability.
Critical System Requirements
These systems must:
- be resilient against cyber threats
- have safeguards against power outages
- have safeguards against hardware failures
- mitigate other events that might impact the system's availability
Availability for critical systems is best ensured by rigorously maintaining all hardware and staying up to date with all system upgrades. Providing bandwidth, preventing bottlenecks and providing disaster recovery is essential.
Types of attacks that relate to the CIA Triad
What can unauthorized people do?
- Interception: This is an attack on confidentiality. An unauthorized party could be a person, a program or a computer
DIAGRAM: Unauthorized access, monitoring, or capture of sensitive information while it is being transmitted or communicated between two parties.
- Modification: An unauthorized party not only gains access to but tampers with an asset. This is an attack on integrity.
DIAGRAM: Unauthorized access and changing values in the data file, altering a program, or modifying the contents of messages being transmitted in a network.
- Fabrication: An unauthorized party inserts counterfeit objects into the system. This is an attack on authenticity.
DIAGRAM: Insertion of spurious messages in a network or addition of records to a file
Best practices for implementing the CIA Triad:
Confidentiality:
- Data should be handled based on the organization's required privacy.
- Data should be encrypted using 2FA.
- Keep access control lists and other file permissions up to date.
Integrity:
- Ensure employees are knowledgeable about compliance and regulatory requirements to minimize human error.
- Use backup and recovery software.
- To ensure integrity, use version control, access control, security control, data logs and checksums, strong hashing algorithms
Availability:
- Use preventive measures such as redundancy, failover and RAID. Ensure systems and applications stay updated.
- Use CDN
- Backup on cloud
- Ensure a data recovery and business continuity (BC) plan is in place in case of data loss.
Read the following article by Tech Target on the CIA Triad
https://www.techtarget.com/whatis/definition/Confidentiality-integrity-and-availability-CIA
Search for RAID and its types (since it might be used to achieve the availability of data).
Cryptography is the science of using mathematics to encrypt and decrypt data.
Cryptography enables you to store sensitive information or transmit it across insecure networks (like the Internet) so that it cannot be read by anyone except the intended recipient.

The earliest known form of cryptography was used by Julius Caesar. While plotting to overthrow the Senate of Rome, Caeser would not trust his messengers and as such created a way to secure his message that only he ‘the sender’ and his generals ‘the recipients’ would have the cypher to decode the message.
Types of Cryptography
Cryptography can be broken down into three different types:
- Secret key cryptography
- Public key cryptography
- Hash functions
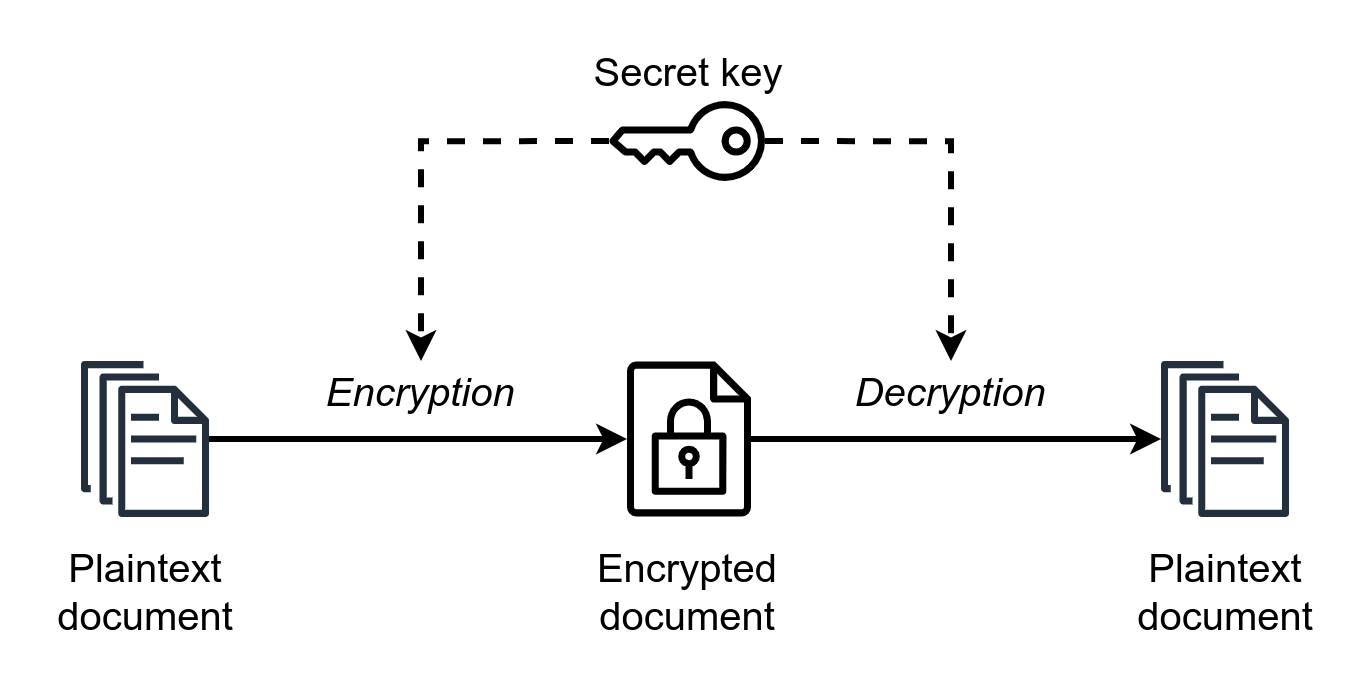
Encryption and Decryption
- Data that can be read and understood without any special measures is called plaintext or cleartext.
