In this topic, we will explore essential techniques and strategies used to protect and secure computer networks, as well as the concept of obfuscation in the context of cybersecurity.
In today’s interconnected world, computer networks play a critical role in facilitating communication, data transfer, and information exchange. However, these networks are also vulnerable to various threats and attacks from malicious actors. It is crucial to understand and implement effective measures to protect networks from unauthorized access, data breaches, and other cybersecurity risks.
By the end of this topic, you will have gained a solid understanding of network protection techniques and the concept of obfuscation in the context of cybersecurity. You will be equipped with the knowledge and skills necessary to implement effective network security measures and protect critical information and communications within computer networks.
A Firewall is responsible for blocking either incoming or outgoing traffic from the internet to your computer. A firewall is a type of cyber-security tool that is used to filter traffic on and secure a network.
Firewalls can be software, hardware, or cloud-based, with each type of firewall having its own unique advantages and disadvantages.
Types of Firewalls
- Packet-Filtering Firewalls
- Stateful Packet Inspection (SPI)
- Next-Generation Firewalls (NGFW)
Packet-Filtering Firewalls
Packet-filtering firewalls are the most basic type of firewall and operate at the network layer (Layer 3) of the TCP/IP protocol stack. They examine individual packets of data as they pass through the firewall and make decisions based on predefined filtering rules. These rules specify which packets are allowed or denied based on criteria such as source IP address, destination IP address, protocol type, and port numbers.
| Advantages | Disadvantages | Protection Level | Who is it for: |
|---|---|---|---|
|
|
|
|
Stateful Inspection Firewalls
Stateful packet inspection is an advanced firewall technology that goes beyond the capabilities of packet-filtering firewalls. It not only examines individual packets but also maintains a record of the state of network connections. This means that it can analyze the entire network communication session and make filtering decisions based on the context and history of the traffic. SPI firewalls keep track of the source and destination IP addresses, port numbers, and connection state (e.g., established, closed) to determine if packets are legitimate or part of an ongoing authorized session.
| Advantages | Disadvantages | Protection Level | Who is it for: |
|---|---|---|---|
|
|
|
|
Additional Reading
Please read for more information about the stateless and stateful protocol.
Next-Generation Firewalls
Next-generation firewalls combine the capabilities of traditional packet-filtering firewalls and stateful packet inspection with additional advanced features. NGFWs incorporate deep packet inspection (DPI) techniques to analyze the content of packets and perform more in-depth inspection of network traffic. They can examine not only packet headers but also the payload of the packets, allowing for more granular control and threat detection. Next-generation firewalls may incorporate other technologies as well, such as intrusion Detection/Intrusion prevention systems (IDS/IPSs), and malware scanning that work to automatically stop attacks against your network. NGFW’s are capable of monitoring network protocols from Layer 2 & Layer 7 of the OSI model)
| Advantages | Disadvantages | Protection Level | Who is it for: |
|---|---|---|---|
|
|
|
|
PCI and HIPAA Definitions
- Research the differences between stateful vs. stateless protocol
Intrusion Detection Systems (IDS) and Intrusion Prevention Systems (IPS) are security technologies used to detect and prevent unauthorized access and malicious activities within computer networks. While they have similar goals, there are some differences in their functionalities.
