In this topic, we will delve into the world of cybersecurity threats and attacks, understanding the techniques used by malicious actors to compromise digital systems and networks.
Cybersecurity attacks pose significant risks to individuals, organizations, and even nations. As technology advances, so do the tactics employed by cybercriminals. Therefore, it is crucial to gain a comprehensive understanding of these attacks in order to effectively protect against them.
By the end of this topic, you will have gained a solid understanding of the several types of cybersecurity attacks, their underlying techniques, and their potential impact. Equipped with this knowledge, you will be better prepared to safeguard digital systems and networks against these evolving threats.
Before we dive into Cybersecurity attacks it is important to refresh your knowledge of the Open System Interconnection Model (OSI) and the 7 layers. Watch the following video and or read the article on the OSI model below.
https://www.imperva.com/learn/application-security/osi-model/
In the context of cybersecurity, risk, vulnerability, and threat are distinct concepts that collectively contribute to understanding and managing potential security issues.
- Risk - Risk refers to the potential for harm or loss resulting from the exploitation of vulnerabilities by threats. It involves assessing the likelihood of an incident occurring and the impact it could have on an organization's assets, systems, or operations.
- Vulnerability - A vulnerability is a weakness or flaw in a system, network, application, or process that can be exploited by a threat to compromise its security. Vulnerabilities can arise due to design flaws, programming errors, misconfigurations, or outdated software.
- Threat - A threat refers to any potential danger or harmful event that could exploit vulnerabilities and negatively impact the confidentiality, integrity, or availability of an information system or its data. Threats can come from various sources, including malicious actors, malware, natural disasters, technical failures, or human errors.
Risk = threat x vulnerability
In other terms, vulnerability refers to the likelihood of an attack being successful and threat refers to the severity of the impact of an attack if it were to occur. Before starting with risk mitigation and risk management, there is a need to understand the vulnerabilities and the threats to those vulnerabilities.
Types of attacks:
| 1. Denial of service 2. Distributed denial of service 3. Syn flood 4. UDP flood 5. Ping of death 6. Buffer overflow 7. Man in the middle 8. Session hijacking |
9. IP spoofing 10. ARP or cache spoofing 11. DNS poisoning 12. Replay attack 13. Social engineering 14. Phishing 15. Whaling attack 16. Malware attack |
17. Brute force 18. Dictionary attack 19. Birthday attack 20. Smurf attack 21. Bluejacking 22. SQL injection 23. XSS attack 24. CSRF attack |
A man-in-the-middle (MiTM) attack is a type of cyber-attack in which the attacker secretly intercepts and relays messages between two parties who believe they are communicating directly with each other. It usually comes during a connection to an unsecured or poorly secured wifi router.
![]()
It will allow the attacker to capture and manipulate sensitive personal information in real-time such as:
- login credentials
- card numbers
![]()
MiTM attack steps
- An attacker installs a packet sniffer to detect insecure network traffic
- Once the user logs into the insecure website, the attacker sends them to a fake website
- The fake website mimics the original website and collects all pertinent user data that the attacker uses on the original website
Types of MiTM attacks
- Wi-Fi eavesdropping: public Wi-Fi users get tricked into connecting to malicious Wi-Fi networks and hotspots. Cybercriminals accomplish this by setting up Wi-Fi connections with names that resemble nearby businesses.
- Internet Protocol spoofing: cybercriminals alter the source IP address of a website, email address or device.
- Cache / ARP spoofing: attackers send false ARP messages over the LAN to link the spoofer’s MAC address to a legitimate IP address of a computer or server on the network.
- URL spoofing: the attacker uses a domain (URL) that looks very similar to that of the target website in a way that the unsuspecting user is unlikely to notice the difference.
- Email spoofing: here, attackers alter the email’s header field to misrepresent who the real sender is. Email spoofs are always used as a part of phishing attacks where victims trust the source of the email and then they are tricked into clicking a malicious link.
- DNS spoofing: cybercriminals inject fake DNS entries into the DNS server, so when legitimate users access the server, they are sent to the injected DNS location, not their intended destination.
- Session hijacking: A.k.a stealing browser cookies, this malicious practice takes place when cybercriminals steal personal data and passwords stored inside the cookies of a user's browsing session.
- Replay attacks -A replay attack is a form of cyber attack where an attacker intercepts and maliciously resends valid data or communication to gain unauthorized access or manipulate a system or process.
Let's take a deep dive into each type of MiM attack.
Wi-Fi eavesdropping

In today's interconnected world, Wi-Fi networks are prevalent and widely used for seamless internet connectivity. However, these networks can be susceptible to security risks, with one notable threat being Wi-Fi eavesdropping.
Wi-Fi eavesdropping refers to the unauthorized interception and monitoring of wireless network traffic by an attacker. Attackers can capture and analyze Wi-Fi data packets transmitted between devices, potentially compromising sensitive information, such as usernames, passwords, or confidential data
Risks of Wi-Fi Eavesdropping:
- Data Interception: Eavesdroppers can capture unencrypted data packets transmitted over the network, allowing them to access sensitive information.
- Identity Theft: Attackers can gather personal information, login credentials, or financial details, which can lead to identity theft or unauthorized access to online accounts.
- Confidentiality Breach: Eavesdropping can expose confidential business data, trade secrets, or proprietary information, leading to financial losses or reputational damage.
Attackers utilize specialized software tools to capture and analyze wireless network packets, intercepting data transmitted over the airwaves. Eavesdroppers position themselves between the target device and the intended Wi-Fi network, intercepting and manipulating communication.
protect against Wi-Fi Eavesdropping
- Encryption: Enable WPA2 or WPA3 encryption on your Wi-Fi router to protect data transmitted over the network. Encryption ensures that data is securely encoded and unreadable to eavesdroppers.
- Secure Authentication: Implement strong and unique passwords for your Wi-Fi network and regularly change them to prevent unauthorized access.
- Public Wi-Fi Caution: Exercise caution when using public Wi-Fi networks, as they are more vulnerable to eavesdropping. Avoid accessing sensitive information or conducting financial transactions on unsecured public networks.
- VPN (Virtual Private Network): Use a VPN to establish an encrypted connection between your device and the network, ensuring secure communication even on untrusted networks.
- Network Monitoring: Regularly monitor your Wi-Fi network for any suspicious activities or unauthorized devices connected to it. Enable logging and intrusion detection systems to detect potential eavesdropping attempts.
IP Spoofing
IP spoofing involves altering the source IP address of network packets to impersonate another entity or mask the attacker's true identity. Attackers use IP spoofing to bypass security measures, launch various types of attacks, or perform covert activities, making it difficult to trace the origin of malicious activities.
Spoofing enables attackers to hide their true IP addresses, making it difficult for security systems to identify and trace the source of malicious activities. Spoofed IP addresses are often used in Distributed Denial of Service (DDoS) attacks, overwhelming target systems with a flood of network traffic, making it challenging to filter out legitimate requests. Attackers can also impersonate legitimate users by spoofing their IP addresses, gaining unauthorized access to sessions or intercepting sensitive information.
Techniques Used in IP Spoofing:
- Source IP Address Modification: Attackers manipulate the source IP address field in IP headers, forging packets to appear to originate from a different IP address than their actual source.
- IP Address Spoofing Tools: Various software tools and scripts allow attackers to automate the process of IP spoofing, simplifying the execution of spoofing attacks.
protect against IP Spoofing
- Filtering and Access Control: Employ ingress and egress filtering mechanisms at network boundaries to block or drop packets with spoofed IP addresses.
- Anti-Spoofing Measures: Implement techniques like Reverse Path Forwarding (RPF), which verifies that incoming packets have valid source IP addresses based on established routing tables.
- Network Monitoring and Intrusion Detection: Utilize network monitoring tools and intrusion detection systems to detect and alert on unusual or suspicious traffic patterns, including potential IP spoofing attempts.
- Strong Authentication and Encryption: Implement robust authentication mechanisms and encryption protocols to ensure the integrity and confidentiality of network communications.
- Educating Users: Raise awareness among users about the risks of IP spoofing and the importance of adopting secure practices, such as being cautious when clicking on suspicious links or downloading files.
Let's take a look at a real-life example of a Man-in-the-Middle Attack that occurred in 2014.
CASE STUDY: Man-in-the-Middle (MitM) attack

One notable real-life example of a Man-in-the-Middle (MitM) attack is the 2014 Superfish incident.
When: The incident occurred in early 2014.
Who: The attack primarily affected users of Lenovo laptops that were pre-installed with Superfish VisualDiscovery software. Superfish was a company that provided advertising software solutions.
What happened: Lenovo, one of the world's largest computer manufacturers, pre-installed the Superfish VisualDiscovery software on some of their laptops. This software was designed to inject visual search results and targeted advertisements into users' web browsers. To achieve this, Superfish employed a technique known as SSL hijacking, where it acted as a proxy between the user's web browser and secure websites.
The problem was that Superfish used a self-signed root certificate to intercept and decrypt the supposedly secure HTTPS traffic. This allowed them to read and modify the content of encrypted web pages. However, the use of a self-signed certificate meant that attackers could potentially exploit the system and perform MitM attacks by impersonating legitimate websites. Impact: The consequences of this MitM attack were significant. Users' encrypted web communications, including passwords, banking details, and other sensitive information, were vulnerable to interception by cybercriminals. Essentially, attackers who gained access to the self-signed certificate could decrypt and eavesdrop on the affected users' supposedly secure communications.
Impact: The incident caused a considerable outcry from the security community, and Lenovo faced widespread criticism for compromising user privacy and security. As a result, Lenovo released a statement acknowledging the security risks and provide instructions on how to remove the Superfish software and the associated root certificate from affected laptops.
The Superfish incident serves as a reminder of the dangers of MitM attacks and the importance of using trusted certificates and encryption protocols to protect sensitive data online.
- What steps could have been taken to prevent this incident?
- Was the incident adequately handled?
- What are other incidents of this type of attack?
ARP Spoofing
Address Resolution Protocol (ARP) spoofing is a deceptive technique used by attackers to manipulate the ARP tables on a local network. ARP spoofing involves falsifying ARP messages to associate an attacker's MAC address with the IP address of another device, leading to the redirection of network traffic intended for the targeted device.
Attackers employ ARP spoofing to intercept sensitive information, conduct man-in-the-middle attacks, or perform network reconnaissance.
By redirecting network traffic, attackers can capture and analyze sensitive information such as login credentials, financial data, or unencrypted communications. ARP spoofing allows attackers to position themselves between communicating parties, enabling them to intercept, modify, or inject malicious content into the traffic. Spoofing the ARP tables can also cause network connectivity issues, leading to service disruptions or denial of service for legitimate users.
Techniques Used in ARP Spoofing:
- ARP Cache Poisoning: Attackers send falsified ARP messages, associating their MAC address with the IP address of the targeted device, poisoning the ARP cache of other devices on the network.
- Gratuitous ARP: Attackers send unsolicited ARP replies, falsely claiming ownership of an IP address and causing other devices to update their ARP tables with the attacker's MAC address.
protect against ARP Spoofing
- Static ARP Entries: Manually configure static ARP entries on critical devices, binding specific IP addresses to their corresponding MAC addresses, and preventing unauthorized changes.
- ARP Spoofing Detection Tools: Utilize network monitoring tools capable of detecting ARP spoofing attacks, alerting administrators to potential spoofing attempts.
- ARP Spoofing Prevention Techniques:
- ARP Spoofing Detection and Prevention: Implement network intrusion detection and prevention systems (IDS/IPS) capable of detecting and blocking ARP spoofing attacks in real time.
- Port Security: Enable port security features on network switches to bind MAC addresses to specific ports, limiting the ability of attackers to spoof MAC addresses.
- Network Segmentation: Divide the network into smaller segments or VLANs to limit the impact of ARP spoofing attacks and contain their scope.
- Encryption and Authentication: Implement encryption protocols and strong authentication mechanisms to secure network communications and prevent unauthorized access.
URL Spoofing
URL (Uniform Resource Locator) spoofing is a deceptive technique used by attackers to manipulate or falsify URLs with the intention of misleading users and redirecting them to malicious websites. URL spoofing involves creating a fraudulent or deceptive URL that appears legitimate to users, leading them to believe they are accessing a trusted website or service.
Attackers employ URL spoofing to trick users into divulging sensitive information, such as login credentials, financial details, or personal data, or to deliver malware.URL spoofing is often used in phishing campaigns where attackers masquerade as legitimate organizations, aiming to trick users into revealing sensitive information. Attackers may use spoofed URLs to distribute malware by tricking users into downloading malicious files or visiting compromised websites. URL spoofing also allows attackers to create fake websites that closely resemble legitimate brands, deceiving users and damaging the brand's reputation.
Techniques Used in URL Spoofing:
- Domain Name Deception: Attackers register domain names that closely resemble legitimate ones by altering characters, adding subdomains, or using alternative top-level domains (TLDs).
- URL Obfuscation: Attackers use techniques like URL shortening services, obfuscated code, or redirects to disguise the true destination of the URL.
- Homograph Attacks: Attackers employ characters from different character sets that visually resemble legitimate characters to create misleading URLs.
protect against URL Spoofing
- User Awareness and Education: Educate users about the risks of URL spoofing, emphasizing the importance of verifying website authenticity, avoiding clicking on suspicious links, and practising caution when providing personal information.
- Secure Web Browsing Practices:
- Check the URL: Examine the URL carefully, looking for misspellings, unusual characters, or deviations from the legitimate domain.
- Hover Over Links: Hover the mouse cursor over a link without clicking to preview the destination URL and ensure it matches the expected website.
- Enable Browser Security Features: Utilize browser features like anti-phishing filters or extensions that warn about potentially harmful websites.