- The method of disguising plaintext in such a way as to hide its substance is called encryption.
- Encrypting plaintext results in unreadable gibberish called ciphertext.
- You use encryption to make sure that information is hidden from anyone for whom it is not intended, even those who can see the encrypted data.
- The process of reverting ciphertext to its original plaintext is called decryption.
The purpose of encryption is to protect the confidentiality and integrity of the information being transmitted or stored. Encryption ensures that even if an unauthorized entity gains access to the ciphertext, it cannot understand its contents without the corresponding decryption key
The following figure shows this process:
How Cryptography Works
- A cryptographic algorithm is a mathematical function used in the encryption and decryption process.
- A cryptographic algorithm works in combination with a key—a word, number, or phrase—to encrypt the plaintext.
- A cipher is a specific implementation or instance of a cryptographic algorithm, that combines algorithm and specific parameters, such as key length or initialization vectors.
- The same plaintext encrypts to different ciphertexts with different keys.
The security of encrypted data is entirely dependent on two things: the strength of the cryptographic algorithm and the secrecy of the key
Caeser’s Cipher
Ceaser created the first cryptography by shifting the letters of the alphabet by ‘3’. Only someone who knew the ‘Shift by 3’ rule could decipher these messages. Using Caeser’s key value of 3, we offset the alphabet so that the 3rd letter down (D) begins the alphabet.
A B C D E F G H I J K L M N O P Q R S T U V W X Y Z
+ sliding by 3 =
D E F G H I J K L M N O P Q R S T U V W X Y Z A B C
Using Caeser’s Cipher to encode the word ‘SECRET’ we must shift each letter by 3.
-
S = V
-
E = H
-
C = F
-
R = U
-
E = H
-
T = W
Thus, the encrypted message (ciphertext) then reads as:
“VHFUHW”
In order to decode the cypher text, the recipient must know the key, which in this rule is 3.
While this type of encryption is still used today, it is however considered weak cryptography. So, let’s explore and look at some more common counterparts.
Encryption Algorithms
An encryption algorithm is a mathematical procedure or set of rules used to transform plaintext (unencrypted data) into ciphertext (encrypted data) during the process of encryption. Encryption algorithms employ various techniques to ensure the confidentiality and security of sensitive information.
Encryption algorithms can be classified into two main categories:
- Symmetric Key Encryption
- Asymmetric Key Encryption
Symmetric Key Encryption
Symmetric key encryption, also known as secret key encryption, utilizes a single shared secret key for both encryption and decryption processes. The same key is used by the sender to encrypt the data and the recipient to decrypt it.
Symmetric cryptography provides a degree of authentication as long as the symmetric key is kept secret by the two parties.
If anyone other than the sender or the receiver finds the key, it affects both confidentiality and authentication. A person with an unauthorized symmetric key not only can decrypt messages sent with that key but can encrypt new messages and send them as if they came from one of the two parties who were originally using the key (fabrication).
Symmetric keys deal with data-at-rest, which is data stored in a static location, such as a database. Using data in a database as an example, while the data is stored in the database, it is encrypted with the symmetric key.
Data at rest
- File servers and network shares
- document management systems
- external storage
- databases
- endpoint, laptop, PCs
- mobile devices
- cloud storage
Key Management
Key management follows a lifecycle of operations, which is needed to ensure the key is created, stored, used, and rotated securely.
