In this section you will learn to:
- Invite stakeholders to assist in the identification of risks
- Research risks that may apply to scope
- Document risks that apply to the scope, in consultation with relevant parties
Supplementary materials relevant to this section:
- Reading C: Preliminary Risks
- Reading D: Reporting Risks

The most important thing when identifying risks is to be as comprehensive as possible. This would not be possible without the participation of key stakeholders. Some critical pieces of legislation, such as the Work Health and Safety Act, also requires employers to consult with workers about risk management activities. Even if it is not mandated, it is highly beneficial to foster stakeholder participation by inviting as many key stakeholders as possible to participate in the risk identification process (Archer, Borthwick, Travers and Ruschena, 2020). Not only do stakeholders provide a variety of perspectives but each stakeholder knows best the risks that are likely to affect their interests (Hopkin 2013). Stakeholder participation can come in the form of:
- Formal meetings
- Informal catch ups
- Brainstorming sessions
- Online discussions
- Phone or video conferences
- Interviews
- Surveys
Once key stakeholders have been invited to participate, you may need to facilitate their participation in the risk identification process. One of the best tools to facilitate risk identification is effective questioning.
Different types of questions are designed to elicit different types of responses. Hogan (2003) identifies several types of questions each with its own purpose, for example:
- Open questions - these questions usually start with who, what, where, when why or how. Open questions can be answered in a variety of ways and have no fixed or predetermined response. These questions are useful for encouraging creativity, generating ideas and problem solving.
- Closed questions - these questions can only be answered with either yes, no or a similarly brief, predetermined response. Closed questions can be valuable when you need an answer quickly or are seeking agreement or consent.
- Probing questions - also known as follow up questions, probing questions are used to seek more information. For example, “can you go into more detail?” or “can you tell me more about that?” are both probing questions.
- Naive questions - naive questions are used by the asker to seek clarification or explanation. They are often used in education and training environments when the facilitator feels that some participants require clarification but are too shy to ask themselves.
- Rhetorical questions - rhetorical questions require no answer, usually because the answer is implied. They are usually used to emphasise a point or to create interest
- Leading questions - these questions are designed specifically to elicit a particular response or type of response. Some leading questions can be used to manipulate the respondent.
Judge a man by his questions rather than by his answers.Voltaire
Reflect
Imagine you are hosting a risk identification session to identify risks at your work or home. Who would you invite to the session and why? What questions would you ask?

When identifying risks, there are several different types of risks to be aware of. Risks can be related to premises, product, purchasing, people, procedures, protection, process, performance planning or policy. Each of these factors will now be discussed in more detail.
- Premises - there are a range of risks associated with the premises where work is performed. Premises may pose risks in the form of unsuitable or unsafe premises, ownership or leasing requirements, repairs, location, environment, security, and competition.
- Product or Service - risks associated with products or service may include demand for the product or service, availability of suitable workforce, employment law, product safety, consumer protections, licensing, copyrights or patents, competition, demographics, storage, and delivery.
- Purchasing - purchasing refers to the risks associated with the purchasing or procurement function of the organisation. These risks may relate to the organisation’s policies and procedures, cost of supplies, fuel and transportation costs, technology and obsolescence, environmental issues, and reputation.
- People - it is important to consider all employees when assessing risks associated with people. Those risks may be related to the range of skills required and the skills available, the training required, the organisational culture, legislative requirements such as equal opportunities and anti-discrimination, benefits, and entitlements.
- Procedures - procedural risk factors relate to the suitability of procedures now and in the future. Procedural risk factors may include willingness of workers to accept change, legislative requirements, security procedures, and industry standards.
- Protection - protection refers to the risks associated with protecting people, premises, materials, intellectual property, data and the environment. Risks associated with protection may relate to motivation and commitment, flexible working hours, bullying and harassment, renewable energy, health and safety, password protection, and data security.
- Process - process risks will vary greatly depending on the specific organisation and industry. Process risks may involve stress levels, turnover, seasonal demand, making work accessible for people with disabilities, job descriptions, keeping processes up to date, increased use of technology, or differences in local requirements.
- Performance - performance risks refer not only to employee performance but performance in a whole range of areas such as safety, environment, product or service and diversity. Performance risks may relate to performance measures and standards, training, feedback, reporting of incidents, penalties or fines and bad publicity.
