Securing the transmission of sensitive data is of paramount importance. SSL (Secure Sockets Layer) encryption plays a crucial role in safeguarding communication between clients and servers. In this topic, we will explore SSL encryption and its significance in securing cloud applications. Specifically, we will delve into AWS Certificate Manager (ACM), a service provided by Amazon Web Services (AWS), which simplifies the process of obtaining and managing SSL/TLS certificates. Let's take a closer look at the content covered in this topic:
- Securing your Cloud Application: We will begin by understanding the importance of SSL encryption in securing data transmitted over the internet. We will explore the underlying principles of SSL/TLS protocols and how they establish secure communication channels between clients (such as web browsers) and servers (such as web applications). We will also discuss the significance of encrypting sensitive data to protect it from unauthorised access.
- AWS Certificate Manager (ACM): ACM is a fully-managed service provided by AWS that simplifies the process of obtaining, deploying, and managing SSL/TLS certificates for your applications. We will explore the features and benefits of ACM, including its integration with other AWS services. ACM provides an easy and automated way to provision SSL/TLS certificates, eliminating the complexities associated with manual certificate management.
Throughout this topic, we will learn how to secure cloud applications using SSL encryption and explore the capabilities of AWS Certificate Manager. By the end of this section, you will have a comprehensive understanding of SSL encryption, its role in securing data transmission, and the practical implementation of SSL/TLS certificates using AWS Certificate Manager in your cloud applications.
In today's interconnected digital world, the transmission of data over the internet is ubiquitous. However, it also exposes sensitive information to potential threats and eavesdropping. Let’s take a look at the underpinning requirements of securing your could application through a review of the CIA Triad.
In the realm of cybersecurity, protecting sensitive information and maintaining the integrity of data is paramount. The fundamental concept that forms the basis of information security is the Triad of CIA (not to be confused with the Central Intelligence Agency):
- Confidentiality
- Integrity
- Availability
Watch the following video from Eye on Tech which further explains the CIA Triad:
By understanding and implementing the principles of the CIA Triad, individuals and organizations can establish robust security measures to safeguard their data and systems from unauthorized access, tampering, and disruptions. In this learning content, we will explore each element of the CIA Triad in detail and discuss how to achieve its objectives effectively.
These three elements are considered to be the most crucial elements of Cybersecurity. Let's review each component of the CIA Triad:
Confidentiality
Confidentiality refers to the protection of sensitive information from unauthorized disclosure. It ensures that only authorized individuals or entities have access to the data. Confidentiality measures aim to prevent data breaches, unauthorized data access, and information leakage.
Confidentiality can be achieved through the following mechanisms:
- Authentication with Authorization
- Encryption
Authentication Vs Authorization
Authentication and authorization are two distinct concepts in the realm of information security and access control. While they are closely related, they serve different purposes. Here's an overview of their differences:
Authentication:
Authentication is the process of verifying the identity of a user or entity attempting to access a system, application, or resource. It confirms whether the claimed identity is valid or not. Authentication is typically performed by presenting credentials such as usernames, passwords, or other authentication factors (e.g., biometrics, tokens) to a system. The purpose of authentication is to ensure that the user is who they claim to be.
Examples of authentication mechanisms include:
- Username and password: The user provides a unique username and a corresponding password to prove their identity.
- Two-factor authentication (2FA): In addition to a password, a second factor such as a fingerprint scan, SMS code, or authenticator app is required.
- Biometric authentication: This involves using unique physical characteristics like fingerprints, facial recognition, or iris scans to authenticate a user.
- Single sign-on (SSO): Users authenticate once, and subsequent authentication is automated across multiple systems or applications.
Authorization (Access Control):
Authorization, also referred to as access control, is the process of granting or denying permissions and privileges to authenticated users or entities. Once a user's identity is confirmed through authentication, authorization determines what actions they are allowed to perform and what resources they can access within a system or application. The purpose of authorization is to enforce restrictions and protect sensitive information from unauthorized access.
Authorization can be based on various factors such as user roles, group memberships, permissions, or access control lists (ACLs). It defines the level of access a user has, and it can be specified at a granular level to restrict certain operations or data.
Examples of authorization mechanisms include:
- Role-based access control (RBAC): Users are assigned roles, and permissions are associated with those roles. Users inherit the permissions of their assigned roles.
- Access control lists (ACLs): Individual permissions are assigned to specific users or groups for finer-grained control.
- Attribute-based access control (ABAC): Access decisions are based on a set of attributes about the user, resource, environment, and other contextual information.
- Mandatory access control (MAC): Access decisions are based on a predetermined security policy enforced by the system, typically used in high-security environments.
Confidentiality in Practice: Two-Factor Authentication
Online banking is commonplace across most segments of society and while traditionally the User IDs and passwords constitute standard procedure, to ensure confidentially and security, two-factor authentication (2FA) is becoming the norm.

ARE YOU THE PERSON YOU SAY YOU ARE? PROVE IT …..TWICE.