Most cryptographic keys follow a lifecycle which involves:
- Generation
- Distribution
- Use
- Storage
- Rotation
- Backup/Recovery
- Revocation
- Destruction
Advantages and Disadvantages of Symmetric Keys
Advantages
- Simplicity - Symmetric key encryption algorithms are relatively straightforward to implement and understand. The same key is used for both encryption and decryption processes, making it easier to manage and maintain the encryption system.
- Efficiency and Speed - Symmetric key encryption algorithms are generally faster and more computationally efficient. This makes symmetric key encryption ideal for encrypting large volumes of data or for real-time communication and data transfer.
Disadvantages
- Key Management – One of the primary challenges in symmetric key encryption is securely managing the shared secret key. If the key is compromised, an attacker can decrypt the encrypted data.
- Key Distribution - The process of securely sharing the key among authorized parties can be complex, especially in large-scale systems.
Let's look at an example of a Symmetric Key:
Alice and Bob (2 users) both agree on a shared secret key prior to the encryption of the information.
- In the case of Alice (sender) and Bob (receiver), symmetric encryption works just fine as there are only two entities.
- But what if Alice is gathering information from thousands of sources? She must manage thousands of keys (not practical) and if a key gets exposed during the distribution it creates a risk of hackers getting access to the sent message.
It is point 2 that creates the motivation for Asymmetric Cryptography.
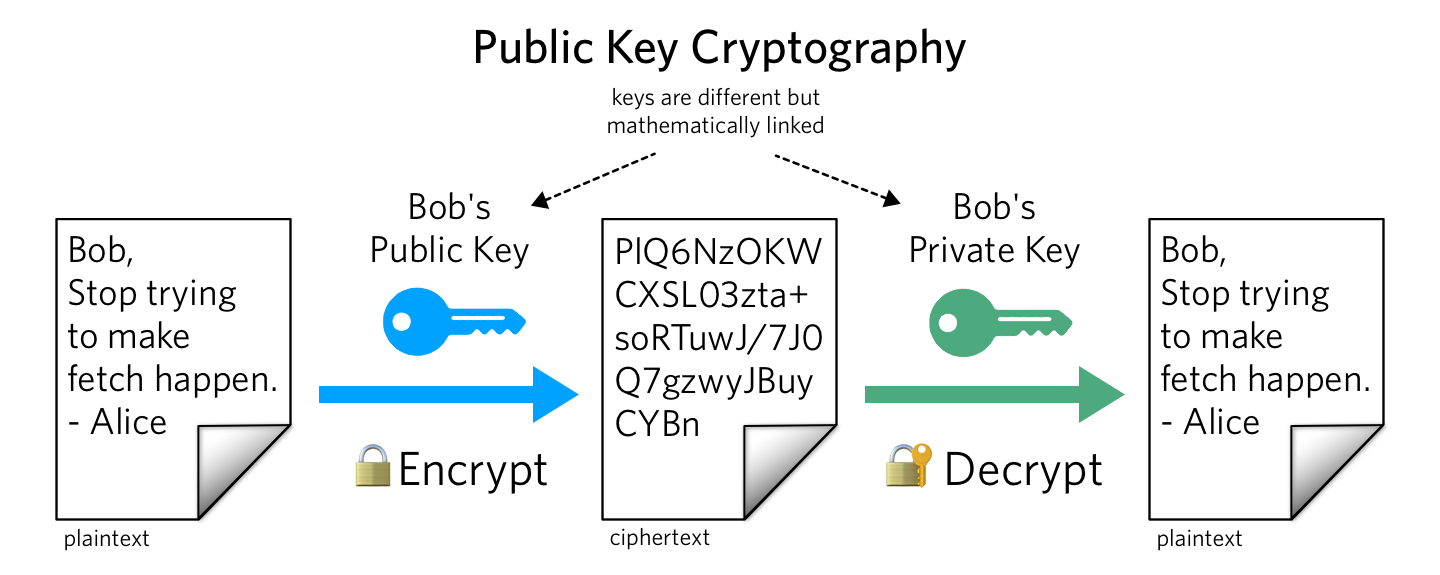
Asymmetric Key Encryption
Asymmetric key encryption also referred to as public key encryption, employs a pair of mathematically related keys: a public key and a private key. The public key is freely distributed, while the private key remains confidential to its owner. The sender uses the recipient's public key to encrypt the data, and the recipient uses their private key to decrypt it.