Intrusion Detection System (IDS)
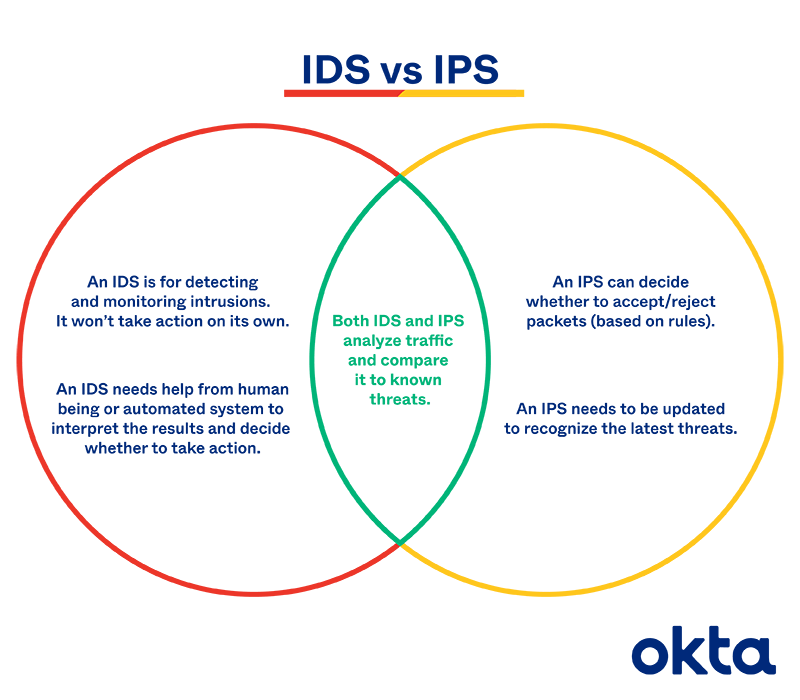
An Intrusion Detection System is a security tool designed to monitor network traffic and system activities to identify and alert administrators about potential security breaches or suspicious activities. IDS analyzes network packets, log files, and system events to detect patterns or signatures of known attacks or anomalies that may indicate an ongoing intrusion attempt. It operates in a passive mode, meaning it detects and reports security incidents but does not actively take action to prevent or stop them. IDS can be deployed at various points within a network, such as at the network perimeter, on specific hosts, or in the form of network-based or host-based IDS.
Intrusion Prevention System (IPS)
An Intrusion Prevention System is an advanced security technology that not only detects security threats but also actively takes preventive measures to block or mitigate them. IPS combines the functionalities of IDS with additional capabilities to actively intervene and prevent malicious activities. It can automatically respond to detected threats by blocking suspicious network traffic, terminating connections, or applying access control policies to protect vulnerable systems. IPS can operate in-line, meaning it sits directly in the network traffic path and can block or modify packets in real-time, offering immediate protection against known and unknown threats. IPS can also utilize signature-based detection, anomaly detection, and behavioural analysis techniques to identify and prevent attacks.
IDS and IPS Compared
| Similarities | Differences |
|---|---|
|
|
A Virtual Private Network (VPN) is a service that helps you stay private online. A VPN establishes a secure, encrypted connection between your computer and the internet, providing a private tunnel for your data and communications while you use public networks. It hides your IP address from 3rd parties and even from ISP (Internet Service Providers).
While many encryption methods, or algorithms, exist, most VPNs use the 256-bit AES (Advanced Encryption Standard) algorithm.
Virtual Private Network (VPN) is a connection between a VPN service and a VPN client. It is a secure tunnel across the internet.
VPN Protocols
Virtual Private Network (VPN) protocols are sets of rules and procedures that govern how VPN clients and servers establish secure connections and encrypt data for secure communication over public networks. There are several VPN protocols available, each offering different levels of security, performance, and compatibility. Here's an overview of some common VPN protocols:
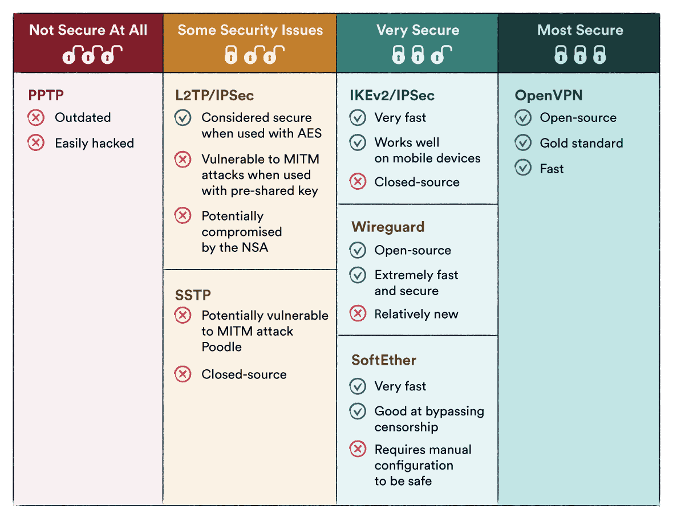
- PPTP (Point-to-Point Tunneling Protocol): PPTP is one of the oldest VPN protocols. It is widely supported and relatively easy to configure. However, it has known security vulnerabilities and is considered less secure compared to other protocols. PPTP is often used for legacy systems or situations where high security is not a primary concern.