Two-factor authentication (2FA), also known as multi-factor authentication (MFA), is a security mechanism that adds an extra layer of protection to user accounts and systems. It requires users to provide two separate and distinct pieces of evidence to verify their identity, making it more difficult for unauthorized individuals to gain access. This provides a higher level of security than authentication methods that depend on single-factor authentication (SFA). 2FA is done by using two factors from the following categories:
- Something You Know: This factor refers to information that only the legitimate user should know, such as a password, a PIN, or the answer to a security question.
- Something You Have: This factor involves possessing a physical or digital device that is unique to the user, such as a mobile phone, a smart card, or a hardware token. This device generates a one-time code or receives a verification message that the user must provide during the authentication process.
- Something You Are: something physically inherent in the user like a fingerprint, facial, or voice recognition, or iris scan.
Case Study: ASB Online Banking Two-Factor Authentication

In 2004, ASB was the first bank in New Zealand to introduce the concept of two-factor authentication. Initially, 2FA was implemented for any transfer over the value of $2,500 NZD to a third-party account. Customers would receive an eight-digit text message which needed to be entered online within three minutes to complete the transaction.
The ASB two-factor authentication system ‘Netcode’ was developed using technology from the US firm RSA Security.
Since 2004, 2FA has come a long way and in 2018 ASB partnered with VIX Verify to roll out a new biometric-based mobile app that allows customers to remotely verify their identity by comparing a selfie with a photo of their eligible drivers' licence or passport.
Sources:
https://www.smh.com.au/national/nz-bank-adds-security-online-20041109-gdk2my.html
https://www.biometricupdate.com/201811/vix-verify-develops-biometric-mobile-id-app-for-asb-bank
Bimoteric Verification
Biometric verification is any means by which a person can be uniquely identified by evaluating one or more distinguishing biological traits. These biological identifiers include fingerprints, hand and earlobe geometries, retina patterns, voice prints and written signatures.
Common Types of Biometric Verification
- Facial recognition
- voice recognition
- fingerprint recognition
- iris scanners
- handwriting recognition
Other ways to keep data secure
- Applying Encryption to the data
- Security tokens, key fobs or soft tokens
- Users can take precautions to minimize the number of places where information appears
- Minimize the number of times data is transmitted to complete a transaction
Integrity
Integrity focuses on maintaining the accuracy, completeness, and reliability of data. It ensures that information remains unaltered and consistent throughout its lifecycle. Integrity measures aim to prevent unauthorized modifications, data corruption, and tampering.
THE DATA RECEIVED IS THE SAME AS IT WAS SENT (TRUSTWORTHY AND ACCURATE).
There are two points during the transmission process during which the integrity could be compromised:
- during the upload or transmission of data
- during the storage of the document in the database or collection
File permission and user access control ensures unauthorized people cannot change data, and checksum and backup save data from non-human threats such as electromagnetic pulse or server crashes.
Availability
Availability refers to ensuring that authorized users have timely and uninterrupted access to the information and resources they require. It involves mitigating the impact of disruptions, system failures, or malicious attacks that can hinder access to data or services.
For a system to demonstrate availability, it must have properly functioning computing systems, security controls and communication channels. Systems defined as critical (power generation, medical equipment, safety systems) often have extreme requirements related to availability.
Critical System Requirements
These systems must:
- be resilient against cyber threats
- have safeguards against power outages
- have safeguards against hardware failures
- mitigate other events that might impact the system's availability
Availability for critical systems is best ensured by rigorously maintaining all hardware and staying up to date with all system upgrade. Providing bandwidth, preventing bottlenecks and providing disaster recovery is essential.
Types of attacks that relate to the CIA Triad
What can unauthorized people do?
- Interception: This is an attack on confidentiality. An unauthorized party could be a person, a program or a computer
- Modification: An unauthorized party not only gains access to but tampers with an asset. This is an attack on integrity.
- Fabrication: An unauthorized party inserts counterfeit objects into the system. This is an attack on authenticity.
Best practices for implementing the CIA Triad:
This is where SSL (Secure Sockets Layer) encryption comes into play. SSL ensures the confidentiality, integrity, and authenticity (CIA Triad) of data exchanged between clients and servers, providing a secure communication channel. Let's delve into the details of SSL encryption and its significance in securing cloud applications.
Importance of SSL Encryption
The importance of SSL encryption lies in its ability to protect sensitive data during transmission. When users interact with cloud applications, they often share personal information, login credentials, financial details, or other sensitive data. Without proper encryption, this information can be intercepted and accessed by unauthorised individuals, compromising user privacy and data integrity. SSL encryption ensures that data is encrypted before transmission and can only be decrypted by the intended recipient, preventing eavesdropping and unauthorised access.
Underlying Principles of SSL/TLS Protocols
SSL/TLS protocols establish secure communication channels between clients (such as web browsers) and servers (such as web applications). These protocols use a combination of symmetric and asymmetric encryption, along with digital certificates, to achieve secure data transfer. The following are the key principles of SSL/TLS protocols:
- Encryption: SSL uses asymmetric encryption to securely exchange a session key, which is then used for symmetric encryption. This ensures that data transmitted between the client and server is encrypted and can only be decrypted by the intended recipient.