Let’s take a look again at the example of Alice and Bob but this time we are encrypting using Aysemmtric Encryption. There are 2 keys in asymmetric or Public-key cryptography: a Private key (used by the receiver) and a Public key (which is announced to the public).
Public and Secret Keys
Public-key encryption requires more calculations in comparison with symmetric-key encryption, it is important to note that public-key encryption is not always appropriate for large amounts of data.
Asymmetric keys focus on encrypting data-in-motion (data sent across a network connection, whether it be a public or private connection).
Data in Transit
- downloads/uploads
- LAN transfers
- file sync apps
- cloud
- collaboration tools
Advantages and Disadvantages of Asymmetric Keys
Advantages
- Message Authentication – As public key encryption allows using digital signatures, message recipients will be able to verify messages to be truly coming from a particular sender.
- Convenience – Asymmetric encryption solves the problem of distributing keys for encryption, with everyone publishing their public keys, while private keys being kept secret.
- Non-Repudiation – Digitally signed messages are like physically signed documents. Basically, it is like acknowledging a message, and therefore, the sender will not be able to deny having sent it.
- Tampering Detection – With digital signatures in public key encryption, message recipients can detect if a message was altered in transit.
Disadvantages
- Speed – Public key encryption in this method is slow compared with symmetric encryption, which means that it is not suitable for decrypting bulk messages.
- Public Key Authentication – Basically, no one absolutely knows that a public key belongs to the individual it specifies, which means that users will have to verify that their public keys truly belong to them. (This lead’s to the digital signature solution which will be covered later in this topic).
- Private Key Loss – Private key loss may be irreparable. When you lose your private key, your received messages will not be decrypted.
Key Types:
To recap, there are three key types:
- Secret keys (shared key for sender and receiver)(Symmetric-key cryptography)
- Private keys (used by the receiver)(Asymmetric-key cryptography)
- Public keys (which are announced to the public)(Asymmetric-key cryptography)
Summary:
| Symmetric Encryption | Asymmetric Encryption |
|---|---|
| Uses a single key to encrypt and decrypt the data. | Uses two separate keys for encryption and decryption. They’re known as “public key” and “private key.” |
| Is a more straightforward and conventional method of encryption. | Was invented to mitigate the risks of symmetric encryption and is more complicated. |
| Is faster when compared to asymmetric encryption, thanks to its simplicity. | Is slower and requires more computational power because of its complexity. |
| Requires smaller key lengths, usually of 128-256 bit length. | Asymmetric keys are longer. |
| Provides the confidentiality of the data (data security). | Provides confidentiality, authenticity, and non-repudiation. |
| Is useful for encrypting a large amount of data. | Is useful for encrypting a small amount of data. |
| Standard symmetric encryption algorithms are RC4, AES, DES, 3DES, and QUAD. | Standard asymmetric encryption algorithms are RSA, Diffie-Hellman, ECC, El Gamal, and DSA. |
Encryption algorithms are designed to be mathematically secure, making it computationally infeasible for unauthorized individuals to reverse-engineer the original data from the encrypted ciphertext without the corresponding key. The strength of an encryption algorithm is determined by factors such as the key size, the complexity of the algorithm, and the resistance to known attacks.
It is important to note that the security of encrypted data relies not only on the encryption algorithm but also on the secure management and protection of the encryption keys. Proper key management practices, including key generation, distribution, storage, and rotation, are crucial for maintaining the confidentiality and integrity of encrypted data.’
To learn more about cryptography and key management read the following articles
- https://www.shiksha.com/online-courses/articles/types-of-cryptography/
- https://doubleoctopus.com/security-wiki/encryption-and-cryptography/symmetric-key-cryptography/#:~:text=Examples%20of%20symmetric%20key%20cryptography,curve%20(EC)%20and%20RSA
- https://www.encryptionconsulting.com/education-center/what-is-key-management/#why-is-it-important
- Look for algorithms that use symmetric key cryptography
- Look for algorithms that use asymmetric key cryptography
- Look for the different states of data and how to protect the data in each state
A hash function is a function that takes a set of inputs of any arbitrary size and fits them into a table or other data structure that contains fixed-size elements. The result received is called a message digest. Message digests are designed to protect the integrity of a piece of data or media to detect changes and alterations to any part of a message.
A message digest is a cryptographic hash function containing a string of digits created by a one-way hashing formula. Message digests are designed to protect the integrity of a piece of data or media to detect changes and alterations to any part of a message. For example, verifying if a downloaded document is the same as the original.