- DNS Monitoring and Protection: Implement DNS security measures such as DNSSEC (DNS Security Extensions) to verify the authenticity of DNS responses and prevent DNS hijacking.
- Web Filtering and Anti-Malware Solutions: Employ web filtering tools and anti-malware solutions that detect and block access to known malicious websites.
- Domain Monitoring and Brand Protection: Regularly monitor domain registrations and employ brand protection services to identify and take action against spoofed domains.
Email Spoofing
Email spoofing involves forging or altering the email header information, including the "From" address, to make the message appear as if it is sent from a trusted source.
Attackers use email spoofing to deceive recipients, gain their trust, and trick them into taking certain actions, such as revealing sensitive information or clicking on malicious links.
Email spoofing is commonly used in phishing campaigns, where attackers impersonate reputable organizations to trick recipients into providing sensitive information or performing malicious actions. Attackers may spoof the email of a company executive or a trusted business partner to deceive employees into initiating unauthorized financial transactions or sharing confidential data. Spoofed emails can also contain malicious attachments or links that, when clicked, lead to the download or installation of malware on the recipient's device.
Techniques Used in Email Spoofing:
- From Address Manipulation: Attackers alter the "From" field to display a forged email address that appears to be legitimate or trustworthy.
- Domain Name Spoofing: Attackers use similar domain names or subdomains that closely resemble legitimate ones to trick recipients.
- Reply-To Address Modification: Attackers change the "Reply-To" address to direct responses to a different email address, allowing them to intercept and manipulate communication.
protect against and identify Email Spoofing
- Check Email Sender Details:
- Review "From" Address: Scrutinize the "From" address for any anomalies, misspellings, or suspicious domain names.
- Verify Domain Authenticity: Validate the legitimacy of the sender's domain by comparing it to the known official domain.
- Be Wary of Suspicious Content:
- Analyze Email Content: Look for grammatical errors, unusual language, or requests for sensitive information.
- Assess Urgency and Tone: Be cautious of emails pressuring immediate action or using threatening language.
- Examine Email Headers: Review the email headers to check for inconsistencies or signs of manipulation.
- Implement Email Authentication Protocols:
- SPF (Sender Policy Framework): SPF validates the authenticity of the sender's domain by verifying the IP address authorized to send emails on its behalf.
- DKIM (DomainKeys Identified Mail): DKIM adds a digital signature to emails, allowing recipients to verify the integrity and authenticity of the message.
- DMARC (Domain-based Message Authentication, Reporting, and Conformance): DMARC provides additional protection by combining SPF and DKIM, specifying how to handle emails that fail authentication checks.
- User Awareness and Education:
- Train users on email security best practices, such as avoiding clicking on suspicious links or attachments and reporting potential spoofed emails to the IT department.
- Promote scepticism and critical thinking when evaluating email requests, especially those involving sensitive information or financial transactions.
DNS Spoofing or Poisoning
DNS spoofing ( a.k.a DNS cache poisoning) is an attack in which altered DNS records are used to redirect online traffic to a fraudulent website that resembles its intended destination. Attackers can poison DNS caches by impersonating DNS nameservers, making a request to a DNS resolver, and then forging the reply when the DNS resolver queries a nameserver.
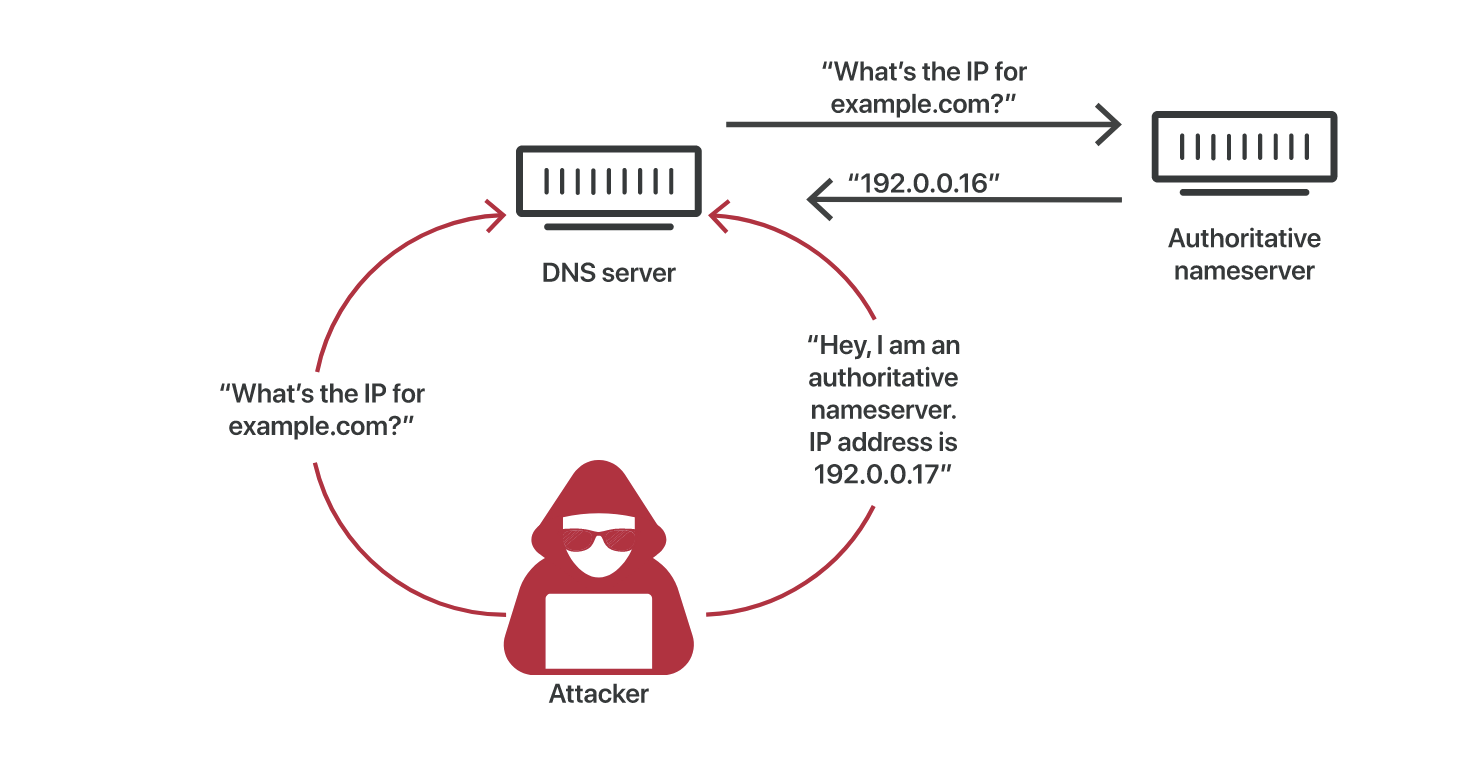
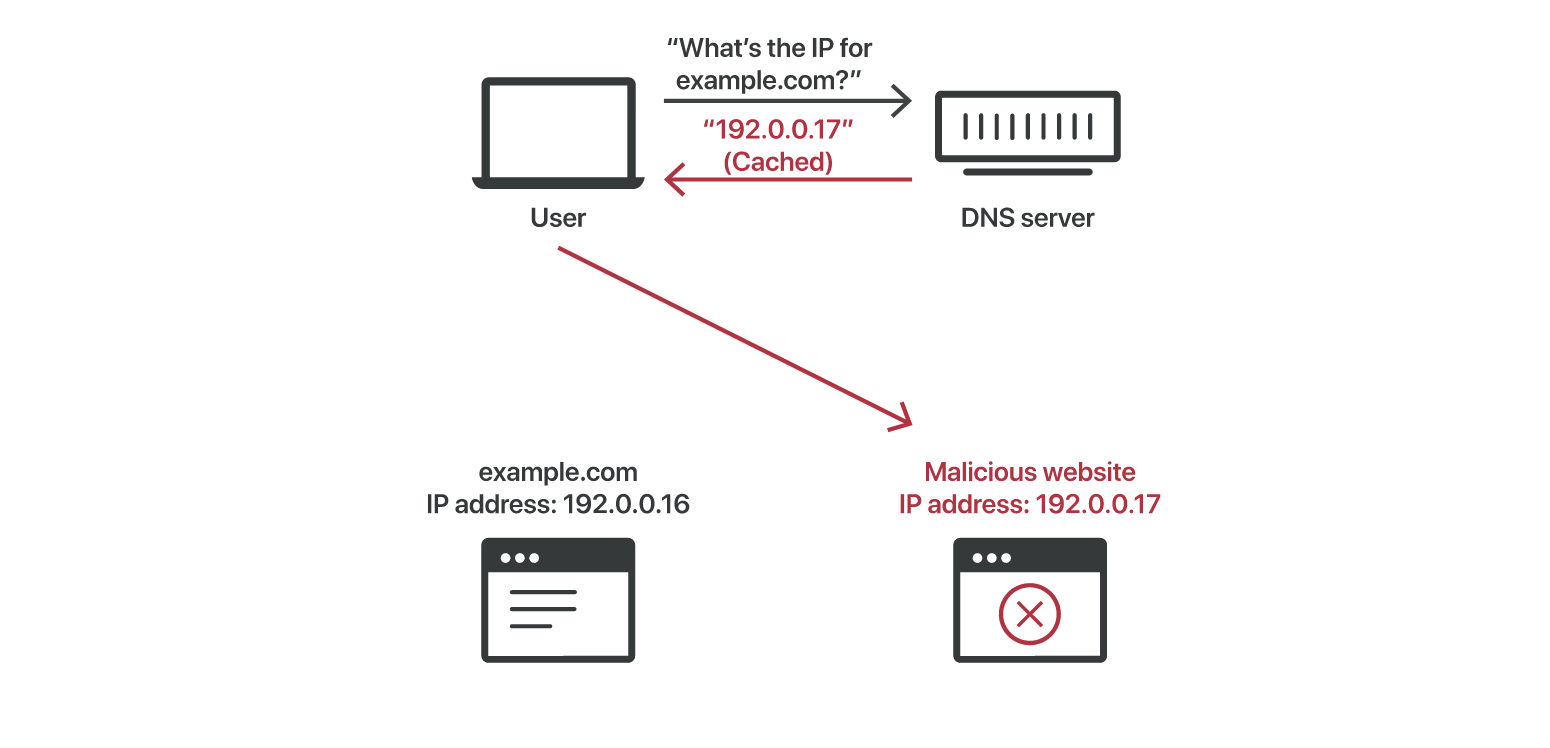
protect against DNS poisoning

- Use Cloudflare’s DNS : 1.1.1.1 or Quad 9 DNS: 9.9.9.9 :
- a public DNS resolver that uses DNSSEC
- offers a fast and private way to browse the Internet.
- Unlike most DNS resolvers, 1.1.1.1 does not sell user data to advertisers.
- DNSSEC short for Domain Name System Security Extensions, verifies DNS data integrity and origin.
- DNS was originally designed with no such verification, which is why DNS poisoning is possible.
- Much like TLS/SSL, DNSSEC uses public key cryptography (a way of digitally signing information) to verify and authenticate data.
Session Hijacking
Session hijacking, also known as session stealing or session sidejacking, is a type of attack where an unauthorized individual intercepts and takes control of a user's active session on a network or web application. In this attack, the attacker aims to exploit vulnerabilities or weaknesses in the session management process to gain unauthorized access to the session and impersonate the legitimate user.
![]()
Here's how session hijacking typically occurs:
- Session Identification: When a user logs into a web application or network, a session is established, and a unique session identifier (session ID) is generated. The session ID is used to authenticate and track the user's activities during their session.
- Interception: The attacker intercepts the session ID, often through various means such as eavesdropping on network traffic, capturing cookies, or exploiting security vulnerabilities in the application.
- Session ID Usage: With the intercepted session ID, the attacker can impersonate the legitimate user by injecting the session ID into their own browser or using it to forge requests. This enables the attacker to gain unauthorized access to the user's session and perform actions on their behalf.
- Exploitation: Once the attacker has control over the session, they can potentially access sensitive information, manipulate data, perform unauthorized transactions, or carry out other malicious activities within the compromised session.
There are different techniques used for session hijacking, including:
- Session Sniffing: The attacker captures network traffic to intercept and obtain session IDs or authentication credentials.
- Session Sidejacking: The attacker steals session IDs from unencrypted network connections or compromised devices to gain unauthorized access.
- Cross-site Scripting (XSS): By injecting malicious scripts into a website, the attacker can hijack session information from unsuspecting users.
protect against Session Hijacking
- Encrypting network traffic using secure protocols (e.g., HTTPS) to protect session data during transmission.
- Implementing secure session management practices, including the use of unique and randomly generated session IDs, session timeouts, and regular session reauthentication.
- Applying secure coding practices to prevent common vulnerabilities like XSS that can lead to session hijacking.
- Monitoring network traffic for suspicious activity, such as multiple concurrent logins or unusual session behaviour.
By implementing these measures, organizations and individuals can strengthen their defences against session hijacking attacks and help ensure the integrity and confidentiality of user sessions.
Replay Attacks
A replay attack is a subset of MiTM attacks and is when third-party intercepts and “replays” a secure data transmission, allowing the third party to interact with the receiver as though they were the original sender.
Let's take a look at an example:
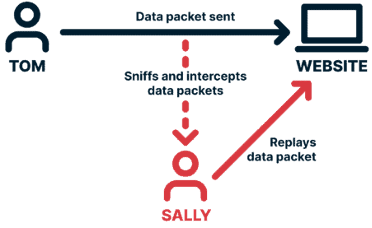
- Tom sends a login request to a website—the login request is verified, and Tom can log in.
- Sally intercepts the login request without Tom or the website being aware.
