

Cyber-Physical Systems (CPS) are an integral part of developments that have led to the fourth industrial revolution. With rapid developments in digital technologies, fully autonomous systems are now possible. Cyber-Physical Systems are emerging as solutions to larger projects, including traffic control systems, smart energy systems and autonomous vehicles. Called ‘Smart’ systems, they closely integrate large collections of smart devices with communications, control and digital storage determined by sophisticated computer software.
Select the heading below to learn about Cyber-Physical Systems.
- Traffic control systems
- Smart energy systems
- Autonomous vehicles
What is a Cyber-Physical System?
Cyber-Physical Systems are a step beyond IoT smart device embedded systems currently used in automated manufacturing, industrial applications and domestic automated systems. Embedded systems consist of automated smart devices, such as a thermostat in an automatic heating system, and utilise information processing systems programmed to carry out automated tasks. Automated assembly robots in a factory setting or the electronic systems embedded in modern motor vehicles are also examples of embedded systems.
Despite having numerous applications, embedded systems still require human intervention to operate. Actions like turning the system on/off, adjusting the settings, providing input and monitoring output are all carried out by humans.
Further developments in digital technology have led to more autonomous Cyber-Physical Systems (CPS). A CPS consists of Cyber components and Physical components that work together to perform autonomous tasks.
Watch the video below to learn about Cyber-Physical Systems from Dr Sue Keay, CSIRO’s Data61 Cyber Physical Systems research director.
Read the full article 'Spotlight on Women in Tech' here:
https://algorithm.data61.csiro.au/spotlight-on-women-in-tech/
Cyber-Physical Systems (CPS) typically have numerous components, both Cyber and Physical, hence the name. The CPS components are tightly integrated to facilitate fully autonomous operations. The operation of the various components is orchestrated by sophisticated computer-based algorithms, allowing these systems to operate continuously with little or no human intervention.
Components of Cyber-Physical Systems are shown in the diagram below. Cyber components are shown in the top row in red. Physical components are shown in the bottom row in blue.
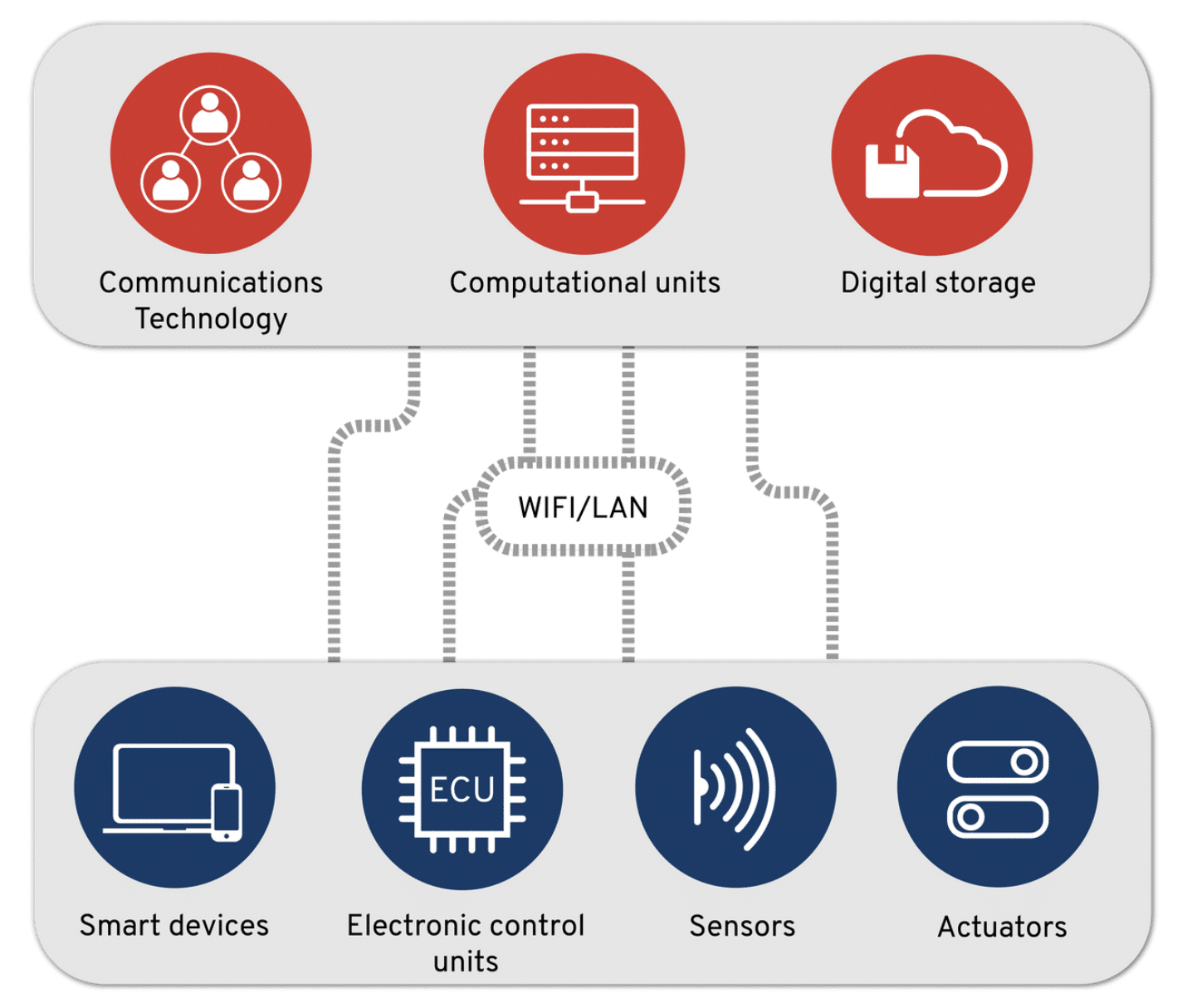
Cyber-Physical System Components in Action
Below is a schematic diagram showing the Cyber-Physical System components for the speed control system in an autonomous bus.
Select each stage starting with 1 to explore how the system works.
Insert activity here.
CPS architecture basically operates over three different layers, allowing numerous tightly integrated cyber and physical components to communicate almost seamlessly. The various components rely on differing technologies and communication protocols for communication to occur across the three layers. This layer system can be further refined into a multi-layer CPS architecture. However, the following is a summary of the three main layers in a CPS.
Learn about the different CPS layers.
Perception Layer
This layer is the sensing or recognition layer for sensors, actuators, aggregators, Global Positioning Systems (GPS), Radio-Frequency Identification (RFID) tags and other physical devices that collect data from the physical world.
Transmission Layer
This layer is the network or transport layer, where data is interchanged and processed between the Perception and Application layers. This interaction is achieved through connection to the internet using LAN and communication protocols, such as Wi-Fi and Bluetooth. Other technologies in this layer manage data routing and transmission using cloud computing platforms and various other technologies to protect the system from cyber-attacks.