The hash function is also used in digital signatures (authentication, non-repudiation, & integrity). It is important to note that a hash is NOT an encrypted version of the original text but rather it’s a 1-way trip, meaning that it’s impossible to recover the original message from the digest.
There are several different types of hashing algorithms used in the field of cryptography. Each type of hashing algorithm has its own characteristics and intended applications. Here are some commonly used types of hashing:
- Secure Hash Algorithms (SHA): SHA algorithms, such as SHA-1, SHA-256, and SHA-3, are widely used cryptographic hash functions. They produce a fixed-length hash value (digest) that is typically represented as a sequence of hexadecimal characters. SHA algorithms are designed to be secure and resistant to various attacks, including collision attacks.
- Message Digest Algorithm (MD): MD algorithms, including MD5 and MD6, are older hash functions that have been widely used but are now considered weak due to their vulnerabilities to collision attacks. While MD algorithms are still used in some non-cryptographic applications, they are not recommended for security-sensitive purposes.
Through the use of SHA different messages will never have the same hash and as such will not ever experience a collision.
Unlike SHA, the MD function is no longer utilised for security purposes. In 1996, it was identified that MD5 encountered a collision problem. The MD5 collision problem refers to the vulnerability in the MD5 (Message Digest Algorithm 5) cryptographic hash function where different inputs can produce the same hash value. In other words, it is possible to find two distinct messages that result in the same MD5 hash. This collision vulnerability undermines the integrity and security provided by the MD5 algorithm.
The discovery of MD5 collisions has significant implications for security. It means that an attacker can create two different files with the same MD5 hash, known as a collision attack. This allows the attacker to maliciously substitute one file for another without changing the hash value, potentially leading to various security breaches.
Due to its collision vulnerabilities, MD5 is no longer considered secure for cryptographic purposes, especially for applications where data integrity is critical. It is highly recommended to use stronger and more secure hash functions, such as the SHA-2 (Secure Hash Algorithm 2) family or SHA-3, which have been designed to resist collision attacks.
SHA256 Hash Example
- SHA256 hash
-256 bits/64 hexadecimal characters - My name is Professor Messer.
SHA 256 hash:
19da9a2e26f3bff67f0522f962851c4254b8659333ac53397c8d65aa7a3f871 - My name is Professor Messer!
54381cae1eea10892d81c8688d06d1928b4ee8495061a792864f83092b033aea
Through the following website, review the online tool SHA256 Hash Generator
https://passwordsgenerator.net/sha256-hash-generator/
As outlined earlier the issue with public key authentication is that no one absolutely knows that a public key belongs to the individual it specifies, which means that users will have to verify that their public keys truly belong to them. This has led to the development of digital signatures.
Digital signatures provide authenticity protection, integrity protection and non-repudiation.
Digital signatures:
- Prove the message was not changed
- Integrity
- Provide the source of the message
- Authentication
- Make sure the signature isn’t fake
- Non-repudiation
- Sign with a private key
- The message doesn’t need to be encrypted
- Nobody else can sign as a result
- Verify with the public key
- Any change in the message will invalidate the signature
It is important to note that digital signatures however do not provide confidentiality protection.
Let's take a look at another example of Alice and Bob and the creating and verifying a digital signature.
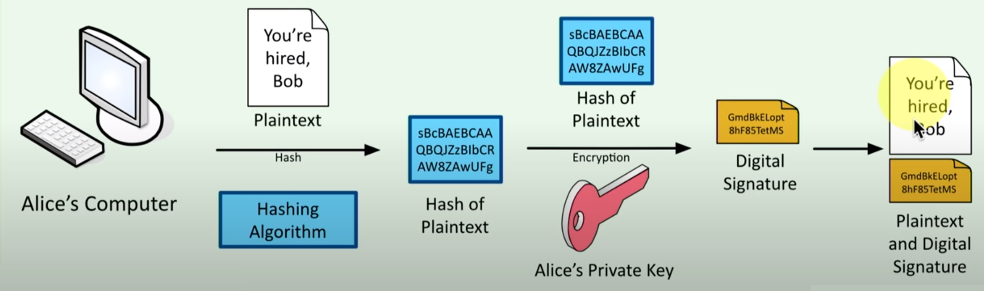
- Alice wants to digitally sign a document that she wants to send to Bob. The plaintext said: “You’re hired Bob”.
- Alice will hash that message to create a hash of the plaintext.
- Alice will encrypt that hash with a private key (no one else has access to this private key except her) the result is this digital signature.