- Planning - planning risks should be considered at both the operational and the strategic level. Planning risk factors may relate to insufficient input from all levels, lack of understanding, legislative requirements, access to relevant data, awareness of competition, industry trends, interest rates, economic conditions, and unpredictable events.
- Policy - policy risks may relate to employment policies, legislative policies, security policies, competitive policies and financial policies. Policy related risk factors may include consultation, equal opportunities, industrial relations, health and safety, privacy, sensitive information, record keeping, fraud, and insurance
Read
Reading C: Preliminary Hazards
Reading C looks at a Preliminary Hazard List (PHL) which is commonly used to identify and compile a list of potential, significant hazards associated with a system’s design. You will notice that the purpose of a PL is to initially identify the most evident or worst-credible hazards that could occur in the system being designed.

The next stage of risk identification is to research risks that may apply to the scope. Remember that the scope is the area included in risk management and may be a project, a business unit or function, the internal or external environment or the whole organisation (however for the purposes of this unit we will be using the term organisation throughout). Research into risks that could affect the scope may include:
- Data or statistical information
- Information from other business areas
- Lessons learned from other projects or activities
- Market research
- Previous experience
- Public consultation
- Review of literature and other sources
Primary Research
Primary research or original research is research that hasn’t already been conducted by somebody else. It is collected specifically for the purpose of the research project being undertaken. According to Dwyer (2017), conducting primary research is a process which includes the following five stages:
- Identify problem
- Plan research
- Conduct research
- Analyse results
- Draw conclusions
When identifying risks, sources of primary research may include:
- Observation of behaviour, processes or events.
- Interviews with key stakeholders.
- Surveys or questionnaires of key stakeholders.
- Sales records, financial statements, incidents reports, and other records.
Secondary Research
Unlike primary research, secondary research is based on research which has already been conducted, analysed and written about by somebody else. Since secondary research is somebody else’s analysis, it is important to evaluate the information for objectivity, credibility and relevance before using it to identify risks (Dwyer, 2017). When identifying risks, sources of secondary research may include:
- Books
- Journal articles
- Newspapers and magazines
- Industry or government reports
- Online resources

The final stage of risk identification is to generate a list of risks that apply to the scope. There are several tools and techniques which can be used to identify risks such as brainstorming, checklists, scenario analysis, flowcharts and fishbone diagrams. Each of these techniques will now be discussed in more detail.
Brainstorming
Brainstorming is one of the most popular business techniques for idea generation and issue or problem identification. Brainstorming can be especially useful if there is little or no evidence or data available making it ideal for identifying risks. Brainstorming works by assembling a group of people familiar with the topic (in this case the organisation) and facilitating a conversation whereby participants are encouraged to generate as many ideas or risks as possible. For brainstorming to work the emphasis must be on quantity of ideas rather than quality. Brainstorming usually ceases after an allotted time period, when no more ideas can be generated or when goals of the brainstorming session have been achieved.
Checklists
Checklists are a popular technique for risk identification. Many organisations keep a risk register which forms the basis of a risk identification checklist. Unfortunately, this method is usually inadequate for identifying new or previously unknown risks. A better option would be to identify all the business units and their functions and then systematically list the risks associated with each function. Another option would be to use the types of risks (e.g., premises, product, purchasing, people, procedures, protection, process, performance, planning and policy) as a starting point and systematically list the risks arising from each risk factor.
Scenario Analysis
Scenario analysis is a planning tool used to understand the business impact of major internal or external events such as system failures, economic downturns or political shifts. In scenario analysis the risk professional creates a number of scenarios or narratives (usually three) describing an event or a series of events. Usually, the three scenarios generated are the best case, the worst case and the most likely scenario. Often there is little or no data available for the scenarios described in these analyses; however, the technique is still a valuable tool for risk identification because it encourages participants to ask, “what if?”
Flowcharts
Flowcharts are a diagram commonly used to describe the steps in a process. They are also a popular tool to aid risk identification. When developed correctly, organisational flowcharts can provide a unique insight into the stages or processes likely to generate risks. A flowchart consists of common shapes and symbols used to represent the different stages of a process. The start and end points are commonly represented by rounded rectangles, actions or steps are represented by rectangles, and decisions or questions are represented by diamonds. The figure below represents a typical flowchart.
Reflect
Think of a task or process you regularly perform either at work or at home (e.g., checking emails, filing, or grocery shopping). Draw a flowchart depicting the process. By examining the flowchart can you identify any potential risks in the task or process?