- L2TP/IPSec (Layer 2 Tunneling Protocol with IP Security): L2TP/IPSec combines the best features of L2TP and IPSec. L2TP provides the tunnelling mechanism, while IPSec provides encryption and authentication. It offers robust security and is supported by most modern operating systems. L2TP/IPSec is commonly used for remote access VPNs.
- OpenVPN: OpenVPN is an open-source and highly configurable VPN protocol. It is known for its strong security, flexibility, and cross-platform compatibility. OpenVPN uses SSL/TLS protocols for encryption and can operate over both TCP and UDP. It is widely regarded as one of the most secure VPN protocols and is often the preferred choice for businesses and privacy-conscious individuals.
- IKEv2 (Internet Key Exchange version 2): IKEv2 is a modern VPN protocol that provides a high level of security and stability. It is designed to establish and maintain VPN connections even when network connectivity changes, such as switching between Wi-Fi and mobile networks. IKEv2 is commonly used on mobile devices and is known for its fast connection establishment and reconnection times.
- WireGuard: WireGuard is a relatively new VPN protocol that aims to provide simplicity, speed, and strong security. It is designed to be lightweight and efficient while offering robust encryption. WireGuard has gained popularity for its easy setup and excellent performance.
For more information about VPN protocols, read these articles:
Comparison and Summary of VPN Protocol
When selecting a VPN protocol, considerations such as security requirements, compatibility with client devices and servers, and network performance should be taken into account. It is essential to choose a protocol that aligns with your specific needs and provides the appropriate balance between security and performance. Additionally, it is worth noting that some VPN services may support multiple protocols, allowing users to choose the one that best suits their requirements.
- Use OpenVPN when available.
- Stay as far from PPTP as you can.
- Avoid SSTP if possible.
- L2TP is a good choice if implemented correctly, but not recommended.
- IKEv2’s open-source iterations are a decent alternative to OpenVPN.
TOR, short for The Onion Router, is a free and open-source software that provides anonymous communication over the Internet. It aims to protect users' privacy by routing their internet traffic through a network of volunteer-operated servers called "nodes" or "relays."
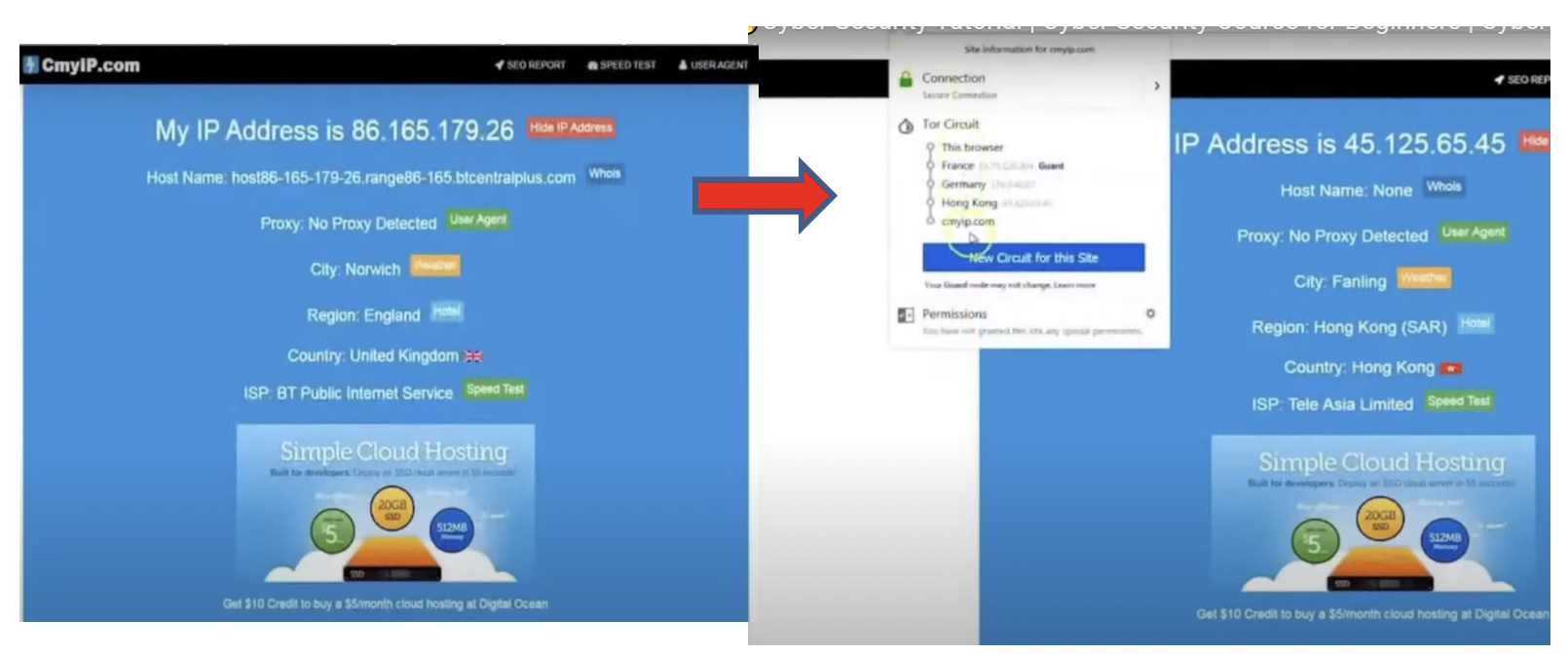
The TOR network works by employing a technique called onion routing. When a user connects to TOR, their internet traffic is encrypted and passed through a series of randomly selected TOR relays before reaching their destination. Each relay in the network only knows the IP address of the previous relay and the next relay, ensuring that no single relay can trace the entire communication path.
