6 Factors to consider when choosing office software for your business
One-time-purchase or Subscription service
The more traditional option is to purchase the software suite outright—it used to be referred to as buying software 'shrink-wrapped' or 'off-the-shelf'. By doing this, you’ll own the software for as long as you want to use it.
Another option available with programs like Microsoft 365 is to purchase a subscription. With a subscription, you can easily stay on top of the latest version of the software as it is released, so you don’t have to purchase upgrades as can be the case if you own the version of the software you are using. However, the subscription is ongoing (monthly or annually) rather than a one-time expense.
The best way to compare expenses between a subscription service and a one-time software purchase is to estimate the length of time that you’ll use the software before purchasing a new version. Include the cost of the newer version in your estimates to decide which is the most cost-effective purchase.
Ease of use
Some programs are more intuitive than others. Most business professionals are already versed in Microsoft 365 to some extent. If you purchase similar or easier office software, you will not incur additional training expenses and your staff can get back into their normal routine more quickly. However, if you opt for a more complex office suite, you may need to take time to train your employees.
Compare the benefits of the program’s enhanced functionality to the expense and challenges associated with teaching your employees to use it. If the benefits (rewards) of the software’s features outweigh the costs (training and the need to pause certain aspects of your workflow during the transition), the long-term rewards may be worth it.
Software requirements
Make sure you know any specific hardware or OS requirements needed to run the software. Most business software is created to work with a specific OS, database, or even a specific hardware platform. Because of this, you need to make sure the software you choose is flexible regarding OSs, underlying databases and hardware platforms. This way, you can use the software for years to come, when the OS you are currently using may be obsolete. You will also eliminate the stress that would come with purchasing software that you cannot even use.
Security elements
Security is one of the biggest concerns for every business owner. You cannot simply trust a new piece of software to be as secure as you need it to be. Many programs outline the need to take additional security measures and learn about cloud security to protect your information adequately.
For example, Microsoft 365 advises customers not to use its product to transmit or store credit cardholder data. You will typically need to invest in additional security solutions compatible with your office software, which could also be a big cost factor, depending on the security needed. Include this in your considerations.
Scalability
Another factor that you may need to consider is if the software can scale to fit your business’s growing needs. Often, a business will wait too long before looking for a new software solution and only begin the search when they have completely outgrown their old software. Because of this, outdated software may be holding a business back from growing or taking on more work.
Be sure that your new software will be capable of growing with your business to fit your ever-evolving needs and staff growth. By choosing software that will grow with you, you invest in a product that could last you through the years.
Functionality
Nearly all companies need programs for word processing and spreadsheets, but you should dig a little deeper into your requirements to adequately determine the best software solution.
Do you use your word processor for long documents that need footnotes, endnotes and annotations, or are you interested more in e-mails or newsletters that are rich in graphics and are easy to scan? Microsoft Word is better for the first, while a program like Publisher is best for the latter.
Take the time to outline your needs and consider all of your options before investing in a new piece of software or renewing your subscription for a known favourite. Exploring a fresh approach could give your business a much-needed boost.39
Check the system requirements
If you have decided to install a new OS, you will first need to figure out which one to use. Operating systems have varying system requirements, so if you have an older computer, make sure it is compatible with a newer OS.
Most Windows installations require at least 1 GB of RAM and at least 15–20 GB of hard disk space. Also, your CPU needs to be powerful enough to run the OS you choose. Make sure that your computer can accommodate this. If not, you may need to install an older OS, such as Windows XP.
| Microsoft Windows 10 Requirements | |
|---|---|
| Required processor | 1 GHz or faster compatible processor |
| Required memory | 1 GB RAM for 32-bit; 2 GB for 64-bit |
| Required hard disk space | Up to 20 GB available hard disk space |
| Required video card | 800 × 600 screen resolution or higher. DirectX 9 graphics processor with WDDM driver |
| Required connectivity | Internet access (fees may apply) |
| Other system requirements | Microsoft account required for some features. Watching DVDs requires separate playback software. |
| Additional system requirements |
You must accept the enclosed Licence Terms, also at microsoft.com/useterms
|
Linux OSs do not typically require as much space and computing power as Windows OS. The requirements vary depending on your distribution (Ubuntu, Fedora, Mint, etc.).