- Sally doesn’t even need to read the contents of the request; she can simply “replay” it.
- To the website, it will appear as though Tom is logging in again, and Sally’s login request (as Tom's) will be successful.
protect against Replay Attacks
- Using a one-time password (OTP) is one option because—as the name suggests—the password can only be used once.
- Adding a timestamp that’s only valid for a short amount of time can also prevent a hacker from launching a replay attack.
- Ensure you only access websites that use HTTPS protocol helps protect data, and avoiding public or free Wi-Fi also helps you stay protected online.
- Use a VPN to prevent hackers from eavesdropping in the first place.
How to Prevent MiTM Attacks:
- Avoid Public Hotspot: Avoid using public WiFi to protect the integrity of your sessions and opt for secure wireless networks.
- Use a VPN: A VPN helps prevent attackers from intercepting traffic, making it more difficult for them to steal session IDs.
- HTTPS: The use of HTTPS ensures that there is SSL/TLS encryption throughout the session traffic. Attackers will be unable to intercept the plaintext session ID, even if the victim’s traffic was monitored. It is advised to use HSTS (HTTP Strict Transport Security) to guarantee complete encryption.
- Implement a Strong Encryption Point with Wi-Fi Protected Access (WPA/WPA-2): WPA can secure your wireless network from MitM attacks.
Watch the below video for a more detailed overview of MiTM attacks.
Read the following article on WEP Vs WPA-1, WPA-2
https://www.avast.com/c-wep-vs-wpa-or-wpa2#:~:text=The%20WPA%20Wi%2DFi%20protocol,packet%2C%20or%20unit%20of%20data
6. Research the difference between WEP and WPA protocols.
A Denial-of-Service (DoS) attack is an attack meant to shut down a single machine or network, making it inaccessible to its intended users. DoS attacks accomplish this by flooding the target with traffic or sending it information that triggers a crash.
DDoS:
A distributed denial-of-service (DDoS) attack occurs when multiple machines are operating together to attack one target or one system by sending fake traffic.
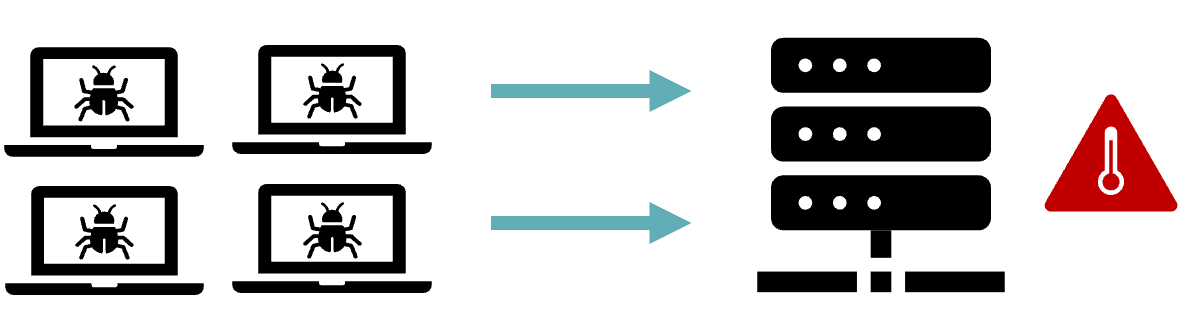
The attack starts when an attacker identifies a vulnerability in one master system. Then, they gain access to other vulnerable systems by introducing malware or bypassing authentication controls. DDoS attackers often leverage the use of a botnet —a group of hijacked or infected internet-connected devices to carry out large-scale attacks.
The host of infected systems is called a bot or zombie.
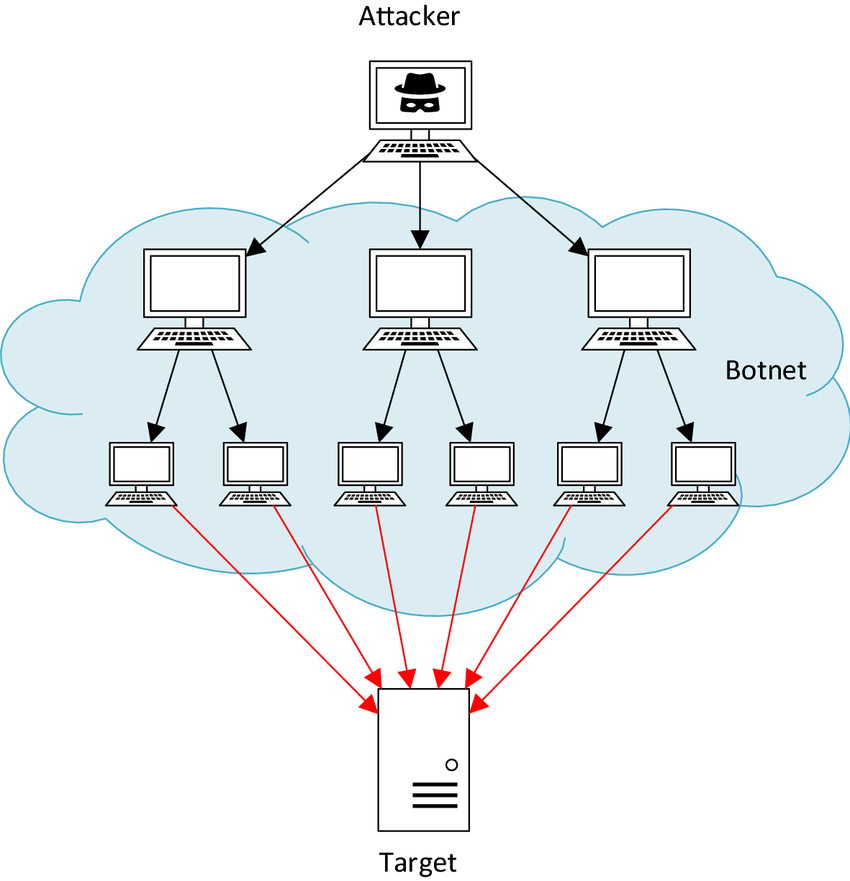
How a DDos attack works
Network resources (such as web servers) have a finite limit to the number of requests that they can service simultaneously. Additionally, the channel that connects the server to the Internet will also have a finite bandwidth/capacity. Whenever the number of requests exceeds the capacity limits of any component of the infrastructure, the level of service is likely to suffer in one of the following ways:
- The response to requests will be much slower than normal.
- Some /or all users’ requests may be totally ignored.
In general, DDoS attacks can be segregated by which layer of the Open Systems Interconnection (OSI) model they attack. They are most common in the Network (Layer 3), Transport (Layer 4), Presentation (Layer 6) and Application (Layer 7) Layers.
Protect Against DDoS Attacks
- Increase bandwidth to ensure there is enough bandwidth to handle traffic spikes that may be caused by cyber-attacks.
- Use a Content Delivery Network (CDN) or Multi CDN
- Implement server-level DDoS protection. Some web hosts include server-level DDoS mitigation tools in their offering
- Monitor, analyse network traffic & Bullet-proof your network hardware configurations(Firewall, IDS):
- Limit ICMP or UDP packets on your network hardware configurations:
- block DNS responses from outside your network to protect against some DNS from volumetric attacks
- set up rules that create alerts for unusual traffic
- Use an anti-DDoS Service provider to try to filter out junk traffic created by cyber criminal
- Use a Web Application Firewall (WAF): web application firewall that can be deployed on CloudFront to help protect your application against DDoS attacks by giving you control over which traffic to allow or block by defining security rules.
Content Delivery Network
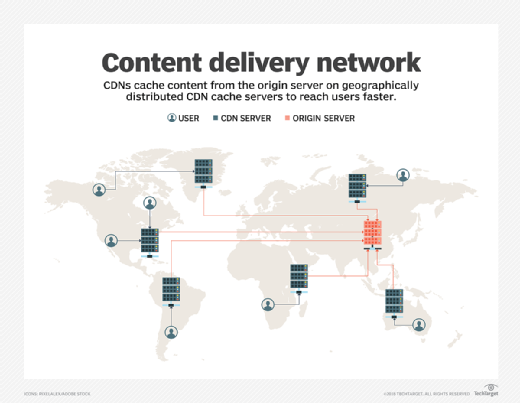
A Content Delivery Network is a distributed network of servers strategically located in different geographical locations to deliver web content and data to users more efficiently and effectively. The primary purpose of a CDN is to improve website performance, enhance user experience, and handle high traffic loads by reducing latency and minimizing the distance between the content and the end user.
A CDN works by caching and distributing content across its network of servers. When a user requests a specific web page, file, or media resource, the CDN serves the content from the server that is geographically closest to the user, reducing the time it takes for the content to reach the user's device. This proximity ensures faster content delivery and decreases the burden on the origin server hosting the website.
A multi-CDN refers to the use of multiple CDN providers simultaneously to further optimize content delivery. With a multi-CDN approach, content is distributed across multiple CDN networks, leveraging the strengths and capabilities of each provider. This strategy enhances performance, redundancy, and resilience by leveraging the combined infrastructure of multiple CDNs.
By utilizing multiple CDNs, organizations can achieve broader geographic coverage, minimize reliance on a single provider, and dynamically route traffic based on real-time performance metrics. This approach allows organizations to select the most optimal CDN for specific regions or situations, ensuring the best possible content delivery performance and user experience.
Categorizing protocols by TCP/IP model
Categorizing protocols by the TCP/IP model involves classifying network protocols based on the layers defined in the TCP/IP networking framework. The TCP/IP model consists of four layers, namely the Network Interface layer, Internet layer, Transport layer, and Application layer. Each layer performs specific functions and encompasses various protocols that facilitate communication between networked devices. Here's a breakdown of the protocol categories within the TCP/IP model:
- Network Interface Layer: This layer handles the physical transmission of data and addresses protocols that govern how network devices interact with the underlying network hardware. Protocols such as Ethernet, Wi-Fi (802.11), and Token Ring fall under this category.
- Internet Layer: The Internet layer deals with the logical addressing and routing of data across different networks. The primary protocol at this layer is the Internet Protocol (IP), responsible for assigning IP addresses to devices and enabling packet routing between networks. Other protocols, such as Internet Control Message Protocol (ICMP) for error reporting and Internet Group Management Protocol (IGMP) for multicast group management, are also part of this layer.
- Transport Layer: This layer focuses on end-to-end communication and ensures reliable data transfer between devices. The Transmission Control Protocol (TCP) is a prominent protocol in this layer, offering connection-oriented and reliable delivery of data. Additionally, the User Datagram Protocol (UDP) provides connectionless and unreliable transmission. These protocols enable applications to establish communication channels and manage data delivery.
- Application Layer: The Application layer contains protocols that support specific application services and functionalities. This layer encompasses a wide range of protocols, including the Hypertext Transfer Protocol (HTTP) for web browsing, File Transfer Protocol (FTP) for file transfers, Simple Mail Transfer Protocol (SMTP) for email transmission, Domain Name System (DNS) for domain name resolution, and many more. These protocols enable various applications to interact with the network and exchange data.
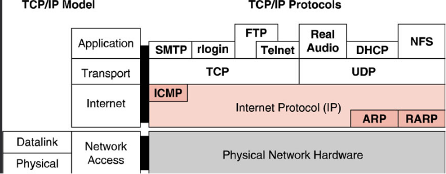
Categorizing protocols by the TCP/IP model helps in understanding the functionality and purpose of each protocol within the networking architecture. It provides a structured approach to organizing and discussing network protocols, facilitating the implementation, troubleshooting, and management of networked systems based on the TCP/IP framework.
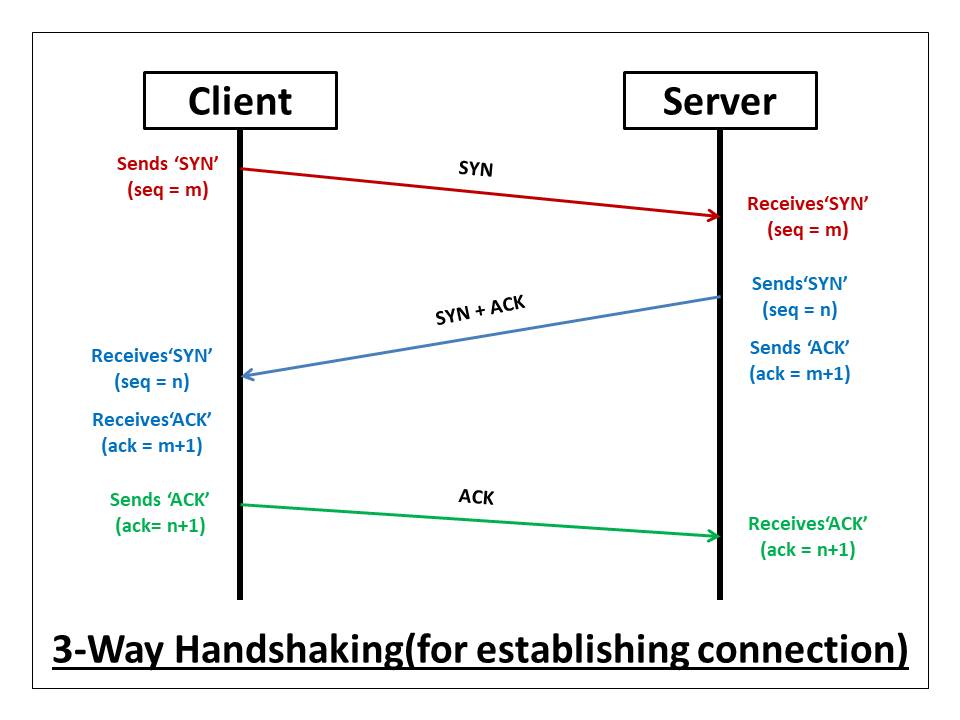
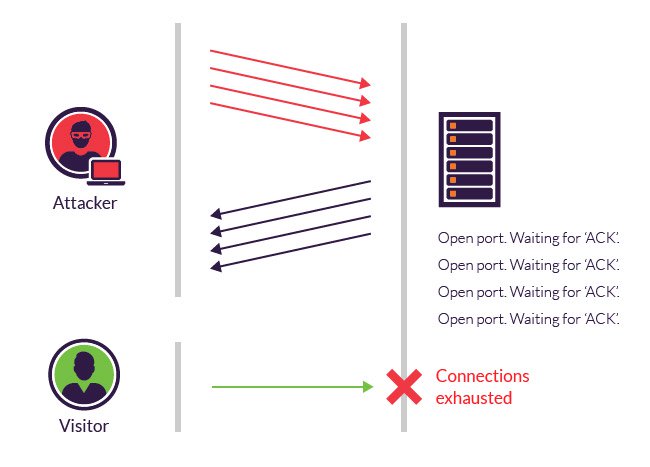
Syn Flood Attack
An SYN FLOOD attack is a type of DDoS attack that opens many connections with the target server and then never closes them. The attacker, acting as a client, sends a SYN message, when the server responds with a SYN-ACK the malicious client never sends an ACK message.