Application Layer
This layer is the information processing layer. Information received from the Transmission layer is processed, complex decision-making algorithms make decisions based on the aggregated data, and commands to be executed by the physical components in the system are issued via the Transmission layer. This layer uses a strong multi-factor authentication process to prevent unauthorised access and preserve privacy.

Visit this link for a more detailed description of multi-layer CPS architecture:
Key Components of the Architecture of Cyber-Physical Manufacturing Systems, International Scientific Journal “Industry 4.0’, 2017 https://stumejournals.com/journals/i4/2017/5/205/pdf
Many CPS applications are sensor-based and communication-enabled autonomous systems. Wireless sensor network systems allow monitoring and data collection from a broad range of environments, either within a building, such as a hospital or factory, or outdoors to collect environmental data over a much wider area. CPS are used in many industries, as well as for organisational, domestic and research purposes. Other CPS categories include smart grids, distributed systems and process control.
Some common CPS applications:
- Automatic Pilot Avionics
- Autonomous Automobiles
- Biomedical Products
- Medical Monitoring
- Distributed Robotics
- Smart Manufacturing
- Smart Buildings
- Smart Homes
- Smart Energy Grids.
Autonomous CPS can be used in homes or in workplace and community buildings. Some examples include autonomous systems for security, heating and cooling, lighting, gardening and solar energy collection and monitoring.
Descriptions of the different Smart systems in the Smart Home shown below.
Smart lighting
Lights automatically switch on when sensors detect low light levels.
Smart gardening
Automatic watering system activated by a timer or soil moisture levels monitored by sensors.
Smart home energy
Solar system controller monitors daily solar energy kilowatt hours collected and used.
Smart security system
A video doorbell and perimeter surveillance system can provide a sense of security.
Smart heating/cooling
Thermostat control can automatically regulate indoor environmental conditions.
Smart appliances
Appliances controlled by smart electronics - touchscreen refrigerator, bread-making machine, smart multicooker, automatic coffee machine, robotic vacuum cleaner and voice- control microwave.
CPS can be used to manage various infrastructure systems in large cities with efficiency, economy and reliability. There are numerous applications for these autonomous systems for monitoring and controlling important aspects of infrastructure. Some examples include public transport, traffic flow, airport operations, railway signalling, electricity grids, air quality, public security, municipal services, water supply and waste management.
Learn about different Smart systems that can be used to manage infrastructure in a Smart City.
Airport operations
Manages baggage handling, ticketing security, maintenance and cleaning services.
Traffic light control
Regulates traffic flow to avoid congestion during peak periods.
Railway signalling
Regulates train routes, timetables and ensures trains operate safety.
Public transport
Regulates transit system such as road and rail, optimises routes, manages ticketing and maintenance
Small electricity grid
Detects and responds to changes in usage and unexpected issues to ensure supply
Water supply
Manages the infrastructure and processes required to reliably supple water to a cirt and waste water management.