TOR is commonly used by journalists, activists, whistleblowers, and individuals who seek to protect their online privacy and anonymity.
How TOR works
By routing internet traffic through multiple relays, TOR helps to mask the user's IP address and location, making it difficult to track their online activities. Additionally, TOR can provide access to websites and services that may be blocked or restricted in certain regions.
- Onion Layering: TOR creates multiple layers of encryption for user data. Each relay removes a layer of encryption, revealing the routing instructions to the next relay, hence the term "onion routing."
- Entry Node: When a user connects to the TOR network, their internet traffic is encrypted and sent to an entry node, which is the first relay in the TOR circuit. The entry node only knows the IP address of the user.
- Intermediate Nodes: The encrypted traffic is then passed through a series of intermediate relays. At each relay, a layer of encryption is removed, revealing the routing instructions for the next relay.
- Exit Node: Finally, the traffic reaches the exit node, which is the last relay in the TOR circuit. The exit node decrypts the final layer of encryption and sends the data to its intended destination on the internet.
It's important to note that while TOR provides anonymity and privacy to some extent, it does not guarantee complete anonymity. Users should also be aware that TOR usage itself can attract attention from authorities, and they should exercise caution when accessing sensitive or illegal content.
| TOR | VPN | |
|---|---|---|
| Pros |
|
|
| Cons |
|
|
For more information, read the following article:
https://nordvpn.com/blog/tor-vs-vpn/
In the Forum ‘Learning Activity: VPN vs. TOR’ discuss the differences and your views on VPN vs. TOR
Use a Dark Web Monitor to:
- Monitor all network traffic for outbound TOR connections:
- Including TOR proxies
- This will allow you to identify staff using TOR on your network and may be indicative of a ransomware attack.
- Block TOR exit nodes: There are public lists available for these, so the null route (blackhole) uses proxy/URL filtering/reputational analysis to monitor or block them.
- Understand what the "Dark Web" might contain and how this may affect your company, brand(s), products, and services: especially important that you check if accounts for your organization: Especially important that you check to services you offer are being sold (either stolen accounts or fresh accounts/digital products, etc.)
- Education, education, education: Backed up with policies clearly stating that TOR and other P2P software is not approved for use, same with Bitcoin mining.