In this way the server is forced to keep numerous connections open, taxing its resources until it fails.
Categories of DDoS attacks
| Attack Types | Description | Example(s) |
|---|---|---|
| Volume-Based Attacks | Volume- Based Attacks are attacks that use high traffic to flood the bandwidth of a network. |
|
| Protocol Attacks | Protocol Attacks are attacks that consume server resources. |
|
| Application Attacks | Application Attacks are attacks that target the application layer and pile on requests until the web server crashes |
|
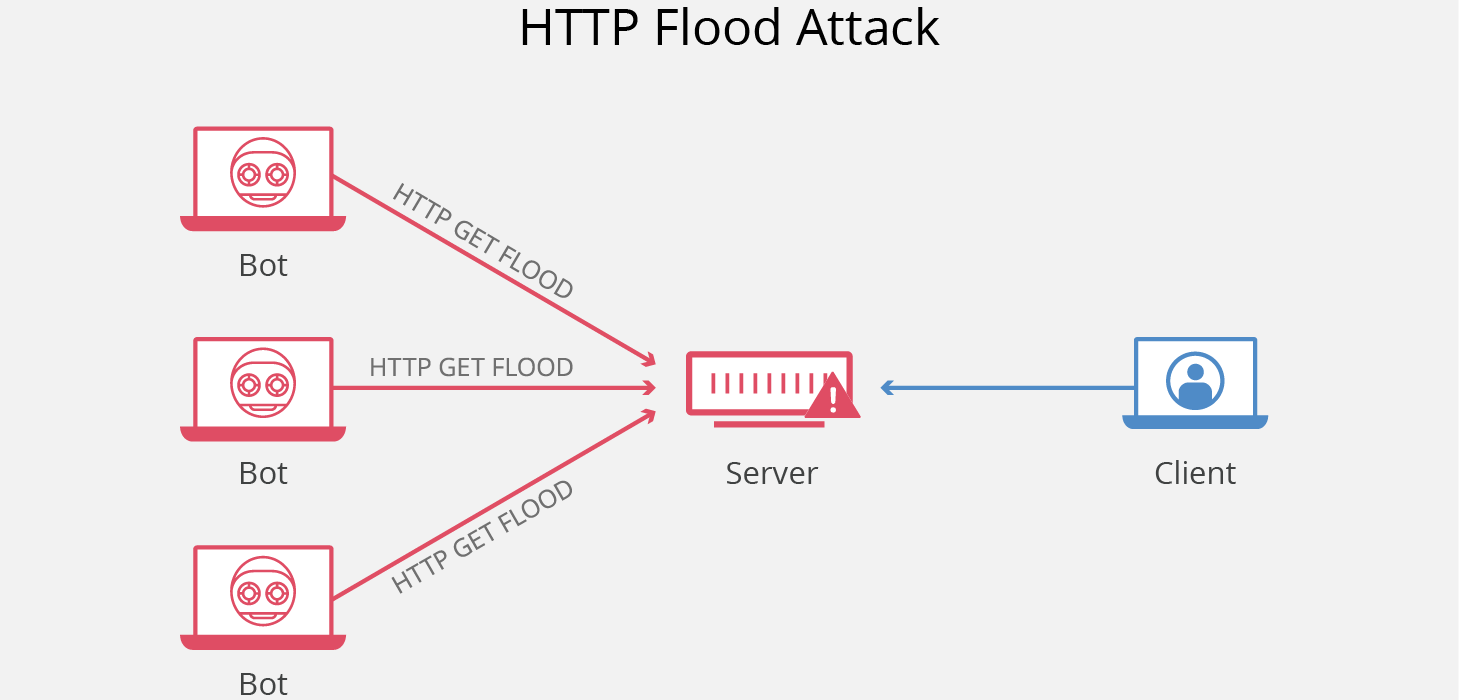
Smurf Attacks
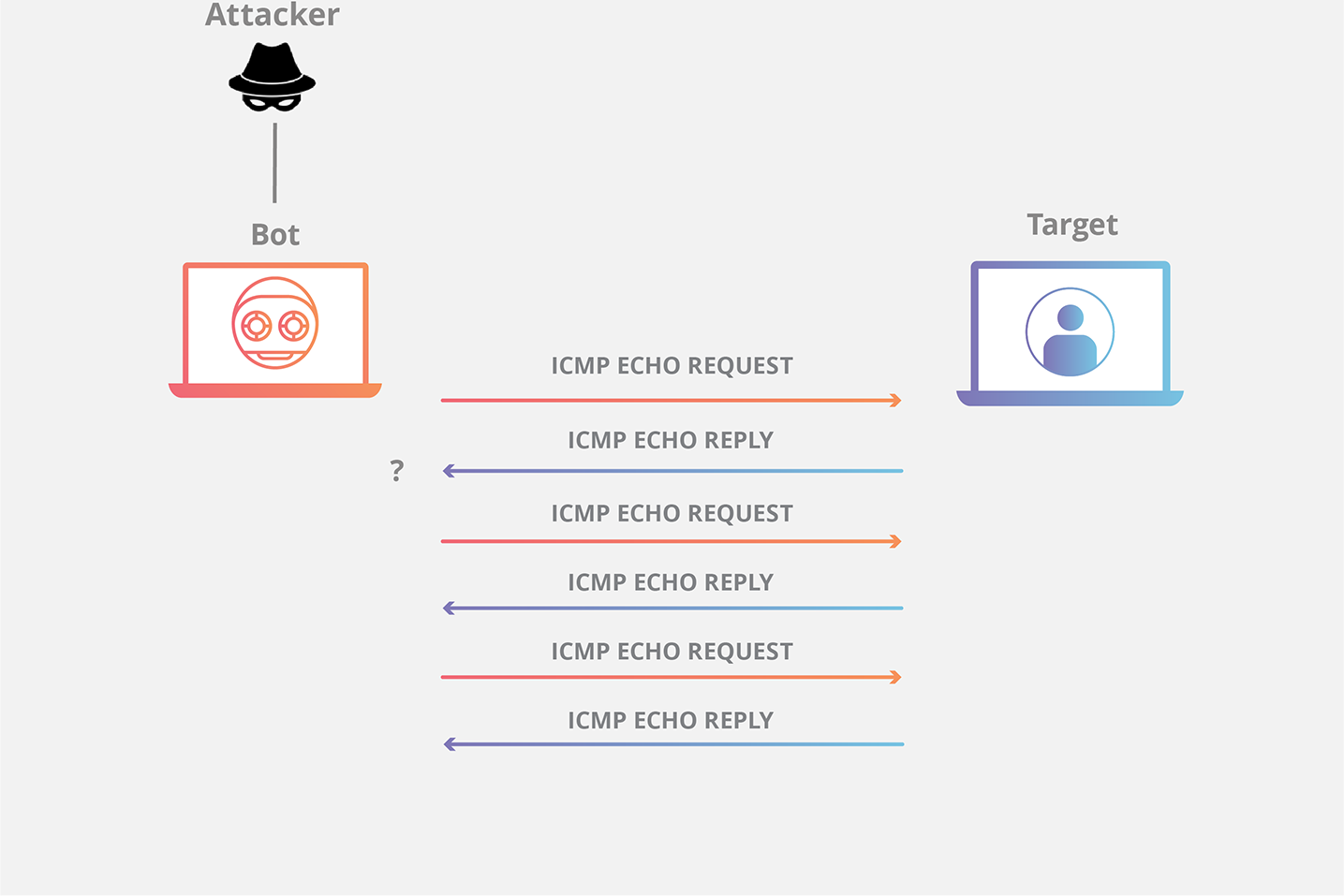
A smurf attack is a DDoS attack that sends packets spoofing the victim's source IP. When devices on the network attempt to respond, the amount of traffic slows the targeted device to the point of being unusable.
This type of attack is named after the cartoon character "The Smurfs” because of their ability to take down larger enemies by working together.
Smurfing attacks are named after the malware ”DDoS.Smurf”, which enables hackers to execute them.
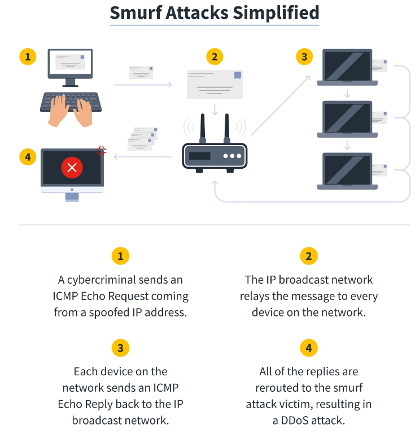
How a Smurf Attack Works
- “DDoS.Smurf” malware creates an ICMP Echo Request coming from a spoofed IP address that routes back to the smurf attack victim.
- The ICMP Echo Request is sent to an IP broadcast network that then relays the message to every device on the network, eliciting ICMP Echo Replies.
- The devices send ICMP Echo Replies back to the IP broadcast network, indicating the ICMP Echo Request has been received.
- All of the replies are rerouted to the Smurf attack victim, resulting in a DDoS attack.
Protect against Smurf Attacks
- Hosts and routers in a network can be configured not to respond to ICMP requests or broadcasts.
- Routers can also be configured not to forward packets directed to IP broadcast addresses.
- Ingress filtering can also be used to block packets in the network that come from outside the network but use source IP addresses that belong to the network.
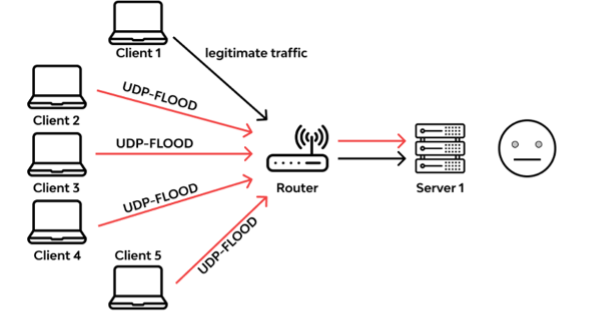
UDP Flood Attacks
Under normal conditions, when a server receives a UDP packet at a particular port, it goes through two steps in response:
- The server first checks to see if any programs are running which are presently listening for requests at the specified port.
- If no programs are receiving packets at that port, the server responds with an ICMP (ping) packet to inform the sender that the destination was unreachable.
What is a UDP flood attack?
A UDP flood is a type of denial-of-service attack in which a large number of User Datagram Protocol (UDP) packets are sent to a targeted server with the aim of overwhelming that device’s ability to process and respond.
The receiving host checks for applications associated with these datagrams and—finding none—sends back a “Destination Unreachable” packet. As more and more UDP packets are received and answered, the system becomes overwhelmed and unresponsive to other clients.
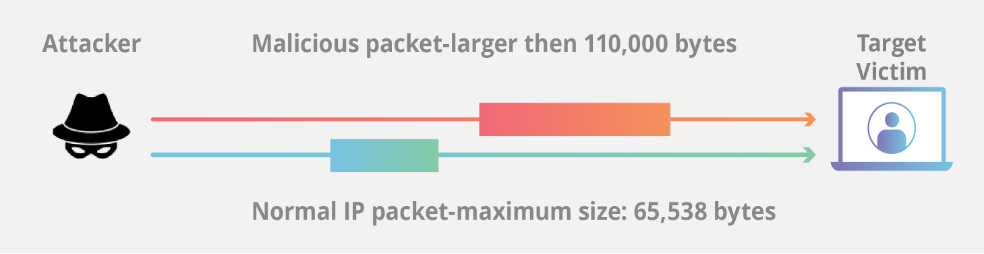
Ping of Death Attack
Type of denial-of-service (DoS) attack, in which the attacker aims to disrupt a targeted machine by sending a packet larger than the maximum allowable size, causing the target machine to freeze or crash.
When the target machine attempts to put the pieces back together of the malicious packets, the total exceeds the size limit and a buffer overflow can occur, causing the target machine to freeze, crash or reboot.
The original ping-of-death attack is less common today, but a new Ping of Death attack for IPv6 packets for Microsoft Windows was discovered and patched in mid-2013.