Smart or Intelligent Transport Systems (ITS) can provide many benefits, particularly for people living in large cities. New and emerging technologies will make getting around cities safer and more convenient. According to a report from the Australian Government and ITS Australia:
There have been significant benefits from deployments of dynamic speed zones and active lane management, ramp metering, traveller information systems, e-tolling and other well-established systems.Austrade: https://www.austrade.gov.au/future-transport/further-information/
Technologies developed in Australia have been employed to alleviate congestion and improve safety and traffic conditions by:
- Improving traffic management
- Increasing motorway efficiency
- Building smart motorways.
The future urban mobility program at Swinburne researches ways to create safe and resilient urban transport and mobility solutions that enhance access to services, places and economic opportunities and improve the quality of life for citizens.
Watch the video below to learn more about automatic passenger counting technologies (iMOVE CRC Project).
Insert video here.
Protecting Cyber-Physical System assets is a vital part of any organisation’s cyber-security defence plan. Technical specialists designing Cyber-Physical Systems must be familiar with security and privacy risks and techniques that relate to both the cyber and physical components, as well as the entire integrated system. Cyber-Physical Systems are particularly vulnerable to cyber-attacks as they rely on wireless connections for large numbers of physically distant components.

As CPS often involve the extensive use of wireless connections to integrate cyber and physical components into an autonomous system, setting up robust cyber-security measures can be a challenge. With CPS uptake possibly increasing across a range of industries in the foreseeable future, Researchers and Technical Specialists have focused on finding solutions to possible CPS security vulnerabilities, threats and attacks.
Learn about common issues for CPS security arising from either accidental or deliberate system.
- Operating system vulnerabilities
- Sensor variable limit changes, with potentially catastrophic effects on manufacturing processes
- Computational complexity causing unexpected issues
- Big Data security – data sets too big for conventional information processing system
- IoT storage issues – widely distributed systems reliant on wireless technology present security challenges
- Vulnerability of critical infrastructures
- Breaches of information privacy.
Some of these issues can be addressed using cryptographic algorithms and protocols to develop security and privacy solutions. Most cyber-security plans aim to provide a secure, accurate, reliable, efficient and safe CPS environment. They require a more complex and innovative approach to protect evolving technologies.
Cyber security has never been more important, both as an enabler for Australian industry and as a source of economic growth itself. At present, Australia's cyber security sector is small; however, it is forecast to triple its revenue over the coming decade due to increased demand for cyber security products and services.CSIRO: https://www.csiro.au/en/Do-business/Futures/Reports/Cyber-Security

Simple cyber security or physical security approaches used in the past can no longer adequately protect a CPS, as the complex level of integration and communication between components across the different layers of CPS architecture can introduce vulnerabilities.
It is vital that cyber security be considered carefully during the design stage of a CPS to protect sensitive or private data to ensure user privacy, as well as the system's trustworthiness. Security and privacy attacks on a CPS may be due to the interconnection between devices and between devices and the internet. These issues arise due to the actions of malicious users or unauthorised third parties.
Data security and privacy are important issues that present major challenges to CPS security. This includes protecting data integrity, authenticity and most importantly, confidentiality.
Although organisations responsible for the operation and security of a CPS do take steps to protect system data from being compromised and the privacy of information stored on their system, users should seek advice on protecting their own private information from reputable sources.
One of the most effective ways to protect your digital accounts is using Multifactor Authentication (MFA).
Watch the following video from the Australian Cyber Security Centre on MFAs.
For more go to the Australian Cyber Security Centre website: https://www.cyber.gov.au/

Summary
This module explored the nature of Cyber-Physical Systems, the basics of how they work and their application involving Industry 4.0 technologies. Many of these complex systems, such as traffic light management systems, though seemingly simple, have been upgraded and transformed as each phase of industrial revolution has evolved into the complex automated monitoring and control system we now have today.
The basics of Cyber-Physical System architecture were introduced, some key applications of Cyber-Physical Systems were covered in more detail, and the security and privacy issues involved when using Cyber-Physical Systems were raised. Take the knowledge check below to test your understanding of this module.
Knowledge Check
Insert activity here.
Below are some links to find out more about Cyber-Physical Systems.
Watch the following video to learn more about the Smart Cities Research Institute.
Links:
- Smart Cities Research Institute, Swinburne:
https://www.swinburne.edu.au/research/institutes/smart-cities/ - An article by Hussein Dia, Professor of Future Urban Mobility, Swinburne - Smart tech systems cut congestion for a fraction of what new roads cost:
https://theconversation.com/smart-tech-systems-cut-congestion-for-a-fraction-of-what-new-roads-cost-125718 - Australian Cyber Security Centre:
https://www.cyber.gov.au/ - CSIRO Article - Data Privacy - what is it, why is it important, how to ensure it, and what are its opportunities:
https://algorithm.data61.csiro.au/data-privacy-what-is-it-why-is-it-important-how-to-ensure-it-and-what-are-its-opportunities/ - CSIRO - Cyber:
https://www.csiro.au/en/research/technology-space/cyber - The Open Web Application Security Project® (OWASP):
https://owasp.org/