Decide whether to purchase or download
Windows licenses need to be purchased. Each license comes with a key good for one installation. Most Linux distributions are free to download and install as much as possible, though some Enterprise versions are closed and require purchase (Red Hat, SUSE, etc.).40
Research your software compatibility
Ensure that the OS you want to install supports the programs you want to use. If you use Office 365 for work, you will not be able to install it on a Linux machine. There are substitute programs available, but the functionality may be limited.
Again, many games that work on Windows will not work on Linux. The number of supported titles is growing, but be aware that your library might not transfer smoothly if you are an avid gamer.
Obtain your new OS
If you have purchased a copy of Windows from a store, you may have received an installation disk with a unique product key code. If you do not have the disk but have a valid code, you can download a copy online.
If you install Linux, you can download a distro ISO (a disk image that needs to be burned to a disk or copied to a bootable USB drive) from the developer's website.
Back up your data
When a major change (such as installing a new OS) is conducted, data loss risk should be considered. This means that you may lose all of your files on the computer unless you back them up. You will need to ensure that any important files are copied to a backup location, such as the cloud, an external hard drive, or network storage, before starting the installation process.
If you are adding an OS to exist alongside your existing one, you most likely will not lose data but is still good practice to backup important files just in case. You cannot backup programs—they will need to be reinstalled once you install a new OS.

Install a new OS
Types of installation
An installation where the installer inputs the configuration information in response to prompts from a setup program is called an 'attended installation'.
In contrast, an installation that derives configuration information from a file designed for that purpose is called an 'unattended installation'.
There are 2 main approaches to performing an attended installation.
- Clean install: means installing the OS to a new computer or completely replacing the OS software on an old one. Any existing user data or settings would be deleted during the setup process. A clean install is generally seen as more reliable than upgrading. In a corporate network environment, installations are completed using 'images' (templates containing the OS and required software) so that machines use a consistent set of software and configuration options for each installation. PC vendors also use images to install new systems for sale.
- In-place upgrade: means installing on top of an existing version of the OS, retaining applications, user settings and data files. Upgrades are generally designed for home users. Upgrade software can usually be purchased at a discount.
Determine your installation order
If you install a Linux distribution that you want to run alongside Windows, you need to install Windows first and then Linux. This is because Windows has a very strict boot loader that needs to be in place before Linux is installed; otherwise, Windows may not load correctly.
Boot from your installation disk
Insert the installation disk into your optical drive or, more likely, a USB drive that installs the media through a USB port when you reboot your computer.
Normally, a computer boots from the hard drive first, so you will need to adjust some settings in your BIOS to boot from the disk drive or USB.
You can enter the BIOS by hitting the designated Setup key (common Setup keys include F2, F10, F12 and Del/Delete) during the boot process. The key will be displayed on your manufacturer's logo on the same screen.
- Once you are in the Setup menu, navigate to the Boot section.
- Set your DVD/CD drive as the first boot device. If installing from a USB drive, ensure that the drive is inserted and then select it as the first boot device.41
- Once you have selected the correct drive, save your changes and exit Setup. Your computer will reboot.
Try your Linux distribution before installing
Most Linux distributions come with a copy that can be loaded directly from the installation disk. This will allow you to 'test drive' your new OS before committing to the installation process. Once you are ready to install, click the Installation program on the desktop.
This is only possible with Linux distributions. Windows does not allow you to test out the OS before installing.
Wait for the Setup program to load
No matter which OS you choose, the setup program will need to copy some files to your computer before continuing. This can take several minutes, depending on your computer's hardware (clock) speed.
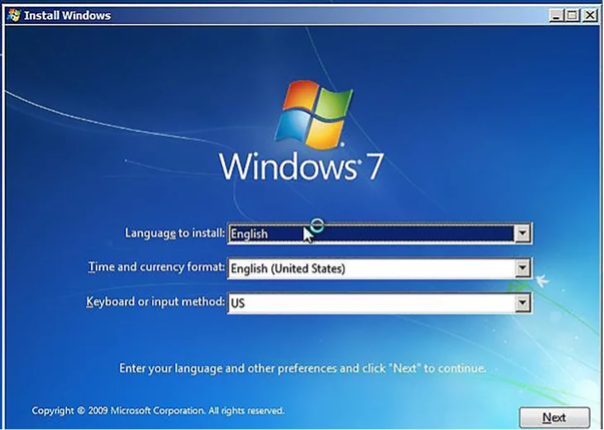
You will most likely need to choose some basic options, such as Language and Keyboard layout.