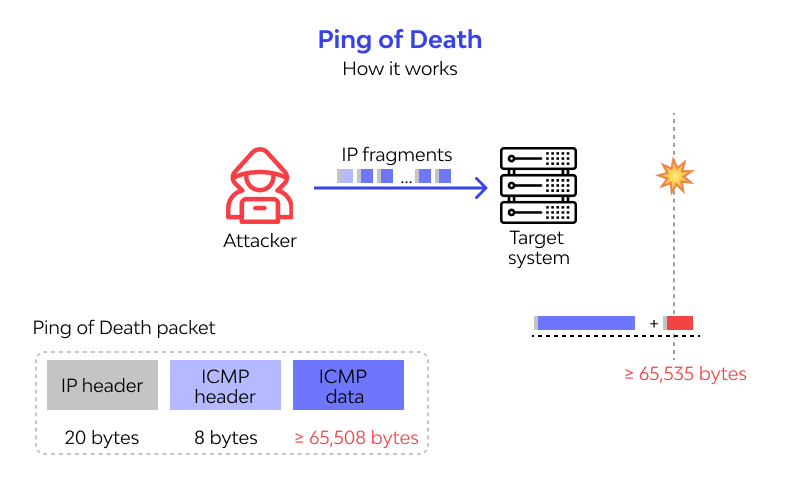
Protect against Pin of Death Attacks
- Add checks to the reassembly process to make sure the maximum packet size constraint will not be exceeded after packet recombination.
- Create a memory buffer with enough space to handle packets which exceed the guideline maximum.
- Cloudflare DDoS Protection mitigates Ping of Death attacks by dropping malformed packets before they reach the targeted host computer
DDoS Attach Types
| DDoS Attacks | Description |
|---|---|
| UDP Flood | UDP floods target the User Datagram Protocol by sending UDP packets to a given port on a target computer or network. When the host checks for the so-called application at that port, there's nobody there. Note: UDP reflection attacks like Memcrashed amplify DDoS attacks by orders of magnitude. Here's one way to stop them. |
| SYN Flood | These attacks go after Transmission Control Protocol (TCP) weaknesses by spoofing synchronized messages to start three-way handshakes with the target network that never closes. |
| Ping of Death (POD) | A Ping of Death sends malicious pings to a target system; these aren't so effective today because many of the weaknesses that allowed for successful exploits have been patched. (Remember—always, always patch your systems!) |
| Smurf Attack | These attacks exploit Internet Protocol (IP) and Internet Control Message Protocol (ICMP) with malware called Smurf that spoofs an IP address in order to ping a given network. |
| Slowloris | Slowloris attacks use HTTP flooding to take down web servers with minimal cost to the attacker, which is one reason these types of attacks often feature in hacktivist DDoS events. |
| Zero-Day | Zero-day DDoS attacks exploit vulnerabilities that have yet to be patched. |
CASE STUDY: Denial-of-Service (DoS) and Distributed Denial-of-Service (DDoS) attack

One significant real-life example of a Denial-of-Service (DoS) and Distributed Denial-of-Service (DDoS) attack is the Mirai botnet attack in 2016.
When: The attack occurred in October 2016.
Who: The attack targeted a managed DNS service provider called Dyn, which provides DNS infrastructure support to numerous major websites and services.
What happened: The Mirai botnet attack involved a large-scale network of compromised Internet of Things (IoT) devices, such as cameras, routers, and DVRs. These devices had been infected with malware, which allowed them to be controlled remotely by the attacker.
The attacker used the Mirai botnet to launch a coordinated DDoS attack against Dyn's infrastructure. By flooding Dyn's DNS servers with an overwhelming amount of traffic, the attack disrupted the DNS resolution process. As a result, many high-profile websites, including Twitter, Netflix, Reddit, GitHub, and others, experienced widespread service outages and became inaccessible to users.
Impact: The Mirai botnet attack had a significant impact on the availability of numerous popular websites and services. Users experienced difficulties accessing these platforms, and businesses suffered financial losses due to disrupted operations. The attack highlighted the vulnerability of IoT devices, which often have weak security measures, making them susceptible to compromise and use in large-scale DDoS attacks.
The Mirai botnet attack served as a wake-up call for both device manufacturers and users, emphasizing the importance of implementing strong security measures in IoT devices and practising good security hygiene. It also underscored the significance of robust DDoS protection measures for critical internet infrastructure and the need for constant vigilance in mitigating such attacks.
- Change the DNS server to Cloudflare’s DNS server or Quad-9 DNS server. (Solution to DNS poisoning)
- Think about this attack and in the forum discuss the following:
- What steps could have been taken to prevent this incident?
- Was the incident adequately handled?
- What are other incidents of this type of attack?
A buffer overflow occurs when a program or process attempts to write more data to a buffer (fixed-length block of memory) than it can hold. Buffers contain a defined amount of data and any extra data will overwrite data values in memory addresses adjacent to the destination buffer.
Attackers can exploit a buffer overflow to control, modify, or crash a process and violating a programming language and overriding the bounds of the buffer to trigger additional actions allows them to send new instructions to an app, therefore giving the hackers access to IT systems, or corrupting an app and taking over a machine.
Types of buffer overflow attacks:
- Stack-based Buffer Overflow: This type of attack targets the stack, a region of memory used for storing local variables and function call information. By overflowing a buffer on the stack, an attacker can overwrite the return address of a function, allowing them to redirect the execution flow to a malicious code payload.
- Heap-based Buffer Overflow: In contrast to stack-based attacks, heap-based buffer overflows target dynamically allocated memory on the heap. Attackers manipulate the size of dynamically allocated buffers, causing adjacent data structures to become corrupted. This can lead to various consequences, including arbitrary code execution or cause the program to crash.
- Integer Overflow: While not strictly a buffer overflow, an integer overflow can lead to similar consequences. It occurs when an arithmetic operation results in a value larger than the maximum representable value for the data type. Attackers can exploit integer overflows to manipulate memory or control program behaviour.
- Format String Attacks: Format string vulnerabilities occur when a program uses user-supplied format strings without proper validation. By exploiting this vulnerability, an attacker can manipulate the format string to read or write data from arbitrary memory locations, potentially leading to a buffer overflow and execution of malicious code.
- Unicode Overvflow: Unicode is a character encoding standard that assigns a unique numerical value (code point) to each character in various writing systems. It provides a way to represent and handle text in different languages and scripts. Vulnerabilities related to Unicode or character encoding exist within specific software applications or implementations.
Protect Against Buffer Overflow Attacks
- Use OS runtime protections, which make it harder for attacks to succeed
- Keep devices patched, to fix buffer overflow vulnerabilities
- Follow the principle of least privilege, only giving users and apps the permissions they need
- Use memory-safe programming languages like Jave, Python or C#
Injection attacks are a common type of security vulnerability that can compromise the integrity and security of software applications. Injection attacks occur when an attacker injects malicious code or commands into an application's input fields or data streams. Attackers exploit vulnerabilities in an application's handling of user input to execute unauthorized actions, gain unauthorized access, or manipulate the application's behaviour.
Watch the following video on Injection Attacks created by an ethical hacker for IBM that outlines the different types of Injection Attacks and their potential impacts.
SQL Injection Attacks:
SQL Injection Attacks are a type of injection attack that makes it possible to execute malicious SQL statements, which are then able to control a database server behind a web application.
A successful SQL injection exploit can:
- read sensitive data from the database
- modify database data (Insert/Update/Delete)
- execute administration operations on the database (such as the shutdown of the DBMS)
- Recover the content of a given file present on the DBMS file system and
- In some cases, issue commands to the operating system.
Examples of SQL Injections:
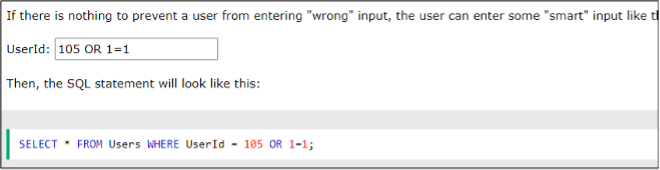
SQL Injection Based on 1=1 is Always True
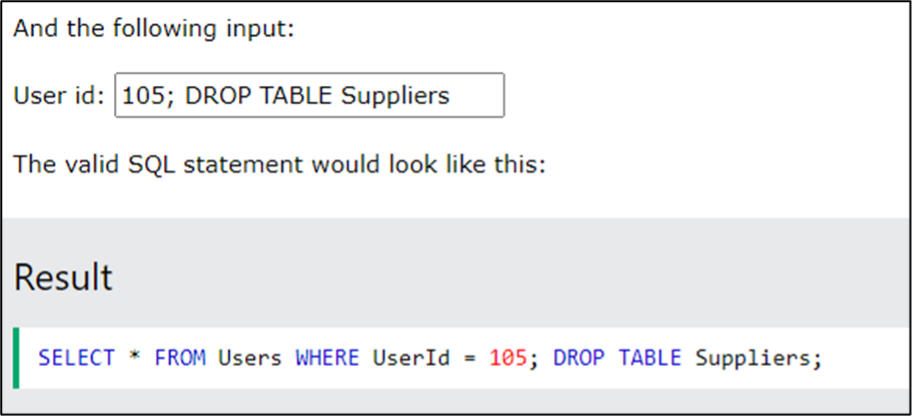
SQL Injection Based on Batched SQL Statements
protect against SQL Injections
- User-input sanitization
- Use safe programming functions that make SQL Injections impossible: parameterized queries (prepared statements) and stored procedures. Every major programming language currently has such safe functions and every developer should only use such safe functions to work with the database.
- Web application firewalls (WAFs) are the most common tool used to filter out SQL attacks. WAFs are based on a library of updated attack signatures and can be configured to flag malicious SQL queries in web applications.
Cross-site Scripting Attacks:
Cross-site scripting (XSS) attacks occur when hackers execute malicious JavaScript within a victim’s browser. Sensitive details about the authenticated user can be stolen from the session, and completely compromise a website.
Attackers can inject their code to target the visitors of the website by adding their own ads, phishing prompts, or other malicious content.
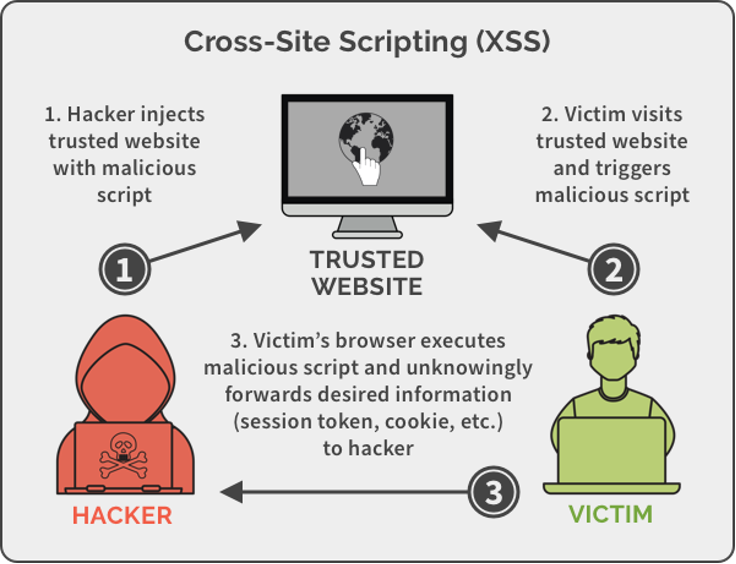
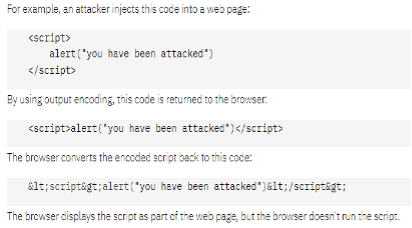
Examples of XSS attacks
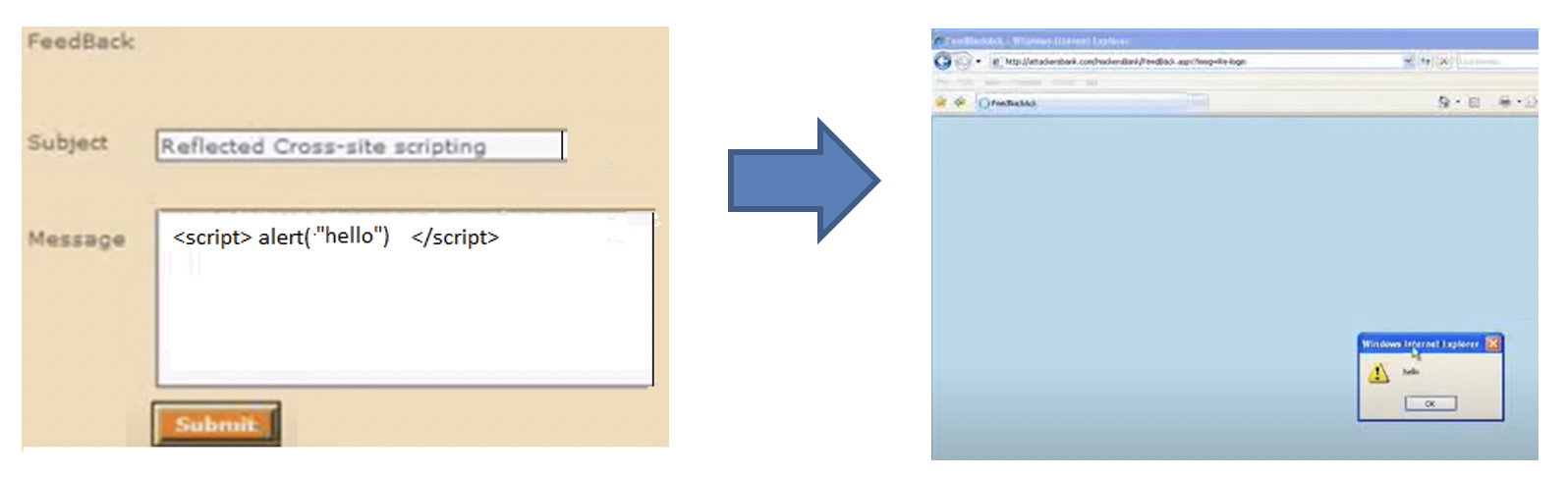
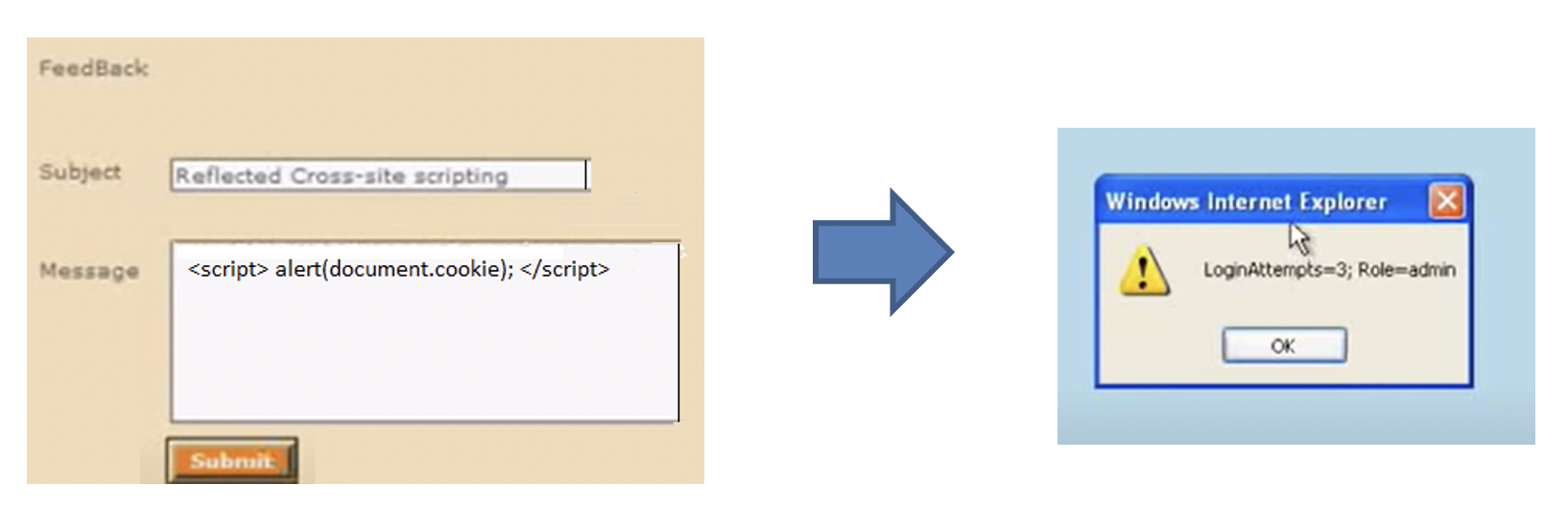
This will list all the cookie variables in the browser at this time. Document.cookie variable clearly contains some sensitive information.