- This is not an encrypted version of the plaintext. It’s common to create a digital signature and attach the digital signature to the plain text that you are sending to the other person (Bob).
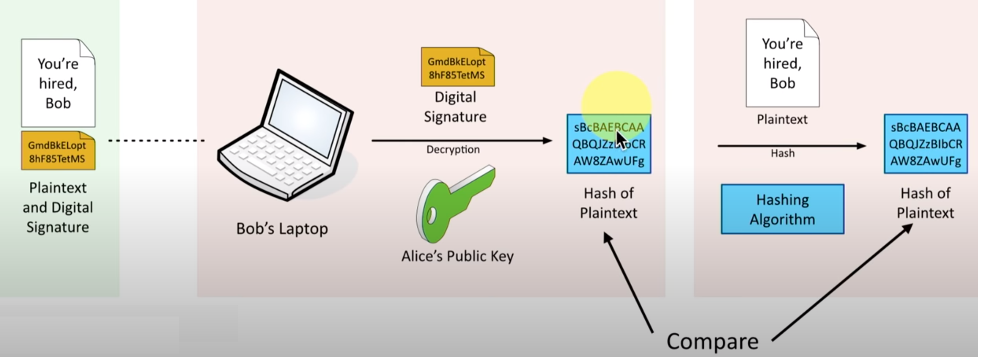
- Bob will take the digital signature received from Alice, and he will decrypt it using Alice’s public key. It will provide the original hash that Alice already created.
- Now Bob can use exactly the same plaintext that Alice sent and perform the same hashing function that Alice originally did, and come up with a hash of the plaintext.
- Bob will compare the hash function after the decryption and the hash that he performed. If they are both matched he knows that the digital signature is valid, meaning that the message came from the right person, and the message has not been tampered with along the way.
Public Key Infrastructure (PKI) is a globally accepted framework that utilizes public key cryptography to manage digital certificates, which are used to verify the authenticity and integrity of digital entities, such as websites, email servers, or individuals. PKI provides a trusted infrastructure for secure communication and is a crucial component in establishing secure connections over the internet.
Watch the following video from Practical Networking on PKI:
In PKI, we have:
- Sender: who requires a digital signature to sign a particular transaction.
- Registration authority: to whom you are going to register for a particular key. It also verifies the identity of the user.
- Certification authority: who signs / issues that key or that certificate.
- Verification authority: who validates the certificate. It does that after the certificate authority.
- Recipient: who is going to be the other party of that particular transaction.
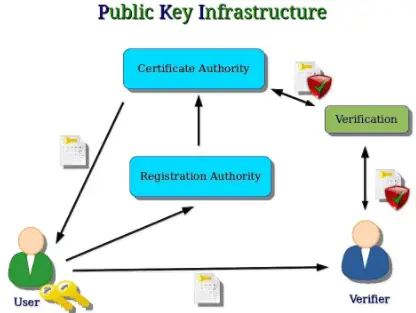
PKI and the ability to create digital certificates ensure that secure communications can occur over the internet. This is called Secure Sockets Layer (SSL).
What is an SSL?
SSL stands for Secure Sockets Layer and is a security protocol to establish an encrypted and secure communication link between a web browser and a web server.
For creating an SSL connection and activating it on your web server, you need a certificate, which is called an SSL certificate. It creates an encrypted connection between the server and the web browsers and establishes visitors’ trust.
Once the SSL certificate is installed by an organization on its web server, secure sessions are initiated with different web browsers, like Microsoft Edge, Google Chrome and Safari to name just a few. URLs that have SSL certificates display a padlock icon and as such the HTTPS protocol is activated, so that the visitors come to know that your website is secure.
The following situations require an SSL certificate on a website:
- To secure online transactions done using a credit card.
- To secure login information and other sensitive data filled by the users.
- To secure Outlook Web Access, Exchange and Office and other webmail and applications.
- To secure the file transfer over HTTPS and FTP(s) services, like when a large file is transferred.
- To secure cloud-based computing platforms or workflow and virtualization applications.
- To secure the connection between an email client and an email server, for example, Microsoft Outlook and Microsoft Exchange.
- To secure intranet traffic like internal networks, sharing files, database connections and so on.
- To provide security to the network logins and other network traffic with SSL VPNs or applications like access gateways.
To learn more about SSL and TLS read the following article
https://www.cloudflare.com/learning/ssl/what-is-https/
Look for SSL certificates of 4 URLs and list the name of the encryption algorithm that is used, and the name of the hashing function used and then post them to the forum ‘Learning Activity: SSL Certificate Research’