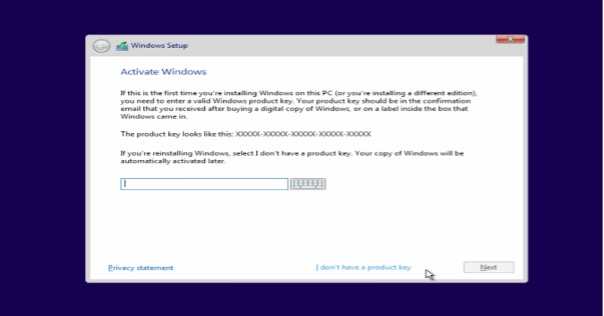
Enter your product key
If you are installing Windows 8, you will need to enter your product key before beginning the installation.
Older Windows versions will ask for the product key after installation is complete.
Linux users will not need a product key unless it is a purchased version such as Red Hat.
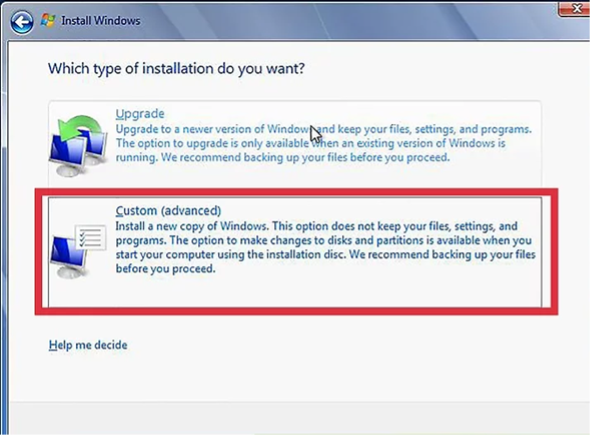
Choose your installation type
Windows will give you the option to Upgrade or perform a Custom installation.
Even if you are upgrading to an older version of Windows, it is highly recommended that you choose Custom (see below) and start from scratch. This will minimise problems arising from combining old with new settings.
If you are installing Linux, you will be given the option to install alongside your existing OS (Windows) or erase the disk and install Linux by itself.
Choose the option that best meets your needs. If you choose to install alongside Windows, you will be given the option to choose how much hard disk space you want to designate for Linux.
Format your partitions
If you are installing Windows, you will need to choose which hard drive partition you want to install it on. Deleting partitions will wipe the data on the partition and return the space to the Unallocated section. Select the Unallocated space and create a new partition.
If you install Linux, the partition needs to be formatted in the Ext4 format.
Set your Linux options
Before installation begins, your Linux installer will ask you for your time zone, and you will need to create a username and password. You will use this to log in to your Linux distribution and authorise system changes.
Windows users will fill out personal information after the installation is complete.
Wait for the installation to complete
Depending on the speed of your computer, this can take up to an hour to finish. Most installations are hands-off at this point. Your computer may reboot several times during the installation process.
Create your Windows login
Once your Windows installation is complete, you will need to create a username. You can also choose to create a password, though this is optional. After creating your login info, you will be asked for your product key.
In Windows 8, you will be asked to customise the colours first. After that, you can either log in with a Microsoft account or use a more traditional Windows username.
Install your drivers and programs
Once the installation is complete, you will be taken to your new desktop.
You can begin installing programs and ensure that your drivers are installed and up-to-date.
Be sure to install an antivirus program if you are going to be connecting to the internet!
This video goes through the process of installing Windows 10 on a new PC.
Try answering the practice questions on the learn.comptia.org website.
User Interface
A User Interface (UI) facilitates communication between an application and its user by acting as their intermediary. Each application, including the OS, is provided with a specific UI for effective communication.
The 2 basic functions of a UI of an application are to:
- take the user's inputs
- provide the output to the users.