Protect against XSS Attacks
- Filter input on arrival. At the point where user input is received, filter as strictly as possible based on what is expected or valid input.
- Encode data on output: to prevent the code from being interpreted as active content:
- HTML markup will be substituted with entities.
- The browser displays the entities but doesn't run them
- Use Web Firewall Applications to employ different methods to counter-attack vectors. In the case of XSS, most will rely on signature-based filtering to identify and block malicious requests.
Preventing Injection Attacks
- Input Validation and Sanitization: Implement strict input validation by validating and sanitizing all user input to ensure it conforms to expected formats and data types. Use parameterized queries or prepared statements to prevent SQL injection attacks by separating data from SQL commands.
- Least Privilege Principle: Assign minimal privileges to application components, databases, and user accounts, limiting the potential impact of an injection attack.
- Input Filtering and Encoding: Filter and sanitize input data by removing or encoding special characters to prevent interpretation as code or commands. Apply appropriate encoding mechanisms (e.g., HTML encoding) to prevent cross-site scripting (XSS) attacks.
- Security Testing and Code Reviews: Regularly conduct security testing, including vulnerability scanning and penetration testing, to identify and address injection vulnerabilities. Perform code reviews to identify insecure coding practices and ensure secure coding standards are followed.
- Use Security Frameworks and Libraries: Utilize security frameworks and libraries that provide built-in protection against common injection vulnerabilities.
- Security Awareness Training: Educate developers and users about the risks and best practices for preventing injection attacks. Encourage a security-conscious culture that emphasizes the importance of secure coding practices and vigilant user behaviour.
- Filter input on arrival. At the point where user input is received, filter as strictly as possible based on what is expected or valid input.
- Encode data on output: to prevent the code from being interpreted as active content:
- HTML markup will be substituted with entities.
- The browser displays the entities but doesn't run them
- Web Firewall Applications: Use Web Firewall Applications to employ different methods to counter-attack vectors. In the case of XSS, most will rely on signature-based filtering to identify and block malicious requests.
Preventing Injection Attacks:
CASE STUDY: Injection attack

One real-life example of an injection attack is the SQL Slammer worm, also known as W32.SQLExp.Worm, which occurred in January 2003.
When: The SQL Slammer attack took place on January 25, 2003.
Who: The attack affected numerous computer systems and networks running Microsoft SQL Server or Microsoft SQL Server Desktop Engine (MSDE). The impact was widespread, impacting both individuals and organizations.
What happened: The SQL Slammer worm exploited a vulnerability in Microsoft SQL Server's Resolution Service (UDP port 1434). It propagated by sending a small malicious packet to vulnerable systems, causing them to become infected and act as new hosts for further propagation.
The worm utilized a technique called SQL injection, where it injected a specially crafted SQL query into vulnerable servers. The injected code caused the server to send multiple requests to random IP addresses, overwhelming networks with a flood of traffic. This led to significant network congestion and the degradation or complete loss of Internet connectivity for affected systems.
Impact: The SQL Slammer worm had a significant impact on global internet infrastructure. Due to its rapid spread and ability to exploit vulnerable systems within minutes, it caused widespread disruption. The worm's network congestion resulted in slowed or completely halted internet access for many individuals, businesses, and even critical infrastructure providers.
The attack highlighted the importance of promptly patching and securing systems to prevent the exploitation of known vulnerabilities. It also underscored the potential impact of injection attacks and the need for robust security measures to protect against them.
Following the SQL Slammer incident, Microsoft released patches to address the vulnerability, and network administrators worldwide scrambled to implement the necessary updates to protect their systems. The attack served as a reminder of the critical role that proactive security measures and timely patch management play in mitigating the risks posed by injection attacks.
Read the following article to learn more about Injection attacks and their different types
https://www.acunetix.com/blog/articles/injection-attacks/
- Find what’s meant by: Next Generation antivirus
- Think about this attack and in the forum discuss the following:
- What steps could have been taken to prevent this incident?
- Was the incident adequately handled?
- What are other incidents of this type of attack?
CSRF (Cross-Site Request Forgery) is a type of security vulnerability that allows an attacker to perform unauthorized actions on behalf of an authenticated user. It occurs when an attacker tricks a victim into unknowingly executing malicious actions on a trusted website or application where the victim is authenticated. Very commonly exploited a vulnerability that allows an attacker to force a user to unknowingly perform actions, therefore, allowing changes to be performed by the name of the users without their knowledge or approval.
As a result, CSRF commonly targets cloud storage, social media, banking and online shopping web page applications in order to harvest social media images and create embarking social media posts, right through to taking money from online accounts. Because of this, CSRF is ranked #8 on OWASP's top 10 charts.
Watch the following video on CSRF.
Example CSRF Attack:
In the previous video, we saw an example of a CSRF Attack. In this example we saw a user visit a page that contains a CSRF attack while also logged into their bank account. Upon visiting the page, a request is performed to transfer money from one account to another.
User TAB 1: Bank Account
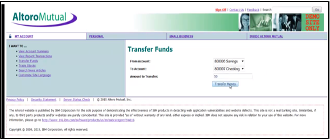
User TAB 2: Page that contains CSRF
The result is $6,000 withdrawn from the user’s account.
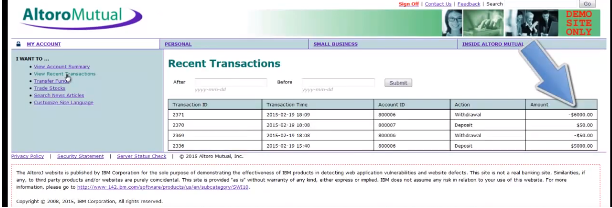
So how did this attack occur?
The banking application allows for a request to originate from servers other than itself because there is no unique token that is tied to the user session.
The general rule therefore should be that if this token is absent or incorrect, it will stop the transaction from being performed.
How to detect and prevent CSRF attacks:
Detect by using:
- by using an automated web vulnerability scanner.
- For example Acunetix, App Scan
Prevent by using:
- ANTI-CSRF tokens
- Web Application Firewall (this help prevent CSRF attacks)
Both brute force and dictionary attacks are methods employed by attackers to gain unauthorized access to systems or encrypted data. They both rely on systematically trying various combinations or pre-compiled lists of passwords or encryption keys to find the correct one.
Brute Force Attacks
A brute force attack is a hacking method that uses trial and error to crack passwords, login credentials, and encryption keys. These types of attacks can take a significant amount of time to complete.
A five-digit lock with individual values from zero to nine has exactly 100,000 possible permutations.
Birthday Attacks
A Birthday Attack is a type of cryptographic attack that belongs to a class of brute force attacks. It exploits the mathematics behind the birthday problem in probability theory.
What is the Birthday Paradox?
The probability of at least two people sharing the same birthday in a group of 23 people is 50%.
The birthday paradox, also known as the birthday problem, is a counterintuitive phenomenon in probability theory. It states that in a group of relatively few people, the probability of two people sharing the same birthday is surprisingly high.
Contrary to what one might expect, the birthday paradox arises from the combinatorial nature of the problem rather than the total number of possible birthdays (365 in a non-leap year).
For example, with just 23 people in a group, the probability of at least two people sharing a birthday exceeds 50%. With 50 people, the probability increases to approximately 97%.
The birthday paradox is often used to illustrate the concepts of probability, combinatorics, and the non-intuitive nature of probability theory. It demonstrates how seemingly improbable events can occur more frequently than expected when dealing with large numbers and random combinations.
How do Birthday Attacks Work?
Birthday attacks exploit or take advantage of collision to a hash function (2 different messages hash out to the same value). It forces this collision in order to change the original message. The success of this attack largely depends upon the higher likelihood of collisions found between random attack attempts and a fixed degree of permutations, as described in the birthday paradox problem.
Example of a Birthday Attack
Bob and Sue are going to get married, as a precaution they both agree to write up a document that in case of a divorce outlines ownership of their respective property. This document states that whatever assets/property Bob owned prior to the marriage he retains in the event of a divorce, and inversely whatever assets/property Sue owned prior to the marriage she retains. Once completed, they take this document and put it into a hashing algorithm to create a message digest value.
In secret, Sue then makes a copy of the original document, and she changes the wording to state in the event of divorce any assets or property that belonged to her prior to marriage, she will retain in the event of a divorce and she will also receive all assets/property previously owned by Bob. Sue creates a hash of the altered document to make a message digest. Initially, the message digest is different. But using the Birthday Attack theory, Sue consistently tweaks the document, slightly changing words and punctuation until she can actually create a message digest value that matches the original.
Unsurprisingly, Bob and Sue get divorced. During the divorce proceedings Sue tells Bob she is to receive everything in the settlement, Bob unknowingly refers to the hashed document and states that they had a formal agreement and refers the lawyers and Sue to the encrypted document. to give her everything he has. Upon reviewing each others version of the document using the hashing algorithm and they both have the same message digest, however, once decrypted, Sue’s document clearly states that she is entitled to everything.
How to Prevent Birthday Attacks
To avoid this attack, a very strong combination and a long sequence of bit length can be chosen so that the birthday attack becomes computationally infeasible, i.e. about twice as many bits as are needed to prevent an ordinary brute-force attack
Dictionary Attacks
A Dictionary Attack is the method of breaking into a password-protected computer, network or other IT resources by systematically entering every word in a dictionary as a password. Attackers incorporate words related to sports teams, monuments, cities, addresses and other regionally specific items when building their attack library dictionaries:
An example of this is the massive SolarWinds data breach which was executed using a dictionary attack. SolarWinds is an IT management company that monitors, analyzes, diagnose and optimizes database performance and data ops. SolarWinds serviced a large number of clients, most notably the US Department of Justice. From 2019 to 2020, Russian-backed hackers were able to log in to SolarWinds' update server by correctly guessing the administrator password, "solarwinds123," and then planting a backdoor that was activated when SolarWinds customers updated their software. This became one of the biggest breaches of the last decade.
Protect Against Brute Force and Dictionary Attacks
- Increase password length
- Increase password complexity
- Limit login attempts
- Implement Captcha
- Use multi-factor authentication
CASE STUDY: Brute Force and Dictionary Attack

One real-life example of a Brute Force and Dictionary Attack is the LinkedIn data breach that occurred in 2012.
When: The attack took place in June 2012.
Who: The attack targeted LinkedIn, a popular professional networking platform with millions of users worldwide. The breach impacted the accounts of LinkedIn users.
What happened: In this attack, hackers used a combination of Brute Force and Dictionary Attack techniques to gain unauthorized access to user accounts on LinkedIn's platform. They obtained a database containing millions of hashed passwords, which were protected using the SHA-1 algorithm. The attackers then employed automated tools to systematically guess and crack the passwords. Brute Force involves attempting all possible combinations of characters until the correct password is discovered, while Dictionary Attack utilizes pre-existing lists of commonly used passwords or previously leaked password databases.