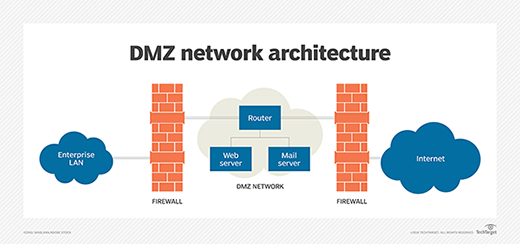
DMZ stands for Demilitarized Zone and comes from the geographic buffer zone that was set up between North Korea and South Korea at the end of the Korean War.
In the context of computer networks and security, a DMZ refers to a separate network segment that sits between an internal network (such as a company's private network) and an external network (typically the Internet). The purpose of a DMZ is to provide an additional layer of security by isolating publicly accessible services and systems from the internal network.
In a typical network setup, the internal network contains sensitive resources like databases, file servers, and internal applications that need to be protected from unauthorized access. On the other hand, there are certain services that need to be accessible to external users, such as web servers, email servers, and FTP servers.
By placing these public-facing servers and services in the DMZ, organizations can create a buffer zone that acts as a barrier between the external network and the internal network. This separation helps mitigate the risk of direct attacks against internal resources in case publicly accessible services are compromised.
The DMZ, also known as a perimeter network, is typically implemented using firewalls and network segmentation techniques. Firewalls are used to control and monitor traffic between the DMZ and the internal network, as well as between the DMZ and the external network. Access controls, such as firewall rules and security policies, are put in place to allow or restrict specific types of traffic to and from the DMZ.
The DMZ architecture allows organizations to provide limited access to certain services while minimizing the potential damage in case of a security breach. It adds an extra layer of protection by separating the public-facing systems from the internal network where critical assets reside.
Some of the most common of these services in DMZ include web, email, domain name system, and File Transfer Protocol.
Implementation of a DMZ
- Through the use of a single (1) firewall
- Through the use of two (2) firewalls
- The first allows external traffic flow to the DMZ
- The second allows traffic to flow from the DMZ to the internal network
Single Firewall DMZ
This approach uses a single firewall that has a connection to each of the three areas (Internet, DMZ and Protected). It will use different rules depending on which of the areas the traffic has been flowing between.
- When traffic comes from the internet, it will need to pass through the firewall and is then forwarded into the DMZ area.
- When the traffic is sent from the DMZ, it will pass through the same firewall and be forwarded to the protected network.
Double Firewall DMZ
This approach uses one firewall to protect the DMZ from the Internet, while the other protects the secure network from the Internet.
Each firewall has 2 interfaces for this purpose:
- when traffic comes from the internet, it is checked at the first firewall, then it arrives at the server in the DMZ, and the DMZ server passes the packet on
- Then it is checked by the second firewall before it is allowed to access the secure network.
Pros and Cons of Each DMZ Implementation
| 1 Firewall | 2 Firewall | |
|---|---|---|
| Pros |
|
|
| Cons |
|
|
Most modern applications of the DMZ employ the use of 2 firewalls as it is the most secure option.
To increase protection, different brands for each of the firewalls are recommended so that if there is a flaw in the first, the same flaw won’t be found in the second.
It's important to note that the DMZ alone does not guarantee absolute security. Proper configuration, regular updates, and monitoring are essential to ensure the effectiveness of the DMZ as part of an overall network security strategy.
Honeypots are a cybersecurity technique used to deceive and monitor malicious actors by creating a trap or decoy system that appears to be a valuable target. A honeypot is designed to attract attackers and divert their attention away from critical systems or networks. Honeypots are called so because they are designed to act as enticing bait, similar to how a pot of honey attracts bees. The concept behind the name is that attackers, like bees, are drawn to the perceived value or vulnerability of the honeypot, just as bees are attracted to the sweetness of honey.
The primary purpose of a honeypot is to gather information about the tactics, techniques, and tools used by attackers. By luring potential attackers into the honeypot environment, security professionals can gain valuable insights into their behaviour, motivations, and methods of attack. This information can then be used to strengthen overall cybersecurity defences and improve incident response capabilities.
Types of Honeypots
Honeypots can be classified into two main types:
- Production Honeypots: These honeypots are deployed within a production network to imitate real systems and services. They are designed to mimic actual systems and generate realistic network traffic to attract and monitor attackers. The goal is to detect and analyze attacks in a production environment, providing insights into the specific threats targeting an organization.