The types of inputs taken by the UI and the types of output provided by the UI may vary from one application to another.42
A UI of any OS can be classified into one of the following types:
- Command-Line Interface (CLI)
- Graphical User Interface (GUI)
Command-Line Interfaces
A Command-Line Interface (CLI) allows the user to interact with the computer by typing in commands:
- the computer displays a prompt
- the user keys in the command and presses Enter (or return).
To perform a task in this interface, the user must type a command at the command line. When the user enters the key, the command line interpreter receives a command.
The software program is responsible for receiving and processing the commands issued by the user. After processing, the command is called a 'command-line interpreter'; the command-line interpreter displays the command prompt again and the output of the previous command issued by the user.
BASH for Linux and PowerShell in Windows are examples of command-line interpreters. Learn more by watching the explanation in the video below.
Characteristics of a CLI
- Commands must be typed correctly and in the right order, or the command will not work.
- Experienced users who know the commands can work very quickly without having to find their way around menus.
- An advantage of command-driven programs is they consume less memory and processing power compared with applications run in a GUI environment.
- Command-driven programs do not need to run in Windows.
- A command-line interface can run many programs (e.g. a batch file could launch half a dozen programs to do its task).
- An inexperienced user can sometimes find a command-driven program difficult to use because of the number of commands that have to be learnt.
Graphical User Interfaces (GUI)
Rather than typing in text commands to navigate around the computer, the user chooses options by selecting graphical representations of navigation items (such as buttons, tabs, folders and tiles) by using a suitable pointing and clicking device such as a mouse, trackball, touch screen, light pen or keyboard 'shortcuts'.
GUIs are considered user-friendly interfaces because each object is represented with a corresponding visual, such as an icon of a folder to represent a directory (see image below).43

Characteristics of GUIs
- Beginners find them much easier to use.
- They enable you to exchange information between software easily using 'cut and paste' or 'drag and drop'.
- They use a lot more memory and processing power and can be slower to use than a command-line interface if you are an expert user.
- They can be irritating to experienced users when simple tasks require several operations.
It is important to note that Windows 7-11, macOS, and Ubuntu have graphical user interfaces.
Good user interface qualities
A good interface makes it easy for the:
- users to tell the computer what they want to do
- computer to request information from the users
- computer to present understandable information.
Clear communication between the user and the computer is the working premise of good UI design.
A good user interface should:
- be attractive and pleasing to the eye
- allow the user to try out different options easily
- be intuitive, easy to use
- use suitable colours for key areas
- use words that are easy to understand for the target user.44
Directory structure models
The 'directory structure' is the organisation of files into a hierarchy of folders.
It should be stable and scalable; it should not fundamentally change, only be added to.
Computers have used the 'folder' metaphor for decades to help users track where something can be found.
Folders are very limited as an organisational structure, however. There must be one top-level organisational construct, which can only be subdivided in a limited way before the system becomes too cumbersome and breaks down.
Which is most important to divide by—date, client, project, subject matter, rating or usage?
Furthermore, information that is dependent on the folder structure is very fragile. If you remove an image from a folder that designates what that image is, that content information can be lost; however, folders provide an ideal tool for managing the data itself.
It is suggested you use folders principally for storage, rather than organisation.
Types of directory structures in operating systems
Single-level directory
The single-level directory is the simplest directory structure: all files are contained in the same directory, making it easy to support and understand.
A single-level directory has a significant limitation when the number of files increases or when the system has more than one user. Since all the files are in the same directory, they must have a unique name. If 2 users call their dataset 'test', the 'unique name rule' is violated.
Advantages
- Since it is a single directory, implementation is very easy.
- If the files are smaller in size, searching will become faster.
- Operations like file creation, searching, deletion and updating are easy in a directory structure.
Disadvantages
- The chance of name collision because of 2 like-named files is high.
- Searching will become time-consuming with larger directories.
- In this structure, you cannot group the same type of files.
Two-level directory
As we have seen, a single-level directory often leads to confusion of file names among different users. The solution to this problem is to create a separate directory for each user.
Each user has their own User File Directory (UFD) in the two-level directory. The UFDs have similar structures, but each lists only the files of a single user. The system’s master file directory (MFD) is searched whenever a new user id=s logs in. The MFD is indexed by username or account number, and each entry points to the UFD for that user.