As a result of the successful attack, the hackers were able to access a significant number of LinkedIn user accounts.
Impact: The LinkedIn data breach had several implications. Firstly, the breach exposed sensitive information, including passwords, email addresses, and other personal details, of millions of users. This put those individuals at risk of various cybercrimes, such as identity theft and phishing attacks.
Moreover, the incident highlighted the importance of using strong, unique passwords and implementing additional security measures like two-factor authentication. It served as a reminder for both individuals and organizations to follow best practices in password security and to regularly update and strengthen their authentication mechanisms.
Following the breach, LinkedIn took immediate action by invalidating the compromised passwords and implementing enhanced security measures. However, the incident served as a wake-up call for the industry as a whole, emphasizing the need for robust security measures and the constant evolution of defences against Brute Force and Dictionary Attacks.
- What steps could have been taken to prevent this incident?
- Was the incident adequately handled?
- What are other incidents of this type of attack?

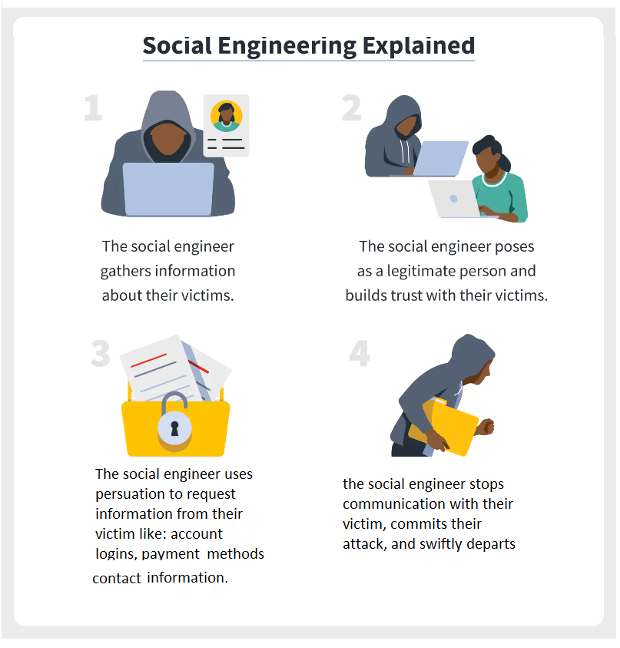
Unlike other forms of attack that target security vulnerabilities, Social Engineering targets Human vulnerability. Social engineering (aka Human Hacking) is the art of manipulating and exploiting human psychology to deceive individuals into revealing sensitive or confidential information, performing certain actions, or granting unauthorized access. It is a technique commonly used by attackers to bypass technical security measures by exploiting the trust and vulnerability of individuals which usually occurs through digital communication.
The goal of social engineering is to exploit human behaviour and emotions, such as curiosity, fear, trust, or urgency, to manipulate individuals into revealing valuable information or performing actions that benefit the attacker.
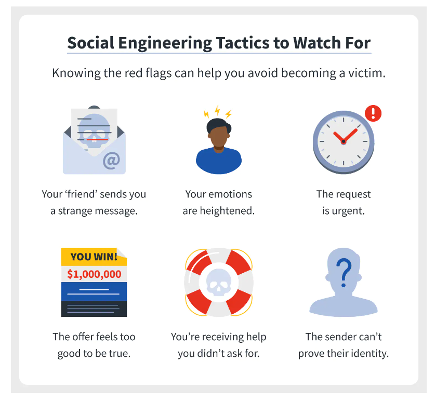
Signs of Social Engineering Attempts
- Sense of Urgency: Social engineering attacks often create a sense of urgency to pressure individuals into acting quickly without careful consideration. These are generally urgent requests for immediate action, such as resetting passwords or providing sensitive information.
- Unsolicited Communication: Social engineers might reach out under the guise of a company providing help for a problem you have, similar to a tech support scam. You might believe they’re who they say they are and provide them access to your device or accounts. These are generally unsolicited emails, phone calls, or messages, especially if they request sensitive information, ask for money, or offer unexpected rewards. Legitimate organizations usually do not reach out unexpectedly to ask for such information.
- Emotional Manipulation: Social engineering attackers often try to evoke strong emotions, such as fear, curiosity, or excitement, to cloud judgment and prompt immediate action. Be mindful of these emotional triggers and take a step back to evaluate the situation objectively.
- Prizes, Gifts and Opportunities for Money: Social Engineers like to play on greed and desperation and offer lure in victims by starting with offering the intended victim good news like winning a cruise, a lottery that didn’t enter or an opportunity to make large sums of money.
- Strange Requests from ‘Friends’: Having taken over the identity of someone, Social Engineers will often use this to gather further information or money from their contacts.
Examples of Social Engineering
- Physical Breaches - physically posing as a legitimate source to steal confidential data or information from you.
- Baiting - a social engineer might leave a USB stick, loaded with malware, in a public place where targets will see it such as in a cafe or bathroom.
- Phishing - Tricking a user into providing info or downloading malware usually by using an email that appears from a trusted or reputable source.
- Scareware - pop-ups or emails indicating you need to “act now” to get rid of viruses or malware on your device. In fact, if you act you might be downloading a computer virus or malware.
Protect Against Social Engineering Attacks
Phishing attacks are fraudulent attempts to deceive individuals into revealing sensitive information, such as passwords, credit card details, or personal data, by impersonating a trusted entity. Attackers often use various tactics to trick victims into clicking on malicious links, downloading malware-infected files, or providing their confidential information.
Phishing Attacks have three categories.
General Phishing Attack
General phishing attacks are broad-based and typically target a large number of individuals indiscriminately. Attackers send out mass emails or messages that appear to be from well-known companies, financial institutions, or service providers, aiming to trick recipients into revealing their personal information or performing certain actions. These attacks are often generic and not personalized to specific targets.
Spear Phishing
Spear phishing attacks are more targeted and personalized compared to general phishing attacks. Attackers conduct thorough research on their intended victims to gather information such as their names, job titles, affiliations, or recent activities. They then craft tailored and convincing messages that appear to be from a trusted source known to the target, such as a colleague, supervisor, or business partner. The goal is to increase the likelihood of the victim falling for the scam by leveraging familiarity and trust.
Whaling Attacks
Whaling attacks, also known as CEO fraud or executive phishing, are a specialized form of spear phishing that specifically targets high-level executives or individuals in senior positions within an organization. Attackers carefully select their targets and conduct extensive research to gather detailed information about the individual's role, responsibilities, and communication patterns. The aim is to deceive the executive into taking actions that could lead to significant financial loss or compromise the organization's sensitive data.
While general phishing attacks cast a wide net, spear phishing and whaling attacks are more sophisticated and personalized. They rely on social engineering techniques to manipulate individuals into believing that the communication is legitimate and trustworthy. By tailoring the attack to specific targets, attackers increase their chances of success.
Example of an Email Phishing Attack
An email is sent to a target with a password expiry notice.

This Phishing Attack has a call to action which asks the victim to click a URL to a spoofed website or malicious link that contains malware.
While this URL may look legitimate at first glance there is a subtle difference between the actual URL and the spoofed website.
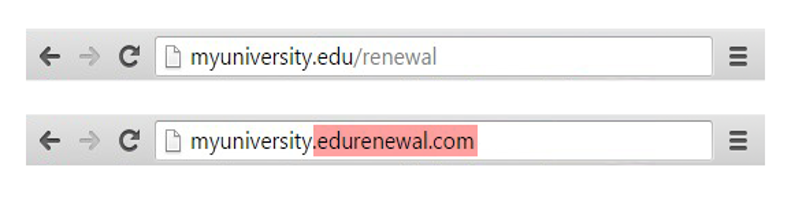
The spoofed website will either gather personal details from the victim or insert malware.
Protect Against Phishing Attacks
- Employ common sense before handing over sensitive information: When you get an alert from your bank or other major institution, never click the link in the email. Instead, open your browser window and type the address directly into the URL field so you can make sure the site is real.
- Never trust alarming messages. Most reputable companies will not request personally identifiable information or account details, via email. This includes your bank, insurance company, and any company you do business with.
- If you ever receive an email asking for any type of account information, immediately delete it and then call the company to confirm that your account is OK.
- Be careful when opening attachments in these suspicious or strange emails — especially Word, Excel, PowerPoint or PDF attachments.
- Keep your software and operating system up to date. Windows OS products are often targets of phishing and other malicious attacks, so be sure you're secure and up to date. Especially for those still running anything older than Windows 10.
- By combining a firewall, anti-spam and anti-malware into one package, you can provide extra backups that keep your system from being compromised, if you do accidentally click on a dangerous link. They are a vital tool to have installed on all your computers as they are designed to complement common sense.
- Education and training sessions for the employees to recognize phishing emails.
- Look for an example of a spear-phishing attack
Malware, short for malicious software, refers to any software or code designed to harm, exploit, or gain unauthorized access to computer systems, networks, or devices. Malware is created with malicious intent and can cause a wide range of detrimental effects, including data theft, system damage, financial loss, and privacy breaches. Generally, Malware is designed to transmit information about your web browsing habits to a third party.
There are various types of malware, each with its own characteristics and purposes.
- Viruses: Viruses are self-replicating programs that infect other files or programs by attaching themselves to them. They can spread rapidly and can cause damage to files, software, and even the entire system.
- Worms: Worms are standalone programs that can replicate and spread across networks without needing to attach themselves to other files. They can consume network resources, slow down systems, and exploit vulnerabilities to gain unauthorized access.
- Trojans: Trojans are deceptive programs that masquerade as legitimate software or files. Once installed, they can perform various malicious activities, such as stealing sensitive information, opening backdoors for attackers, or initiating unauthorized actions on the compromised system.
- Ransomware: Ransomware encrypts files or locks the entire system, rendering it inaccessible to the user until a ransom is paid. It is a lucrative form of malware that extorts money from victims by exploiting their need for access to their data or systems.
- Spyware: Spyware is designed to gather information about a user's activities without their consent. It can monitor keystrokes, capture screenshots, track browsing habits, and steal sensitive data, including login credentials and financial information.
- Adware: Adware is software that displays unwanted advertisements on a user's computer or device. While not necessarily malicious, it can disrupt user experience, slow down systems, and collect user data for targeted advertising purposes.
- Rootkit: Rootkits operate at a deep level within an operating system, typically at the kernel or device driver level, which gives them high privileges and allows them to hide their presence and activities from regular system processes and users. Once a rootkit gains control, it can modify system files, manipulate system behaviour, and even tamper with security mechanisms.
Virus
A Virus is a software that replicates itself and spreads by damaging and deleting files. A computer virus attaches itself to a program or file, enabling it to spread from one computer to another, leaving infections as it travels. Generally, a Virus will enter a device by being attached to images, audio, video or download files.
A Virus can range in its severity. Some have mild effects while others can cause huge damage to hardware, software or files.
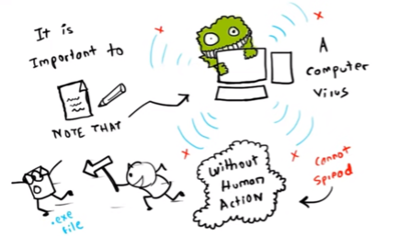
Almost all viruses are attached to executable files, although viruses may exist on your computer but don’t infect your computer unless you run a malicious program. A virus cannot spread without human action (running an infected program).
Worms
Worms can be considered a subclass of a Virus. Like a Virus, Worms are malicious programs that make copies of themselves on local devices and through network shares. Worms make the device work slower and spread from device to device. Unlike a Virus, however, a Worm has the capability to travel from one computer to another, without any human action.
Spread of Worms
Once you have been infected with a worm, without knowing it the worm sends a copy of itself to everyone listed in your email address book.
Then the worm replicates to send itself to everyone listed in each of the receiver’s address books, and the manifest continues.
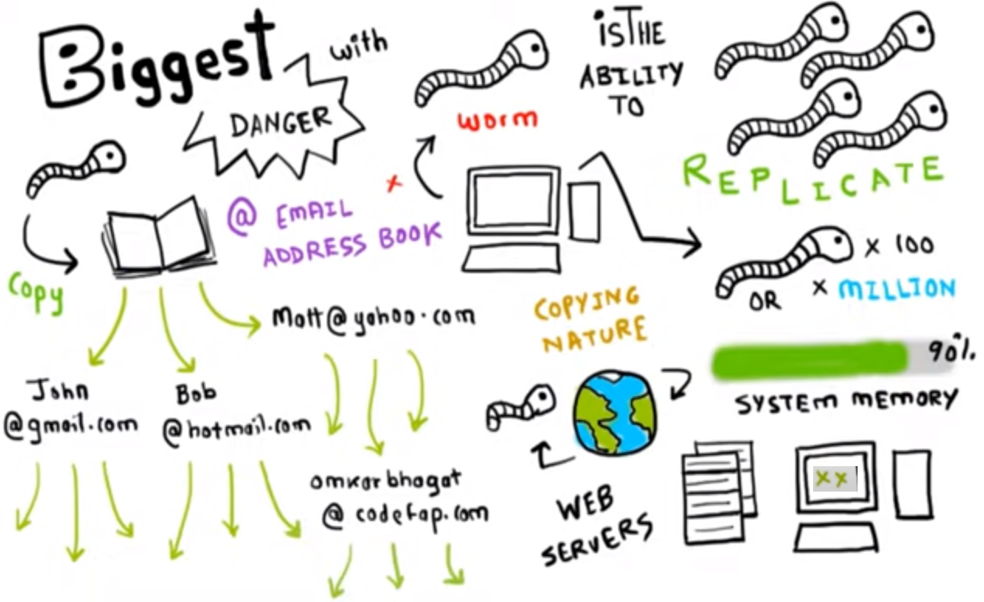
Due to the capability of replicating itself and the ability to travel across the network, it consumes too much system memory (network bandwidth), causing web servers, network servers, and individual computers to stop responding.