Fishbone Diagrams
Fishbone diagrams (also known as Ishikawa or cause and effect diagrams) are a tool used to show the relationship between problems and their causes. In risk management the fishbone diagram is used to identify risks which could potentially lead to problems. Each cause represents a different category. Categories can be business units or functions, risk factors (premises, product, purchasing, people, procedures, protection, process, performance, planning and policy) or any other category that makes sense for the organisation. The sub causes then, are risks associated with each category.
The figure on the following page represents the typical structure of a fishbone diagram.
The following fictional case study has been developed to assist your learning in this unit. In the case study below the operations manager of a small manufacturing business generates a list of risks using the tools and techniques described in this section.
Case Study
Stella Shoes
Stella Shoes is an Australian owned footwear manufacturer with a small factory located in New South Wales. The company consists of the CEO, production manager, 12 craftspeople that make up the production team, and various other support staff.
The CEO of Stella Shoes has asked the production manager Wendy Olsen to create a risk management plan for her department. Wendy’s first step was to research risks which might apply to her department. During her research she came across the following graph.
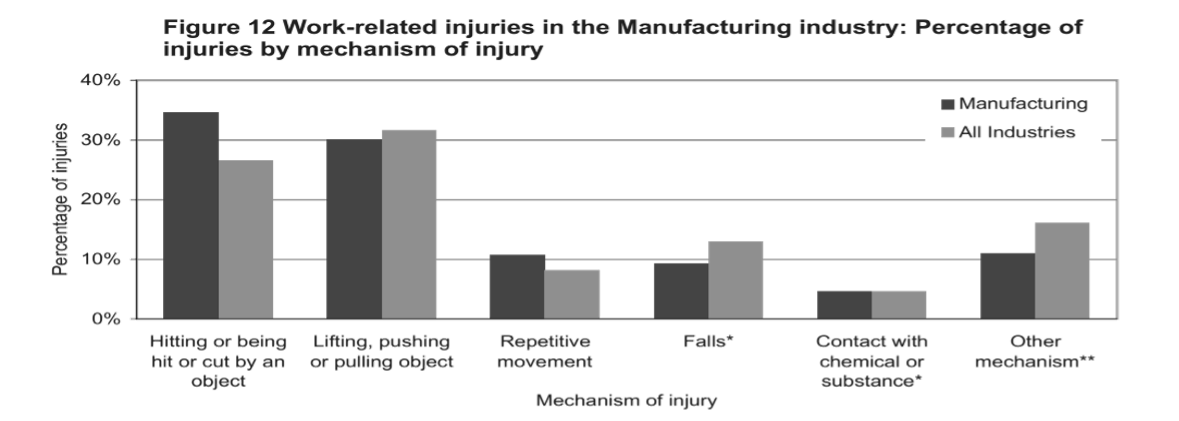
Next Wendy invited the production team to a risk identification session. During the session the team developed the following flow chart in order to identify where in the production process risks were likely to occur.
Based on her research, the input from the production team and the tools and techniques used, Wendy was able to generate the following list of risks:
- Being hit or cut by an object
- Lifting, pushing or pulling an object
- Strains or sprains from lifting materials
- Cuts, broken bones or bruises from falling or dropped materials
- Cuts or lacerations from cutting machines and tools
- Puncture wounds from sewing machines
- Puncture wounds from tacks or nails
- Cuts, broken bones or bruises from hammering tools
- Rashes or burns from chemicals
- Electrical or chemical fires
- Respiratory diseases caused by chemical inhalation
- Theft of tools, materials or products
- Wastage
Reflect
Consider the above Case Study involving Wendy. What other tools or techniques could she have used to help her identify risks? Can you identify any risks that Wendy wasn’t able to?
Reading
Reading D: Reporting Risks
Reading D investigates reporting tools that empower the operational risk function with the opportunity to contribute to the business decision making at the firm. This reading considered loss data reporting in some depth and also discusses reporting on the other elements in the framework, including risk and control self-assessment, key risk indicators, and scenario analysis.
This section of the module you have focused on identifying risks. In this section you have learned how to invite key stakeholders to participate in risk identification and some useful facilitation techniques. You also learned research principles for identifying risks as well as various types of risks. Finally, you learned some tools and techniques which can be used to generate a list of risks.