Advantages
- Locations can be described with a full path like: /User-name/directory-name/
- Different users can have the same directory as well as the file name.
- Searching for files becomes easier due to pathname and user-grouping.
Disadvantages
- A user is not allowed to share files with other users.
- It is not very scalable; 2 files of the same type cannot be grouped under the same user.
Tree-structured directory
Once we have seen a two-level directory as a tree of height 2, the natural generalisation is to extend the directory structure to a tree of arbitrary height.45
This generalisation allows users to create their subdirectories and organise files accordingly.
A tree structure is the most common directory structure. As illustrated below, the tree has a root directory and every file in the system has a unique path to it.
▼ ROOT ├── ▼ DIRECTORY │ ├── file │ └── file └── ▼ DIRECTORY └── file
Advantages
- Very generalised, since full path names can be provided.
- Very scalable, the probability of name collision is less.
- Searching becomes very easy; we can use both absolute paths and relative.
Disadvantages
- Not every file fits into the hierarchical model; files may be saved into multiple directories.
- You cannot share files.
- It is inefficient because a file may exist in multiple directories.
Acyclic graph directory
An 'acyclic graph' is a graph with no cycle and allows us to share subdirectories and files. The same file or subdirectories may be in 2 different directories. It is a natural generalisation of the tree-structured directory.
It is used when 2 programmers work on a joint project and need to access the same files. The associated files are stored in a subdirectory, separating them from other projects and files of other programmers. Since they are working on a joint project, they want the subdirectories to be in their directories. The common subdirectories should be shared. So here, we use acyclic directories (illustrated below).
Advantages
- We can share files.
- Searching is easy due to different-different paths.
Disadvantages
- Files are shared via linking, in the case of deleting it may create a problem.
- We are left with a dangling pointer if the link is weak after deleting the file.
- In the case of a hard link, we have to delete all the references associated with it in order to delete a file.
The general graph directory structure
In the general graph directory structure, cycles are allowed within a directory structure where multiple directories can be derived from more than one parent directory (see below).
The main problem with this kind of directory structure is calculating the total size or space that the files and directories have taken.46
Advantages
- It allows cycles.
- It is more flexible than other directory structures.
Disadvantages
- It is costlier than others.
- It needs 'garbage collection'.
Virtual memory
'Virtual memory' is a management technique where secondary memory can be used as part of the main memory. It is a very common technique used in OSs on computers.
Virtual memory uses hardware and software to allow a computer to compensate for physical memory shortages by temporarily transferring data from random access memory (RAM) to disk storage. Virtual memory allows a computer to treat secondary memory as the main memory.47
Benefits of using virtual memory
- Its ability to handle twice as many addresses as main memory.
- Frees applications from managing shared memory and saves users from having to add memory modules when RAM space runs out.
- Multiple larger applications can be run simultaneously.
- Allocating memory is relatively cheap.
- Data can be moved automatically.
What is Virtual Memory? What Does it Do? The video below has the answers.
Memory management in OS
'Memory management' is responsible for managing the computer's primary memory in the OS.
The memory management function keeps track of the status of each memory location, either allocated or free. It determines:
- how memory is allocated among competing processes
- which process gets the memory
- when it receives the memory
- how much memory it is allowed
- which memory locations will be assigned
- when memory is freed or unallocated and updates the status.
Memory management is crucial to server performance.
Servers are expected to function 24/7 without delay or underperformance.48 The client expects requests to be fulfilled within a few seconds. The server, therefore, has to manage and allocate the free space.
Memory management techniques
Memory paging
'Paging' is one of the memory management techniques done by the computer OS. In this method, if the main memory (RAM) is not available, the secondary storage (disk or hard disk) is used as the main memory.
The OS retrieves the data in blocks of the same size called 'pages'.
It does have a downside—the time taken to retrieve the data from a disk is slower than retrieving data from RAM.
Memory mirroring
'Memory mirroring' is a mechanism for splitting memory into 2 channels on a memory device (such as a server).
To create redundancy, one channel is duplicated to another in memory mirroring.
Because the same physical byte may be accessed at several addresses, this strategy makes input/output (I/O) registers and memory appear to have multiple address ranges.
Memory mirroring allows for greater memory dependability as well as greater memory consolidation.