- Authentication: SSL provides a mechanism for authenticating the identity of the server using digital certificates. These certificates are issued by trusted Certificate Authorities (CAs) and validate that the server is legitimate, preventing man-in-the-middle attacks.
- Integrity: SSL employs cryptographic hash functions to ensure data integrity. This means that any tampering or modification of the transmitted data can be detected, ensuring the integrity and trustworthiness of the information.
Significance of Encrypting Sensitive Data
Encrypting sensitive data is essential to protect it from unauthorised access and maintain data confidentiality. When data is encrypted, it is transformed into an unreadable format that can only be deciphered using the correct decryption key. By encrypting sensitive data during transmission, even if it is intercepted by attackers, they will not be able to decipher the information without the encryption key. This provides an additional layer of protection and reduces the risk of data breaches. In the context of cloud applications, SSL encryption is crucial for securing data transmitted between users and the cloud environment. It ensures that sensitive information remains confidential, mitigates the risk of unauthorized access, and maintains the trust of users. Implementing SSL encryption in your cloud application helps to establish a secure communication channel and protect user data, enhancing the overall security posture of your application.
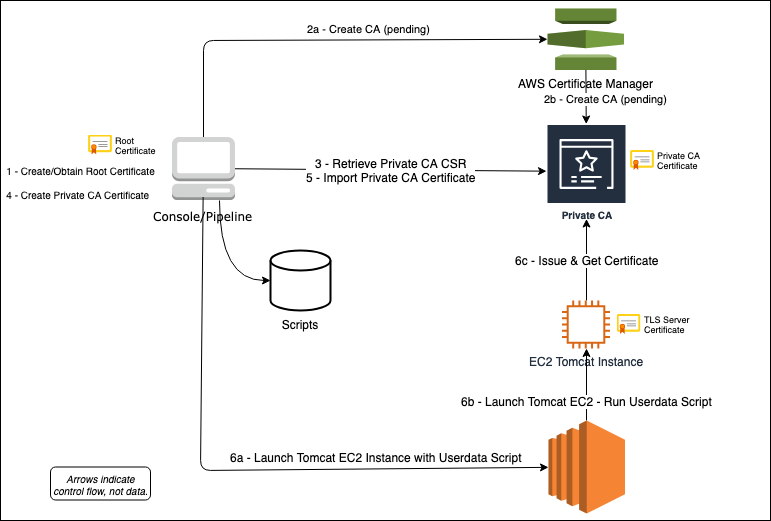
AWS Certificate Manager (ACM) is a fully-managed service offered by Amazon Web Services (AWS) that streamlines the process of obtaining, deploying, and managing SSL/TLS certificates for your applications. ACM simplifies the certificate management workflow by providing a convenient and automated solution.
Let's delve into the details of ACM, its features, benefits, and integration with other AWS services.
- Simplified Certificate Management: ACM eliminates the manual complexities associated with certificate management. It provides a centralised platform to request, deploy, and manage SSL/TLS certificates for your applications hosted on AWS. ACM handles certificate renewal and helps you stay up to date with the latest security standards without requiring manual intervention.
- Seamless Integration with AWS Services: ACM seamlessly integrates with various AWS services, making it easy to provision and manage certificates for your application deployments. It integrates particularly well with Elastic Load Balancers (ELBs), Amazon CloudFront, and Amazon API Gateway. This integration ensures that your applications can leverage ACM certificates without the need for additional configuration or manual certificate uploads.
- Automated Certificate Provisioning and Renewal: ACM streamlines the process of obtaining SSL/TLS certificates by automating the certificate provisioning and renewal tasks. It generates the necessary Certificate Signing Requests (CSRs) and handles the complex steps involved in certificate issuance, making the process fast and hassle-free. ACM also automates the renewal of certificates before they expire, ensuring continuous security without manual intervention.
- Certificate Visibility and Management: ACM provides a unified interface to view and manage all your certificates in one place. It offers visibility into the status and expiration dates of your certificates, allowing you to easily monitor and track their validity. Additionally, ACM offers features for tagging and organising certificates, simplifying the management of large-scale deployments with multiple certificates.
- Public and Private Certificates: ACM supports both public and private certificates. Public certificates can be used for securing websites, APIs, or any publicly accessible application. Private certificates, on the other hand, are used within a private network or Virtual Private Cloud (VPC) for internal communication. ACM allows you to manage and deploy both types of certificates seamlessly.
- Integration with AWS CloudFormation and AWS CLI: ACM can be easily integrated into your infrastructure deployment workflows using AWS CloudFormation templates or the AWS Command Line Interface (CLI). This enables you to automate the certificate provisioning process, making it more efficient and consistent across different environments and deployments.
By leveraging ACM, you can simplify and automate the process of obtaining, deploying, and managing SSL/TLS certificates for your applications. ACM provides a user-friendly interface, seamless integration with AWS services, and automated certificate provisioning and renewal. With ACM, you can focus on building and deploying your applications while leaving the complexities of certificate management to the service.
Link
Follow the link to find out more about AWS Certificate Manager:
Certificate Manager - AWS Certificate Manager - AWS (amazon.com)