- Research Honeypots: Research honeypots are primarily used for collecting data and conducting research on the latest attack techniques and trends. They are often implemented in controlled lab environments and are not part of a production network. Research honeypots provide a controlled environment for studying and analyzing attacks without posing any risk to critical systems.
Implementation of Honeypots
A honeypot operation consists of a computer, applications, and data that simulate the behaviour of a real system like a financial system, or IoT system but is completely isolated and closely monitored. Honey pots can be placed inside the DMZ or outside the external firewall to detect the attempt to the internal network.
In the DMZ:
Outside the external Firewall:
Pros and Cons of Honeypots
| Honeypot | |
|---|---|
| Pros |
|
| Cons |
|
Use of Honeypots
While beneficial, the average small to medium enterprise would not use Honeypots. Generally, these are utilised in the following institutions:
- Large Enterprises and Corporations: Large enterprises and corporations across industries, such as finance, healthcare, technology, and manufacturing, can deploy honeypots to monitor and detect threats targeting their critical assets and systems.
- Government Agencies: Government entities at various levels, including defence, intelligence, law enforcement, and national security agencies, can employ honeypots to gather intelligence on potential cyber threats and protect sensitive information.
- Research Institutions: Academic institutions, cybersecurity research labs, and think tanks may use honeypots for studying and analyzing the latest attack techniques, developing countermeasures, and contributing to the overall understanding of cybersecurity threats.
- Internet Service Providers (ISPs): ISPs can deploy honeypots to detect and mitigate attacks targeting their network infrastructure, as well as to gather intelligence on botnets, malware propagation, and other malicious activities.
- Security Service Providers: Companies offering managed security services or cybersecurity consulting may utilize honeypots as part of their services to proactively detect, analyze, and respond to threats on behalf of their clients.
- Critical Infrastructure Operators: Organizations operating critical infrastructure, such as energy, transportation, and telecommunications, can use honeypots to enhance their overall security posture and detect potential attacks on their systems.

In the world of cybersecurity, different types of hackers exist, each with their own motivations and intentions. Here are some common types of hackers:
- White Hat Hackers: Also known as ‘ethical hackers’ or security researchers, white hat hackers use their skills for good. They work legally and ethically to identify vulnerabilities in systems, networks, or applications and help organizations improve their security. They often work as cybersecurity professionals, consultants, or freelance researchers.
- Black Hat Hackers: Black hat hackers are individuals who engage in hacking activities for malicious purposes. They unlawfully exploit vulnerabilities to gain unauthorized access to systems, steal sensitive information, cause damage, or engage in other criminal activities. They are commonly associated with cybercrime and illegal hacking activities for monetary gain.
- Grey Hat Hackers: Grey hat hackers fall somewhere in between white hat and black hat hackers. They may not have malicious intent, but they operate outside the boundaries of legal and ethical hacking. Grey hat hackers often discover vulnerabilities and expose them publicly without permission, often with the intention of bringing attention to security flaws or pressuring organizations to fix them. Sometimes the grey-hat hackers also ask for money for the spotted vulnerabilities.
Hackers can also fall outside of the above categories, these types are often referred to as:
- Script Kiddies: Script kiddies are individuals with limited technical skills who use pre-existing tools, scripts, or software to carry out basic hacking activities. They typically lack in-depth knowledge and understanding of hacking techniques but still engage in low-level hacking attempts, such as launching basic DDoS attacks or using readily available hacking tools.
- Hacktivists: Hacktivists are hackers who engage in hacking activities to promote a particular social or political cause. They often target organizations or websites to spread their message, raise awareness, or disrupt operations. Hacktivist groups may deface websites, leak sensitive information, or carry out distributed denial-of-service (DDoS) attacks.
- State-Sponsored Hackers: State-sponsored hackers are individuals or groups supported by government entities to conduct cyber espionage, gather intelligence, carry out cyberattacks on other nations, or engage in disruptive activities. They often have significant resources, advanced skills, and access to sophisticated tools and techniques.
- Insider Threats: Insider threats refer to individuals within an organization who misuse their authorized access or privileges for malicious purposes. This can include employees, contractors, or anyone with legitimate access to systems and data who abuses their privileges to steal information, sabotage systems, or compromise security.