Memory overcommit
The concept is that more memory is assigned to VM (virtual machine) than physically available on the host. Most of the time, VMs do not need to use the whole allocated memory.
For instance, if there are 4 VMs, each has 1 GB of memory on a physical machine. The physical machine provides 4 GB of memory. However, those VM do not use more than 500 MB. So, if we assume that 2 GB of memory is still left untouched, we can add more VMs.
Trouble arises if all of them start using more memory than required, or anyone if anyone is allocated a significantly higher margin than the others.
Memory ballooning
This is a process in memory paging in which the spare memory space is made available to the host and will be allocated to those systems where there is an urgent memory requirement.
There are 'balloon drivers' in each VM to identify the unused memory to make it available to the host for further usage.
For instance, if 10 GB of memory had been allocated for one virtual machine, only 5 GB is in use. The remaining 50 per cent of the memory could be determined by the balloon drivers and distributed to other virtual machines (on the same host) running low in memory.
Transparent page sharing
A common scenario in which multiple virtual machines run the same OS and identical memory pages exist, resulting in redundancies. The hypervisor discovers it by assigning hash values to the pages and comparing them bit-by-bit. The comparison is made when those hash values match.
If the hypervisor detects an identical memory page on multiple VMs on a host, instead of keeping additional memory space for similar pages, it shares them among VMs with pointers. If the existing data changes, the hypervisor writes the memory to a new page and then readdresses a pointer.
In general, small memory pages are identical. The concept is, therefore, not applicable for large memory pages.49

Software testing methods
Functional testing
These testing methods are usually conducted in order. Read on to learn what is involved.
Unit testing
Unit testing is the first level of testing and is often performed by the developers.
It is the process of ensuring individual components of a piece of software at the code level are functional and work as they were designed to. Developers in a test-driven environment will typically write and run the tests before the software or feature is passed over to the test team.
Unit testing can be conducted manually, but automating the process will speed up delivery cycles and expand test coverage.
Unit testing will also make debugging easier because finding issues earlier means they take less time to fix than if they were discovered later in the testing process.
'TestLeft' is a tool that allows advanced testers and developers to shift left with the fastest test automation tool embedded in any IDE.
Integration testing
After thoroughly testing each unit, it is integrated with other units to create modules or components designed to perform specific tasks or activities.
These are then tested as a group through 'integration testing' to ensure whole segments of an application behave as expected (i.e. the interactions between units are seamless).
User scenarios often frame these tests--such as logging into an application or opening files.
Integrated tests can be conducted by either developers or independent testers and usually comprise automated functional and manual tests.
System testing
'System testing' is a black-box testing method used to evaluate the completed and integrated system, as a whole, to ensure it meets specified requirements. The functionality of the software is tested from end-to-end.
It is typically conducted by a separate testing team than the development team before the product is pushed into production.
Acceptance testing
'Acceptance testing' is the last phase of functional testing and is used to assess whether or not the final piece of software is ready for delivery.
It involves ensuring that the product complies with all of the original business criteria and meets the end user’s needs. This requires the product to be tested both internally and externally, meaning you will need to get it into the hands of your end-users for beta testing along with those of your Quality Assurance (QA) team.
Beta testing is key to getting real feedback from potential customers and can address any final usability concerns.
Non-functional testing
'Non-functional testing' methods incorporate all test types focused on the operational aspects of a piece of software. These include:
Performance testing
'Performance testing' is a non-functional technique used to determine how an application will behave under various conditions. The goal is to test its responsiveness and stability in real user situations.
Performance testing can be broken down into 4 types:
- Load testing puts increasing amounts of simulated demand on your software, application, or website to verify whether or not it can handle what it is designed to handle.
- Stress testing takes this further and gauges how your software will respond at or beyond its peak load. Stress testing aims to overload the application on purpose until it breaks by applying realistic and unrealistic load scenarios. With stress testing, you will be able to find the failure point of your piece of software.
- Endurance testing, also known as 'soak testing', is used to analyse the behaviour of an application under a specific amount of simulated load over longer amounts of time. The goal is to understand how your system will behave under sustained use, making it a longer process than load or stress testing (designed to end after a few hours). A critical piece of endurance testing is that it helps uncover memory leaks.