Trojan Horse
A Trojan horse, often referred to simply as a "Trojan," is a type of malicious software that disguises itself as a legitimate program or file to deceive users and gain unauthorized access to their computer systems. The name "Trojan horse" is derived from Greek mythology, where the Greeks used a large wooden horse to infiltrate and attack the city of Troy.
Similar to its namesake, a Trojan horse appears harmless or useful on the surface, tricking users into executing or installing it. Once inside the system, the Trojan horse performs malicious actions without the user's knowledge or consent. Unlike viruses or worms, Trojans do not replicate themselves but instead rely on social engineering tactics to spread and carry out their malicious activities.
Trojan horses can take various forms, such as executable files, documents, email attachments or even fake software updates. Like Viruses, Trojans can range in severity, from simply being annoying like changing desktops or adding silly active desktop icons to causing series damage by deleting files and destroying information.
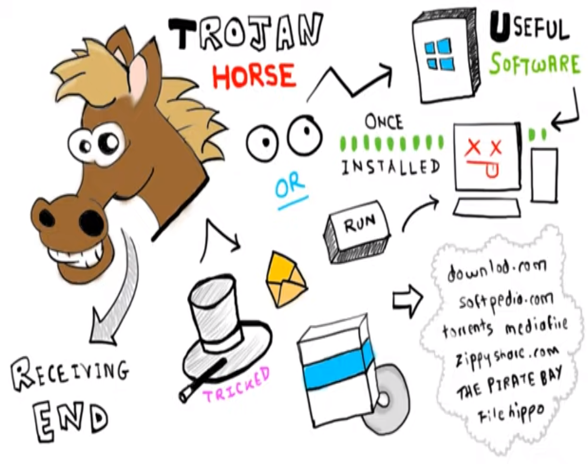
Trojans are known to create a backdoor on your computer that gives malicious users access to your system allowing confidential data to be compromised. Unlike Viruses, Trojans don’t reproduce by reinfecting files and don’t self-replicate.
Spyware
Spyware refers to malicious software that is designed to secretly collect information about a user's activities without their knowledge or consent. It is typically installed on a computer or device without the user's awareness and operates covertly in the background.
Spyware can gather a wide range of sensitive information, including browsing habits, keystrokes, login credentials, personal documents, emails, and more. The collected data is then transmitted to remote servers or used for various malicious purposes, such as identity theft, unauthorized access to financial accounts, targeted advertising, or selling the information to third parties.
Spyware often infiltrates systems through deceptive methods, such as bundling with legitimate software downloads, clicking on malicious links or ads, or exploiting security vulnerabilities. It can also be distributed through email attachments, infected websites, or infected removable storage devices.
Step by step, spyware will take the following actions on your computer or device:
- Infiltrate – via an app install package, malicious website or file attachment
- Monitor and capture data – via keystrokes, screen captures, and other tracking codes
- Send stolen data – to the spyware author to be used directly or sold to other parties
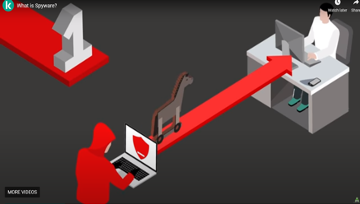
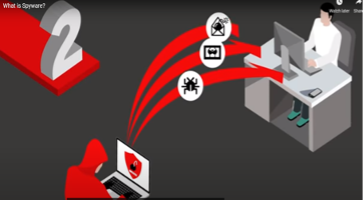
Hackers can get spyware to your device in many ways, but these 4 are the most common:
- It can penetrate your device in the form of a trojan (a type of malware that is disguised as legitimate software). Hackers use trojan in a sneaky process called social engineering.
- Hackers can exploit user interactions with advertisements, adult material content, and various 3rd party program download to gain access to devices.
- Hackers can compromise tracking cookies (a common practice that many legitimate websites employ).

- Spyware can get onto your device through system monitors that are designed to monitor computer activity and performance.
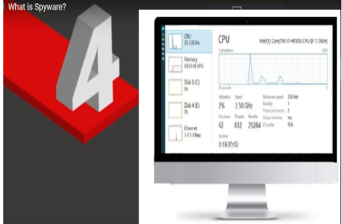
Infected with Spyware
Once spyware gets on your device, it can cause nasty problems:
- It can communicate your personal/confidential information (email activity, passwords, social media account, credit card info, and purchase history) to the attacker=> Your online identity is at high risk of being stolen and imitated.
- Spyware can potentially corrupt and compromise your device. It can soak up your device’s resources making it run slowly, tag between applications, crash and overheat
- It can manipulate search results and serve you potentially harmful and fraudulent websites, which may trick you to click on more harmful and dangerous viruses.
Adware
Adware is a type of malicious software that displays unwanted advertisements on a user's computer or device. It is often bundled with free software or downloaded unknowingly by users when they visit certain websites or click on malicious links. The primary purpose of adware is to generate revenue for its creators through advertising.
Adware typically works by injecting or displaying advertisements in various forms, such as pop-ups, banners, or in-text ads, while the user is browsing the internet. These ads can be intrusive, and disruptive, and may lead to a poor user experience. Adware may also redirect the user's web searches to sponsored websites or modify browser settings to display targeted advertisements.
Impacts of Adware
- Adware redirects your search requests to advertisement websites and collects data about you. This info is used to deliver custom advertisements to you.
- Adware is usually bundled with other files, and programs that you have downloaded and is not necessarily harmful however it has the potential to be.
- Pop-ups, toolbars installed in your browser, and changes made to your default search engines are common occurrences of adware.
- They can massively slow down your computer’s performance system.
- They can be malicious by hijacking your browser and redirecting you to potentially unsafe sites.
- Some adware contains trojan viruses and spyware specifically designed for stealthy installation.
Unfortunately, adware doesn’t always have to uninstall option meaning these types of programs can be difficult to remove. Some antivirus programs may not be able to determine if a specific adware is a threat or not.
Protection against adware
- Get your files and programs from a reputable website.
- When you install a program, carefully read through the terms and service agreement for any hidden adware that you might not be aware of.
- Pop-up, ad blocker blockers can limit your exposure to adware.
Ransomware
Ransomware is a type of malware that blocks users from accessing their operating system or files until a ransom is paid. It does so by locking the system’s screen or encrypting the users’ files using advanced encryption algorithms.
There is generally a time restriction for completing the payment usually in Bitcoin, or else the files may be lost permanently or made public by attackers. Unfortunately, even if the victim pays the ransom, there is no assurance that the decryption key will be delivered.
Protect Against Ransomware Attacks
- Keep your antivirus software up to date, and use multiple AVs to scan email & web content
- Use software restriction policies or AppLocker
- Train your employee to recognize malicious emails, report them
- Be aware of pop-up installation requirements
- Think twice before you open links and attachments in your email
- Don’t download apps from unknown sources
- Use VPN on public Wi-Fi
- Harden systems, reduce rights, disable macros (unless on the whitelist)
- Apply the principle of least privilege (reduce rights)
- Update your operating system and your apps
- Back up and encrypt essential data
- Use a multi-layer cybersecurity approach
What to do in cases of Ransomware Attacks
DO NOT PAY THE RANSOM
- All businesses should have an incident response plan in place, and know it by heart meaning that it will reduce the time of response which is critical in these cases.
- Isolate affected end-points (disconnect them) from the network to stop the spread.
- Track down the attack: which computer was infected? Did the user click any suspicious emails? Or was there any unusual behaviour on their computer?
- Identify the ransomware strain that affected your network.
- Report the attack to authorities as soon as possible
- If the computer is infected by ransomware, run it on safe mode and install an anti-malware solution in order to remove the ransomware, and use a decryption tool.
- Patch your security system after the issue has been resolved
- Perform a total security audit
- Recover your data, restore data from backup
- Go to www. nomoreransom.org, and look over the list of ransom names. You might be able to decrypt it.
Rootkit
A rootkit is a type of malware designed to give hackers access to and control over a target device. Although most rootkits affect the software and the operating system, some can also infect your computer’s hardware and firmware.
Rootkits are proficient at concealing their presence, but while they remain hidden, they are active. Rootkits can hide keyloggers, which capture your keystrokes without your consent.
Once they gain unauthorized access to computers, rootkits enable cybercriminals to:
- steal personal data and financial information
- install malware
- send out spam email
- participate in DDoS (distributed denial of service) attacks
- They can even disable or remove security software.
The name “rootkit” derives from Unix and Linux operating systems, where the most privileged account admin is called the "root". Once a bad actor has root-level (administrator-level, privileged) access, nothing on your computer is secure. Everything is fair game.
How to find Rootkits
It is almost impossible to find a rootkit installed on your PC, even if you know there is one on your computer. You need help from a next-gen antivirus solution.
Although Rootkit detection is a challenge, as a responsible computer user, you can keep an eye out for strange behaviour on your computer:
If you think it’s slow to load or certain processes are not working smoothly, you’d be right to suspect malware
Protect Against Rootkit Malware
- Be proactive about securing your PC and install a comprehensive and advanced antivirus / Internet security solution
- Download software from reputed sites only – and review all user ratings/reviews
- Download software patches and antivirus updates as and when available
- Don’t cast a blind eye to your computer’s behavioural issues; learn why these are happening
CASE STUDY: Malware Attack

One real-life example of a malware attack is the WannaCry ransomware attack that occurred in May 2017.
When: The attack took place on May 12, 2017.
Who: The WannaCry attack targeted organizations and individuals worldwide, impacting hundreds of thousands of computers across various industries, including healthcare, government, and telecommunications.
What happened: The WannaCry ransomware attack exploited a vulnerability in Microsoft Windows operating systems, particularly targeting machines that hadn't been patched with the necessary security updates. The attack spread rapidly using a worm-like behaviour, infecting vulnerable systems connected to the same network.
Once a system was infected, WannaCry encrypted the files on the computer, making them inaccessible to the user. The attackers then demanded a ransom payment in Bitcoin to provide the decryption key and restore access to the encrypted files.
The malware also incorporated worm-like capabilities, allowing it to self-propagate and infect other vulnerable systems connected to the network. This led to the rapid spread of the attack across organizations and countries.
Impact: The WannaCry attack had a significant impact globally. It disrupted the operations of numerous organizations, including hospitals, government agencies, and businesses, rendering their systems and data inaccessible. This resulted in halted operations, delayed healthcare services, and financial losses.
The attack raised awareness about the importance of timely patching and updating software systems to protect against known vulnerabilities. It also highlighted the severe consequences of malware attacks and the need for robust cybersecurity measures, including effective backups, network segmentation, and proactive monitoring, to mitigate such threats.
Following the WannaCry attack, security researchers and organizations collaborated to analyze the malware and develop tools to decrypt files without paying the ransom. Additionally, Microsoft released emergency security updates to address the vulnerability that WannaCry exploited.
The incident served as a reminder of the ever-present threat of malware and the need for individuals and organizations to remain vigilant, keep their systems updated, and employ comprehensive security practices to protect against such attacks.
- What steps could have been taken to prevent this incident?
- Was the incident adequately handled?
- What are other incidents of this type of attack?
Bluejacking is a term used to describe the unauthorized sending of unsolicited messages or data to Bluetooth-enabled devices, such as mobile phones, tablets, or laptops. It is a form of wireless spamming or nuisance messaging that takes advantage of Bluetooth technology's short-range communication capabilities.
Bluejacking exploits a Bluetooth device's ability to receive and accept incoming data or messages from other nearby Bluetooth-enabled devices. The attacker typically sends a text message, contact card, or other types of data to the victim's device without their consent or knowledge. The messages are often harmless and aim to surprise or annoy the recipient rather than causing any real harm. It's important to note that bluejacking is generally considered a harmless prank rather than a malicious attack. The attacker does not gain control over the victim's device or access to their personal information. The main purpose is to disrupt or annoy the recipient by sending unsolicited messages.
Protect Against Bluejacking
- Disable Bluetooth visibility or set it to "hidden" or "non-discoverable" mode on their devices. This reduces the chances of receiving unsolicited messages from nearby devices.
- Avoid accepting or opening messages or files from unknown or untrusted sources.
- Regularly review and manage the devices connected to Bluetooth and remove any unauthorized or unfamiliar devices.
- Keep the Bluetooth firmware and software up to date with the latest security patches and updates.
- Be cautious when in public places or crowded areas where bluejacking attacks are more likely to occur.
An advanced persistent threat is a set of stealthy and continuous computer hacking processes, often targeting a specific entity. It is a sophisticated, sustained cyberattack in which an intruder establishes an undetected presence in a network in order to steal sensitive data over a prolonged period of time.
Characteristics of an APT
- Targets organizations and/or nations for business or political motives.
- Requires a high degree of covertness over a long period of time “low and slow” communications technique often coupled with the use of common communication protocols.
- Created by well-funded, highly sophisticated criminals or nation-states.
- Advanced, multi-vector attack techniques using malware are used to exploit vulnerabilities and expand the attack.
- External command and control system continuously monitors and extracts data; self-modification and or active patching is utilized to update malware and help evade detection.
AAPT Target Attack
- Reconnaissance: attacker quietly gathers information about the victim
- Weaponization: attacker prepares an attack payload to deliver to the victim
- Delivery: the attacker sends a payload to the victim
- Exploitation: attackers payload deployed in the victim’s network
- Installation: attacker establishes a foothold in the victim’s network
- Command and control: attackers have hands on the keyboard remote access to the victim’s network
- Actions on objectives: attacker acts to accomplish data exfiltration