Ethical Hackers (White Hat Hackers)

As outlined previously, while White Hat Hackers operate legally and ethically, as a result, they are also known as Ethical Hackers.
An Ethical Hacker locates weaknesses or vulnerabilities in computer and information systems using the same intent and actions of a malicious hacker but they do this at the request of the organisation with the intention of making systems and environments more secure.
To be an Ethical Hacker, you must have completed the CEHv10 Certification which is known as Certified Ethical Hacker.
Ethical hackers, utilize a variety of tools and technologies to identify vulnerabilities and strengthen the security of systems and networks. Here are some commonly used tools by ethical hackers and their purposes:
These tools scan systems, networks, or applications to identify known vulnerabilities. They help ethical hackers discover security weaknesses and potential entry points for unauthorized access.
- Nessus
- OpenVAS
- Qualys
Penetration testing tools simulate real-world attacks to test the security of systems. They help ethical hackers identify and exploit vulnerabilities, gaining insights into the potential impact and severity of security flaws.
- Metasploit Framework
- Burp Suit
- OWASP ZAP
Network scanning tools examine network infrastructure to identify open ports, devices, and services. They assist ethical hackers in mapping the network and identifying potential entry points or misconfigurations.
- Nmap
- Angry IP Scanner
- WiresharkAP
These tools attempt to crack passwords using various techniques such as brute force, dictionary attacks, or rainbow tables. Ethical hackers use them to test the strength of passwords and identify weak or easily guessable ones.
- John the Ripper
- Hashcat
- Hydra
Packet sniffing tools intercept and analyze network traffic, allowing ethical hackers to inspect the data being transmitted. They help in identifying vulnerabilities, detecting unauthorized activities, and analyzing network communication for potential security issues.
- Wireshark
- tcpdump
- Ettercap
Exploitation frameworks like Metasploit provide a collection of tools, exploits, and payloads to help ethical hackers test and exploit vulnerabilities. They streamline the process of launching attacks and demonstrate the potential impact of successful exploits.
- Metasploit Framework
- ExploitDB
- Core Impact
Forensic tools aid in the investigation and analysis of security incidents. They help ethical hackers gather evidence, examine logs, and reconstruct events to understand the nature of an attack and mitigate future risks.
- EnCase
- Autopsy
- Volatility
These tools specifically focus on assessing the security of web applications. They help ethical hackers identify common web application vulnerabilities such as SQL injection, cross-site scripting (XSS), or insecure direct object references.
- OWASP Zap
- Burp Suite
- Acunetix
Ethical hackers often use wireless network tools to assess the security of wireless networks. These tools can detect vulnerabilities, monitor network traffic, crack encryption keys, and identify weak configurations.
- Aircrack-ng
- Kismet
- Wi-Fi Pineapple
The Social Engineering Toolkit is a collection of tools that assist ethical hackers in carrying out social engineering attacks. It helps simulate phishing, credential harvesting, or other social engineering techniques to test the human element of security.
- SET Toolkit
- GoPhish
- Social-Engineer Toolkit (SET)
Ethical Hacking Process
To carry out a structured attack, Ethical Hacking is completed in phases.
- Reconnaissance: stage of gathering information: IP address, MAC address, OS used, which build/version, applications on top, versions of applications so I know what I am attacking.
- Scanning: Using the Nmap tool for example, if I am going to attack a server: I scan the open ports, open services, and protocols that are running on this server.
- Gaining access: probably through cracking passwords, or exploiting vulnerabilities during the scanning phase.
- Maintaining access: since the vulnerability may not be there for long, I have to maintain access: I install trojans or backdoor entries to get access secretly at my own will and on my own time as long as these devices are available on the network.
- Clear my track: for example, trojan install files/ directory on the device, I have to hide that because if the victim comes to know that there are traces, they will increase the security parameters so the victim doesn’t know he is compromised. And even if he is compromised, he can’t track the commission to the hacker. It consists of deleting any reference to IP addresses, or MAC addresses.
- Reporting: Examples: What attacks did we do? What was the outcome of the attack? A detailed analysis report is submitted to the management with steps, screenshots, evidence, the outcome of attacks, the expected outcome of attacks and the steps to mitigate these attacks.