- Spike testing is a load test used to determine how your software will respond to substantially larger concurrent user or system activity bursts over varying amounts of time. Ideally, this will help you understand what will happen when the load suddenly and drastically increases.
Security testing
With the rise of cloud-based testing platforms and cyber-attacks, there is a growing concern and need for data security being used and stored in the software.
Security testing is a non-functional software testing technique used to determine if the information and data are protected. The goal is to purposefully find loopholes and security risks in the system that could result in unauthorised access to or the loss of information by probing the application for weaknesses.
There are multiple types of this testing method, each of which aimed at verifying 6 basic principles of security:
- integrity
- confidentiality
- authentication
- authorisation
- availability
- non-repudiation.

Usability testing
'Usability testing' measures an application’s ease of use from the end-user perspective and is often performed during the system or acceptance testing stages.
The goal is to determine whether or not an application's visual design and aesthetics meet the intended workflow for various processes (such as logging into an application).
Usability testing is a great way for teams to review separate functions, or that the system as a whole is intuitive to use.
Compatibility testing
'Compatibility testing' is used to gauge how an application or software will work in different environments.
It is used to check that your product is compatible with multiple OS, platforms, browsers or resolution configurations. The goal is to ensure that your software’s functionality is consistently supported across any environment you expect your end-users to be using.50
Optimise OS software
Optimising the OS uses various utilities to ensure that it functions at its best. You can monitor and optimise an OS such as Windows 10 using the following utilities:
- Task Manager utilities
- System Monitor
- System Tool
- Performance Logs and Alerts
- Virtual Memory
- Event Viewer
- Task Scheduler.
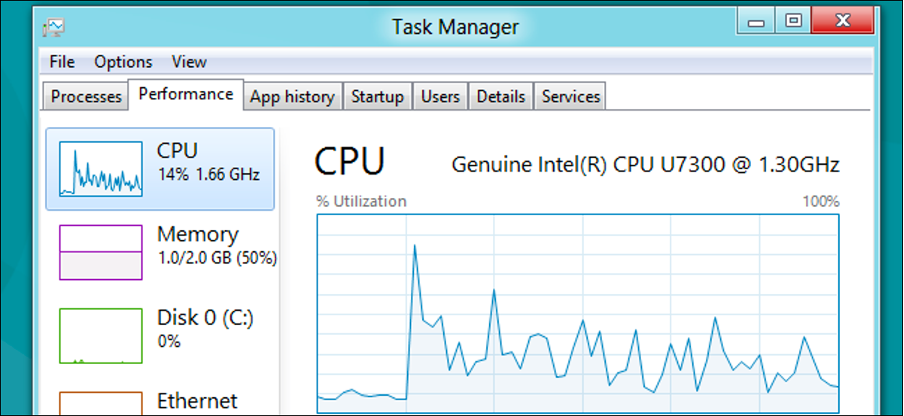
Monitoring applications with Task Manager
The Task Manager utility provides information about the computer's performance and displays details about the program and processes' (an executable program such as Windows Explorer) running.
Performance logs and alerts
Performance logs and alerts (PLA) is a Windows utility that monitors the use of OS resources. Counter logs can be created (manually or on a defined schedule) to record data about hardware usage and the activity of system services (e.g. the CPU percentage used).
Trace logs can also be created to record detailed systems application events such as input/output operations or a page fault. An alert can be generated when a specific event exceeds or falls below or above a specified value (e.g. when CPU usage goes over 20 per cent, a message can be sent to the user).
Virtual memory
Virtual memory (as briefly discussed earlier) uses hard disk space to supplement Random Access Memory (RAM). For example, suppose you simultaneously load several programs such as an email program, Internet browser, Word Processor and video software. In that case, there may not be enough RAM installed to hold all the programs. With virtual memory, the computer moves programs that have not been used recently to the hard disk, which frees up memory to load the new programs. Moving data that is not immediately required onto a reserved area of the hard disk is known as 'paging' or 'swapping'.51
The following video contains tips for optimising Windows 10 performance.
Knowledge check
Complete these three activities.
Using Task Manager, System Monitor, System Tools, and any other performance and monitoring tools you like, record your computer's current performance. Are there any actions you can take to enhance it?
Share your monitoring, optimisation process, and results (if any) in the forum.
